Fast Root Cause Analysis on Distributed Systems by Composing
... each component class of the system. This means that if a system is composed of 1000 components of the same type, only a single compilation for the component would be required, leveraging the fact that most complex systems have a large number of replicated components. In order to include connections ...
... each component class of the system. This means that if a system is composed of 1000 components of the same type, only a single compilation for the component would be required, leveraging the fact that most complex systems have a large number of replicated components. In order to include connections ...
Dynamic Control of Coding for Progressive Packet Arrivals in DTNs
... • In this context, contacts between DTN nodes may be rare, for instance due to low densities of active nodes, so that the design of routing strategies is a core step to permit timely delivery of information to a certain destination with high probability. • When mobility is random, i.e., cannot be kn ...
... • In this context, contacts between DTN nodes may be rare, for instance due to low densities of active nodes, so that the design of routing strategies is a core step to permit timely delivery of information to a certain destination with high probability. • When mobility is random, i.e., cannot be kn ...
Network tomography via network coding
... directly extended to the problem of determining dynamic network properties, such as packet delays incurred at each node and link. We then consider the problem of actively estimating network topology in the presence of a malicious Byzantine adversary who wishes to disrupt the estimation process. For ...
... directly extended to the problem of determining dynamic network properties, such as packet delays incurred at each node and link. We then consider the problem of actively estimating network topology in the presence of a malicious Byzantine adversary who wishes to disrupt the estimation process. For ...
Network Information
... historical buildings manufacturing environments – no cables real time inventory – walking around PDA - personal digital assistants Interference with other wireless users Not even a plug in option ...
... historical buildings manufacturing environments – no cables real time inventory – walking around PDA - personal digital assistants Interference with other wireless users Not even a plug in option ...
Titles and Abstracts
... origin in the melding of the Quantum Inverse Scattering Method and Bethe ansatz techniques. This approach can be complicated and difficult to implement. In some instances an ability to extend the exact solutions to the most general Hamiltonians to which they are applicable is outside the scope of su ...
... origin in the melding of the Quantum Inverse Scattering Method and Bethe ansatz techniques. This approach can be complicated and difficult to implement. In some instances an ability to extend the exact solutions to the most general Hamiltonians to which they are applicable is outside the scope of su ...
KK14 - smk negeri 2 kediri
... conditions. For example, devices that have been damaged, then restored after it is used again, but at the time it is used again, should be monitored because of their performance even though he was functioning, but their performance will not be as effective as new condition. ...
... conditions. For example, devices that have been damaged, then restored after it is used again, but at the time it is used again, should be monitored because of their performance even though he was functioning, but their performance will not be as effective as new condition. ...
ICS 271 Fall 2014 Instructor : Kalev Kask
... by a depth-fist search with depth bound equal to d? (c) What is the minimum and maximum number of nodes that might be generated by a depth-first iterative-deepening search? (Assume that you start with an initial depth limit of 1 and increment the depth limit by 1 each time no goal is found within th ...
... by a depth-fist search with depth bound equal to d? (c) What is the minimum and maximum number of nodes that might be generated by a depth-first iterative-deepening search? (Assume that you start with an initial depth limit of 1 and increment the depth limit by 1 each time no goal is found within th ...
Topology-Aware Overlay Construction and Server Selection
... Aims much less structured overlay such as Gnutella, Freenet Focusing on the following general problem in unstructured overlays: “Given a set of n nodes on the Internet, have each node picks any k neighbor nodes from this set so that the average routing latency on the resultant overlay is low” ...
... Aims much less structured overlay such as Gnutella, Freenet Focusing on the following general problem in unstructured overlays: “Given a set of n nodes on the Internet, have each node picks any k neighbor nodes from this set so that the average routing latency on the resultant overlay is low” ...
PP slides
... - Many assumptions required for mathematical tractability - Typically, one function at a time is all that can be represented mathematically ; hence many coupled relationships may be required to completely describe ad hoc networks - In many areas, these analytic relationships do not exist • Discrete ...
... - Many assumptions required for mathematical tractability - Typically, one function at a time is all that can be represented mathematically ; hence many coupled relationships may be required to completely describe ad hoc networks - In many areas, these analytic relationships do not exist • Discrete ...
Hot Sticky Random Multipath
... know all utility functions impractical for large number of sources we’ll see: congestion control as distributed asynchronous algorithms to solve this problem ...
... know all utility functions impractical for large number of sources we’ll see: congestion control as distributed asynchronous algorithms to solve this problem ...
Proof-based formal methods for WSN development
... laboratory testbed techniques are the main approaches to analyse and evaluate the correctness and performance of network algorithms and protocols [3]. However, since WSNs have been applied to safety-critical application domains from healthcare to military applications, the high-level abstraction and ...
... laboratory testbed techniques are the main approaches to analyse and evaluate the correctness and performance of network algorithms and protocols [3]. However, since WSNs have been applied to safety-critical application domains from healthcare to military applications, the high-level abstraction and ...
The Complexity of Channel Scheduling in Multi-Radio Multi
... National University of Defense technology ...
... National University of Defense technology ...
