Slide 1
... To designate a file’s location, you must first specify the device where the file is stored – The main hard disk usually is referred to as Drive C A disk partition is a section of hard disk drive that is treated as a separate storage unit – Partitions can be assigned drive letters – Partitions ar ...
... To designate a file’s location, you must first specify the device where the file is stored – The main hard disk usually is referred to as Drive C A disk partition is a section of hard disk drive that is treated as a separate storage unit – Partitions can be assigned drive letters – Partitions ar ...
UNIX Operating System
... first starting with the target it is going to create. Make looks at each of the target’s dependencies to see if they are listed as targets. It follows the chain of dependencies until it reaches the end of the chain and then begins backing out and executing the commands found in each target's rule. A ...
... first starting with the target it is going to create. Make looks at each of the target’s dependencies to see if they are listed as targets. It follows the chain of dependencies until it reaches the end of the chain and then begins backing out and executing the commands found in each target's rule. A ...
PPT Chapter 13
... • MS-DOS uses a variant of linked allocation that stores the metadata separately from the file data • FAT has one element corresponding to every disk block in the disk – Penalty: FAT has to be accessed to obtain the address of the next disk block • Solution: FAT is held in memory during file process ...
... • MS-DOS uses a variant of linked allocation that stores the metadata separately from the file data • FAT has one element corresponding to every disk block in the disk – Penalty: FAT has to be accessed to obtain the address of the next disk block • Solution: FAT is held in memory during file process ...
Network File System
... VxWorks provides two local file systems appropriate for real-time used with block devices (disks): One is compatible with MS-DOS file systems and the other with the RT-11 file system. In VxWorks, the file system is not tied to a specific type of block device or its driver. VxWorks block device ...
... VxWorks provides two local file systems appropriate for real-time used with block devices (disks): One is compatible with MS-DOS file systems and the other with the RT-11 file system. In VxWorks, the file system is not tied to a specific type of block device or its driver. VxWorks block device ...
disk controller - Faculty Web Sites
... • RAID is arranged into six different levels • RAID schemes improve performance and improve the reliability of the storage system by storing redundant data ▫ Mirroring or shadowing (RAID 1) keeps duplicate of each disk ▫ Striped mirrors (RAID 1+0) or mirrored stripes (RAID 0+1) provides high perform ...
... • RAID is arranged into six different levels • RAID schemes improve performance and improve the reliability of the storage system by storing redundant data ▫ Mirroring or shadowing (RAID 1) keeps duplicate of each disk ▫ Striped mirrors (RAID 1+0) or mirrored stripes (RAID 0+1) provides high perform ...
File Systems
... – How many i-nodes should a file system have? – How many direct and indirect blocks should an i-node have? – What is the “right” block size? ...
... – How many i-nodes should a file system have? – How many direct and indirect blocks should an i-node have? – What is the “right” block size? ...
Operating Systems
... • The number in the brackets will change as you work. It is the “number” of the command that you are about to type. • If this prompt is not on the screen at any time, you are not communicating with the OS. UMBC CMSC 104, Section 0801 -- Fall 2002 ...
... • The number in the brackets will change as you work. It is the “number” of the command that you are about to type. • If this prompt is not on the screen at any time, you are not communicating with the OS. UMBC CMSC 104, Section 0801 -- Fall 2002 ...
File System
... treated as illegal file name (links become valid if another file/subdirectory with the same name is created) ...
... treated as illegal file name (links become valid if another file/subdirectory with the same name is created) ...
Integrated End-to-End Dependability in the Loris Storage Stack,
... base system), resource isolation, and the potential to checkpoint/restart and migrate environments [16]. 1) The naming layer: The Loris naming layer is part of the MEE. This has two main advantages. First, this allows a MEE (and thus its applications) to choose its own, private naming scheme. The ca ...
... base system), resource isolation, and the potential to checkpoint/restart and migrate environments [16]. 1) The naming layer: The Loris naming layer is part of the MEE. This has two main advantages. First, this allows a MEE (and thus its applications) to choose its own, private naming scheme. The ca ...
Quick UNIX Tutorial
... Getting help while on the system The shell Working with files & directories Wild card characters ...
... Getting help while on the system The shell Working with files & directories Wild card characters ...
Modern Operating System by Tanenbaum
... Question 20: If a page is shared between two processes, is it possible that the page is read-only for one process and read-write for the other? Why or why not? Answer: If pages can be shared, yes. For example, if two users of a timesharing system are running the same editor at the same time and the ...
... Question 20: If a page is shared between two processes, is it possible that the page is read-only for one process and read-write for the other? Why or why not? Answer: If pages can be shared, yes. For example, if two users of a timesharing system are running the same editor at the same time and the ...
... Seek 200 Kbytes and repeat the pattern. This again is a typical application behavior for applications that have data structures contained within a file and is accessing a particular region of the data structure. Most operating systems do not detect this behavior or implement any techniques to enhan ...
Slides
... File Structure None - sequence of words, bytes Simple record structure Lines Fixed length Variable length ...
