Introduction to Operating Systems
... Unix rewritten in C programming language (1974) Unix utility programs written by students at colleges and universities (continues today) Unix used to share research and data (foundation of the Internet and the WWW) Linus Torvalds orchestrated development of an operating system based on Unix, but abl ...
... Unix rewritten in C programming language (1974) Unix utility programs written by students at colleges and universities (continues today) Unix used to share research and data (foundation of the Internet and the WWW) Linus Torvalds orchestrated development of an operating system based on Unix, but abl ...
SELinux For Dummies - LinuxFest Northwest 2015
... This might cause some confusion, but this works the same way as with discretionary access control. The cp command acts a little differently. If a file exists that you are copying over, the new file will maintain the file context of the previous file. If the file does not exist, it will either get th ...
... This might cause some confusion, but this works the same way as with discretionary access control. The cp command acts a little differently. If a file exists that you are copying over, the new file will maintain the file context of the previous file. If the file does not exist, it will either get th ...
Proceedings of the 5th Symposium on Operating Systems Design and Implementation USENIX Association
... classes. Also, users can use the same machine to run different capsules for different tasks. They can have a single customized capsule each for personal use, and multiple work capsules which are centrally updated by system administrators. The capsule technique also causes less disruption since old c ...
... classes. Also, users can use the same machine to run different capsules for different tasks. They can have a single customized capsule each for personal use, and multiple work capsules which are centrally updated by system administrators. The capsule technique also causes less disruption since old c ...
Optimizing the Migration of Virtual Computers
... classes. Also, users can use the same machine to run different capsules for different tasks. They can have a single customized capsule each for personal use, and multiple work capsules which are centrally updated by system administrators. The capsule technique also causes less disruption since old c ...
... classes. Also, users can use the same machine to run different capsules for different tasks. They can have a single customized capsule each for personal use, and multiple work capsules which are centrally updated by system administrators. The capsule technique also causes less disruption since old c ...
File System
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the ...
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the ...
Document
... 11. Explain the facilities provided by the following operating system 12. List out the services provided by operating systems to programs and to the 13. Define operating system and list out the function and component of operating system. 14. Explain in detail the modern computer system 15. Explain t ...
... 11. Explain the facilities provided by the following operating system 12. List out the services provided by operating systems to programs and to the 13. Define operating system and list out the function and component of operating system. 14. Explain in detail the modern computer system 15. Explain t ...
No Slide Title
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the ...
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the ...
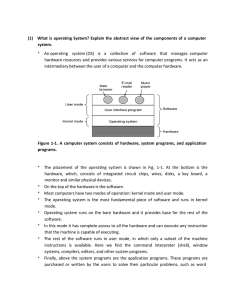
(1) What is operating System? Explain the abstract view of the
... (2) Give the view of OS as an extended machine. Operating systems perform two basically unrelated functions: providing a clean abstract set of resources instead of the messy hardware to application programmers and managing these hardware resources. Let us now look at both. Operating System as an Ext ...
... (2) Give the view of OS as an extended machine. Operating systems perform two basically unrelated functions: providing a clean abstract set of resources instead of the messy hardware to application programmers and managing these hardware resources. Let us now look at both. Operating System as an Ext ...
ch22
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the ...
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the ...
What is a file system? - Montana State University
... Another layer of indirection • Multics, Unix, Minux, and Linux originally supported only one file system. – They only understood one type of layout on disk for directories and files. – Because of its origins, Linux initially supported just the Minix file system. • Limited to small partitions and sh ...
... Another layer of indirection • Multics, Unix, Minux, and Linux originally supported only one file system. – They only understood one type of layout on disk for directories and files. – Because of its origins, Linux initially supported just the Minix file system. • Limited to small partitions and sh ...
Process Management (Cont.)
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash. The log is stored in the third metadata file at the beginning of the ...
... recovered after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash. The log is stored in the third metadata file at the beginning of the ...
Appendix C: Windows 2000
... To compress a file, NTFS divides the file’s data into compression units, ...
... To compress a file, NTFS divides the file’s data into compression units, ...
PPT - EazyNotes
... after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the volume The logging functionality is provided by the 2000 log file service ...
... after a crash, just that the file system data structures (the metadata files) are undamaged and reflect some consistent state prior to the crash The log is stored in the third metadata file at the beginning of the volume The logging functionality is provided by the 2000 log file service ...
2005-03-midterm.pdf
... As a virtual machine, an operating system provides an abstraction over the hardware by means of, for example, system calls. In this way, it provides a convenient way to program a machine without the need to know about hardware details. As a resource manager, it allows multiple processes (or users) t ...