NETADIS Research Project Overview The first list below gives the
... Title: Inference of regulatory controls in biochemical reaction networks Research Objectives: This project will study inference of regulatory controls in biochemical reaction networks, most notably in genome-scale reconstructions of cellular metabolism (where the interacting units are genes coding f ...
... Title: Inference of regulatory controls in biochemical reaction networks Research Objectives: This project will study inference of regulatory controls in biochemical reaction networks, most notably in genome-scale reconstructions of cellular metabolism (where the interacting units are genes coding f ...
slides - Duke Workshop on Sensing and Analysis of High
... – There are some 20 AT&T-like large transit providers in today’s Internet ...
... – There are some 20 AT&T-like large transit providers in today’s Internet ...
PPT Version
... Description of WG 1/3 The NEMO Working Group is concerned with managing the mobility of an entire network, viewed as a single unit, which changes its point of attachment to the Internet and thus its reachability in the topology. The mobile network is moving as a unit, and includes one or more mobil ...
... Description of WG 1/3 The NEMO Working Group is concerned with managing the mobility of an entire network, viewed as a single unit, which changes its point of attachment to the Internet and thus its reachability in the topology. The mobile network is moving as a unit, and includes one or more mobil ...
CS 151, Written Homework, Week 5, Solutions
... (e) Write down an expression for P(X,Z|Y ). P(X,Y,Z) = P(X,Z|Y)P(Y) P(X,Z|Y) = P(X,Y,Z)/P(Y) = P(X)P(Y|X)P(Z|Y)/P(Y) note that P(Y|X) = P(X|Y)P(Y) / P(X) so P(X,Z|Y) = P(X|Y)P(Z|Y) (f) Based on the expression in (e), and the definition of conditional independence, are X and Z conditionally independe ...
... (e) Write down an expression for P(X,Z|Y ). P(X,Y,Z) = P(X,Z|Y)P(Y) P(X,Z|Y) = P(X,Y,Z)/P(Y) = P(X)P(Y|X)P(Z|Y)/P(Y) note that P(Y|X) = P(X|Y)P(Y) / P(X) so P(X,Z|Y) = P(X|Y)P(Z|Y) (f) Based on the expression in (e), and the definition of conditional independence, are X and Z conditionally independe ...
Offense - Northwestern Networks Group
... They are basically stalling the problem and not fixing it. They would have to upgrade anyways because of newer technologies and higher data rate. ...
... They are basically stalling the problem and not fixing it. They would have to upgrade anyways because of newer technologies and higher data rate. ...
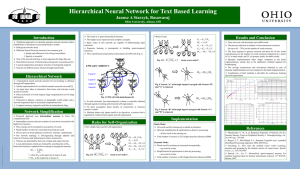
Application of Artificial Neural Network in Fluid Mechanics Teaching Evaluation System
... hidden nodes in the hidden layer. It can capture the pattern in the data. So the hidden layer and nodes play very important roles in the network architecture. Most studies indicate that a single hidden layer network tends to be used to the modeling problem and if the number of hidden nodes is enough ...
... hidden nodes in the hidden layer. It can capture the pattern in the data. So the hidden layer and nodes play very important roles in the network architecture. Most studies indicate that a single hidden layer network tends to be used to the modeling problem and if the number of hidden nodes is enough ...
KDSM_Ozegovic_v3
... •new optimization and adaptation possibilities Collision memory effect, occurring in DCF-type networks and causing throughput decrease, has been detected •CPCF mechanism, used for limiting this effect, has been ...
... •new optimization and adaptation possibilities Collision memory effect, occurring in DCF-type networks and causing throughput decrease, has been detected •CPCF mechanism, used for limiting this effect, has been ...
LAN topologies
... can still function if one segment goes bad. In a bus or ring topology, a bad segment can bring down the entire network. Most networks are a hybrid of the three types. A network's logical topology does not have to match its physical topology. For example, in most token ring networks the network may b ...
... can still function if one segment goes bad. In a bus or ring topology, a bad segment can bring down the entire network. Most networks are a hybrid of the three types. A network's logical topology does not have to match its physical topology. For example, in most token ring networks the network may b ...
we show that the performance gains obtained by jointly optimizing
... In this paper, we first study the optimal joint configuration of routing, access probability, and transmission rate parameters in slotted ALOHA fixed wireless networks to maximize the minimum throughput of the flows under an interference model based on SINR.In this paper, we study a simple MAC proto ...
... In this paper, we first study the optimal joint configuration of routing, access probability, and transmission rate parameters in slotted ALOHA fixed wireless networks to maximize the minimum throughput of the flows under an interference model based on SINR.In this paper, we study a simple MAC proto ...
Network science

Network science is an academic field which studies complex networks such as telecommunication networks, computer networks, biological networks, cognitive and semantic networks, and social networks, considering distinct elements or actors represented by nodes (or vertices) and the connections between the elements or actors as links (or edges). The field draws on theories and methods including graph theory from mathematics, statistical mechanics from physics, data mining and information visualization from computer science, inferential modeling from statistics, and social structure from sociology. The United States National Research Council defines network science as ""the study of network representations of physical, biological, and social phenomena leading to predictive models of these phenomena.""