... File Structure None - sequence of words, bytes Simple record structure Lines Fixed length Variable length ...
Transparency in Distributed Systems
... which are physically distant apart and a single set of operations should be provided to access these remote as well as the local files. Applications written for the local file should be able to be executed even for the remote files. The examples illustrating this property are the File system in Netw ...
... which are physically distant apart and a single set of operations should be provided to access these remote as well as the local files. Applications written for the local file should be able to be executed even for the remote files. The examples illustrating this property are the File system in Netw ...
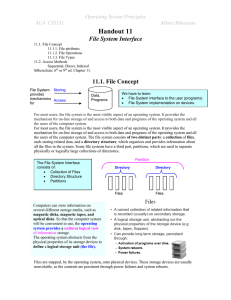
H 10.1. File-System Interface
... Type: This information is needed for those systems that support different types. Size: The current size of the file (in bytes, words, or blocks), and possibly the maximum allowed size are included in this attribute. Protection: Access-control information determines who can do reading, writing, execu ...
... Type: This information is needed for those systems that support different types. Size: The current size of the file (in bytes, words, or blocks), and possibly the maximum allowed size are included in this attribute. Protection: Access-control information determines who can do reading, writing, execu ...
Files and File Systems • files: persistent, named data objects – data
... Links and Multiple File Systems • hard links cannot cross file system boundaries – each hard link maps a name to an i-number, which is unique only within a file system • for example, even after the mount operation illustrated on the previous slide, link(/x/a/x/g,/z/d) would result in an error, becau ...
... Links and Multiple File Systems • hard links cannot cross file system boundaries – each hard link maps a name to an i-number, which is unique only within a file system • for example, even after the mount operation illustrated on the previous slide, link(/x/a/x/g,/z/d) would result in an error, becau ...
Chapter 10 File System Interface
... of bytes is allocated to it 2) Write – add data to file; usually OpSys maintains writepointer (wp) and data is written to current wp. Call minimally specifies buffer containing data to be written, file ID, sometimes more. 3) Read – read data from file; usually OpSys maintains readpointer (rp) an ...
... of bytes is allocated to it 2) Write – add data to file; usually OpSys maintains writepointer (wp) and data is written to current wp. Call minimally specifies buffer containing data to be written, file ID, sometimes more. 3) Read – read data from file; usually OpSys maintains readpointer (rp) an ...
Ch 1 Getting Started with the Operating System
... Built into command processor Automatically loaded/stored in ...
... Built into command processor Automatically loaded/stored in ...
Slide Set 7
... Fully Buffered: I/O takes place when a buffer is full. Disk files are normally fully buffered. The buffer is allocated by the I/O library itself by doing a malloc. Line Buffered: I/O takes place when a new line character is encountered. Line buffering is used for terminal I/O. Note that I/O may take ...
... Fully Buffered: I/O takes place when a buffer is full. Disk files are normally fully buffered. The buffer is allocated by the I/O library itself by doing a malloc. Line Buffered: I/O takes place when a new line character is encountered. Line buffering is used for terminal I/O. Note that I/O may take ...
Linux Tutorial
... This implies that you may read files in the directory if you have read permission on the individual files. example: ...
... This implies that you may read files in the directory if you have read permission on the individual files. example: ...
Presentation
... • With a new system called large block allocation (LBA), it is now possible to make file systems much larger than 512 MB under MS-DOS • LBA translates larger logical blocks to smaller ones for support of larger physical disks • However, the disk controller and disk must support LBA, and they must be ...
... • With a new system called large block allocation (LBA), it is now possible to make file systems much larger than 512 MB under MS-DOS • LBA translates larger logical blocks to smaller ones for support of larger physical disks • However, the disk controller and disk must support LBA, and they must be ...
UNIX Notes:
... have POSIX compliant kernels. Popular Linux OS distributions include: Ubuntu, Fedora, Cygwin, UWin, GNU-win, Debian, Redhat, Knoppix, DSL, Gentu, TinyCore, and MSys. Since it started more than 50 years ago, UNIX has grown and changed in a different way from most operating systems. Many early UNIX us ...
... have POSIX compliant kernels. Popular Linux OS distributions include: Ubuntu, Fedora, Cygwin, UWin, GNU-win, Debian, Redhat, Knoppix, DSL, Gentu, TinyCore, and MSys. Since it started more than 50 years ago, UNIX has grown and changed in a different way from most operating systems. Many early UNIX us ...
UNIX Notes:
... have POSIX compliant kernels. Popular Linux OS distributions include: GNU, Ubuntu, Fedora, Debian, Redhat, Knoppix, Puppy, DSL, Gentu, Cygwin, and TinyCore. Since it started more than 50 years ago, UNIX has grown and changed in a different way from most operating systems. Many early UNIX users were ...
... have POSIX compliant kernels. Popular Linux OS distributions include: GNU, Ubuntu, Fedora, Debian, Redhat, Knoppix, Puppy, DSL, Gentu, Cygwin, and TinyCore. Since it started more than 50 years ago, UNIX has grown and changed in a different way from most operating systems. Many early UNIX users were ...