... As a virtual machine, an operating system provides an abstraction over the hardware by means of, for example, system calls. In this way, it provides a convenient way to program a machine without the need to know about hardware details. As a resource manager, it allows multiple processes (or users) t ...
the linux operating system
... that runs as a single process with a single address space. All the functional components of the kernel have access to all of its internal data structures and routines. If changes are made to any portion of a typical monolithic OS, all the modules and routines must be relinked and reinstalled and the ...
... that runs as a single process with a single address space. All the functional components of the kernel have access to all of its internal data structures and routines. If changes are made to any portion of a typical monolithic OS, all the modules and routines must be relinked and reinstalled and the ...
ppt
... Credentials - Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personality - Not traditionally found on UNIX systems, but under Linux each process has an associated personality identifier that can slig ...
... Credentials - Each process must have an associated user ID and one or more group IDs that determine the process’s rights to access system resources and files Personality - Not traditionally found on UNIX systems, but under Linux each process has an associated personality identifier that can slig ...
Post Graduate Diploma in Computer Application
... Let us begin with the word ‘compute’. It means ‘to calculate’. We all are familiar with calculations in our day-to-day life. We apply mathematical operations like addition, subtraction, multiplication, etc. and many other formulae for calculations. Simpler calculations take less time. But complex ca ...
... Let us begin with the word ‘compute’. It means ‘to calculate’. We all are familiar with calculations in our day-to-day life. We apply mathematical operations like addition, subtraction, multiplication, etc. and many other formulae for calculations. Simpler calculations take less time. But complex ca ...
an introduction to solaris
... Sun’s UNIX operating environment began life as a port of BSD UNIX to the Sun-1 workstation. The early versions of Sun’s UNIX were known as SunOS, which is the name used for the core operating system component of Solaris. SunOS 1.0 was based on a port of BSD 4.1 from Berkeley labs in 1982. At that ti ...
... Sun’s UNIX operating environment began life as a port of BSD UNIX to the Sun-1 workstation. The early versions of Sun’s UNIX were known as SunOS, which is the name used for the core operating system component of Solaris. SunOS 1.0 was based on a port of BSD 4.1 from Berkeley labs in 1982. At that ti ...
OPERATING SYSTEM : AN OVERVIEW – [UNIT
... operating system of each of the interconnected computers must contain, in addition to its own stand-alone functionality, provisions for handing communication and transfer of program and data among the other computers with which it is connected. Network operating systems are not fundamentally differe ...
... operating system of each of the interconnected computers must contain, in addition to its own stand-alone functionality, provisions for handing communication and transfer of program and data among the other computers with which it is connected. Network operating systems are not fundamentally differe ...
No Slide Title
... Object names are structured like file path names in MSDOS and UNIX. 2000 implements a symbolic link object, which is similar to symbolic links in UNIX that allow multiple nicknames or aliases to refer to the same file. A process gets an object handle by creating an object by opening an existing one, ...
... Object names are structured like file path names in MSDOS and UNIX. 2000 implements a symbolic link object, which is similar to symbolic links in UNIX that allow multiple nicknames or aliases to refer to the same file. A process gets an object handle by creating an object by opening an existing one, ...
ch22
... Object names are structured like file path names in MS-DOS and UNIX. XP implements a symbolic link object, which is similar to symbolic links in UNIX that allow multiple nicknames or aliases to refer to the same file. A process gets an object handle by creating an object by opening an existing one, ...
... Object names are structured like file path names in MS-DOS and UNIX. XP implements a symbolic link object, which is similar to symbolic links in UNIX that allow multiple nicknames or aliases to refer to the same file. A process gets an object handle by creating an object by opening an existing one, ...
Software I: Utilities and Internals
... resources such as CPU time, memory and I/O devices). • UNIX includes: – kernel – tools, including compilers, editors, etc. – shell, which includes its own programming language ...
... resources such as CPU time, memory and I/O devices). • UNIX includes: – kernel – tools, including compilers, editors, etc. – shell, which includes its own programming language ...
lecture1423726024
... Network types are based on the distance between the nodes such as LAN (within a room, floor or building) and WAN (between buildings, cities or countries). The advantages of distributed system are resource sharing, computation speed up, reliability, communication. 5. Real time Systems: Real time syst ...
... Network types are based on the distance between the nodes such as LAN (within a room, floor or building) and WAN (between buildings, cities or countries). The advantages of distributed system are resource sharing, computation speed up, reliability, communication. 5. Real time Systems: Real time syst ...