pptx
... • Memex (thinking machine): Vannevar Bush (1945) • Galactic Network: J.C. R. Licklider (1962) - First Head of DARPA computer research ...
... • Memex (thinking machine): Vannevar Bush (1945) • Galactic Network: J.C. R. Licklider (1962) - First Head of DARPA computer research ...
投影片 1 - sigcomm
... • Goal: avoid rollbacks by selecting ordering likely to happen anyway – Events separated by long period will fall into different groups which means ordering is easy – Problem: some failure events are correlated • E.g., multiple overlay links sharing same physical link ...
... • Goal: avoid rollbacks by selecting ordering likely to happen anyway – Events separated by long period will fall into different groups which means ordering is easy – Problem: some failure events are correlated • E.g., multiple overlay links sharing same physical link ...
Network Analysis in the Social Sciences REVIEW
... For example, the typology shown in Fig. 3 divides dyadic relations into four basic types—similarities, social relations, interactions, and flows. Much of social network research can be seen as working out how these different kinds of ties affect each other. The importance of structure. As in the stu ...
... For example, the typology shown in Fig. 3 divides dyadic relations into four basic types—similarities, social relations, interactions, and flows. Much of social network research can be seen as working out how these different kinds of ties affect each other. The importance of structure. As in the stu ...
What is a Network Topology? The physical topology of a network
... Main Types of Physical Topologies Ring Topology In a ring topology, all nodes (file server, workstations, and peripherals) are connected to each other in a ring. This is called daisy-chaining. Each node on the ring acts as a repeater. It receives a transmission from the previous node, amplifies it t ...
... Main Types of Physical Topologies Ring Topology In a ring topology, all nodes (file server, workstations, and peripherals) are connected to each other in a ring. This is called daisy-chaining. Each node on the ring acts as a repeater. It receives a transmission from the previous node, amplifies it t ...
Document
... server> – Assumption: The IP address of a DNS server of a domain is relatively static ...
... server> – Assumption: The IP address of a DNS server of a domain is relatively static ...
The-assignment
... value of one and the other n-1 arcs of a flow value of zero (all nonbasic arcs receive flows of 0). Therefore each basis solution is highly degenerate ( i.e contains a large number of zero flows on basic arcs ...
... value of one and the other n-1 arcs of a flow value of zero (all nonbasic arcs receive flows of 0). Therefore each basis solution is highly degenerate ( i.e contains a large number of zero flows on basic arcs ...
Network Analysis in the Social Sciences
... For example, the typology shown in Fig. 3 divides dyadic relations into four basic types—similarities, social relations, interactions, and flows. Much of social network research can be seen as working out how these different kinds of ties affect each other. The importance of structure. As in the stu ...
... For example, the typology shown in Fig. 3 divides dyadic relations into four basic types—similarities, social relations, interactions, and flows. Much of social network research can be seen as working out how these different kinds of ties affect each other. The importance of structure. As in the stu ...
Sybex CCENT 100-101 Chapter 5
... From the Command window, ping the IP address of the local host If that’s successful, your network interface card (NIC) is functioning. If it fails, there is a problem with the NIC. Success here doesn’t just mean that a cable is plugged into the NIC, only that the IP protocol stack on the host can co ...
... From the Command window, ping the IP address of the local host If that’s successful, your network interface card (NIC) is functioning. If it fails, there is a problem with the NIC. Success here doesn’t just mean that a cable is plugged into the NIC, only that the IP protocol stack on the host can co ...
MaxFlow.pdf
... Previous max-flow algorithms have come at the problem one edge, or path, at a time, Kelner says. So for example, when sending items from node A to node B, the algorithms would transmit some of the goods down one path, until they reached its maximum capacity, and then begin sending some down the next ...
... Previous max-flow algorithms have come at the problem one edge, or path, at a time, Kelner says. So for example, when sending items from node A to node B, the algorithms would transmit some of the goods down one path, until they reached its maximum capacity, and then begin sending some down the next ...
Convergence Properties of the Degree Distribution of Some
... of edges to be sent out every time. They do this by saying that each node has m out-links, which they carefully keep track of. In step t + 1 the ith out-link is uniformly attached by probability p, and with probability 1 − p, the ith out-link of the chosen node is “copied” as above. Such a model can ...
... of edges to be sent out every time. They do this by saying that each node has m out-links, which they carefully keep track of. In step t + 1 the ith out-link is uniformly attached by probability p, and with probability 1 − p, the ith out-link of the chosen node is “copied” as above. Such a model can ...
PPT - P2
... • Despite ~25 years of research, no abstractions have emerged to modularize the problem. • I find this astonishing. Can ...
... • Despite ~25 years of research, no abstractions have emerged to modularize the problem. • I find this astonishing. Can ...
Challenges in modern HPC network design
... About HPC-Technology Development Group • Our group works in the area of high performance network design: From conceptualization to product: covering multiple aspects of hardware, software development, integration and deployment aspects • Last several years, the group has been developing high speed ...
... About HPC-Technology Development Group • Our group works in the area of high performance network design: From conceptualization to product: covering multiple aspects of hardware, software development, integration and deployment aspects • Last several years, the group has been developing high speed ...
Theorem 1
... Let M = {Mij} be the corresponding transfer matrix relating the set of input nodes to the set of output nodes. The network problem (G,C) is solvable if and only if there exists an assignment of numbers to ξ such that, • Mi,j = 0 for all pairs (vi, vj) of vertices such that (vi, vj ,X (vi, vj)) C • I ...
... Let M = {Mij} be the corresponding transfer matrix relating the set of input nodes to the set of output nodes. The network problem (G,C) is solvable if and only if there exists an assignment of numbers to ξ such that, • Mi,j = 0 for all pairs (vi, vj) of vertices such that (vi, vj ,X (vi, vj)) C • I ...
Local Area Network
... Mesh Topology Merits Demerits • No congestion • Cable length problem • Impractical for large • No MAC protocols networks are needed • More Secure • It is Robust • Fault identification is easy ...
... Mesh Topology Merits Demerits • No congestion • Cable length problem • Impractical for large • No MAC protocols networks are needed • More Secure • It is Robust • Fault identification is easy ...
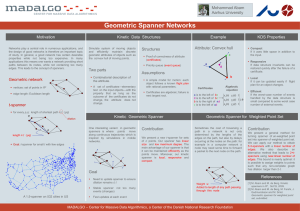
Geometric spanner for weighted point set, submitted.
... We present a general method for turning spanner of un-weighted point set into spanner of weighted point set. We can apply our method to obtain 5+t-spanners with a linear number of edges. We also describe an alternative method that leads to 2+tspanners using near-linear number of edges. This bound is ...
... We present a general method for turning spanner of un-weighted point set into spanner of weighted point set. We can apply our method to obtain 5+t-spanners with a linear number of edges. We also describe an alternative method that leads to 2+tspanners using near-linear number of edges. This bound is ...
Maximal covering with network survivability requirements in wireless
... feet, so 6930 feet is used for the maximum distance for Wi-Fi point to point interconnection (W) The required number of Wi-Fi routers (p) is specified to be in the range of 8–29. It is assumed that 20% of Wi-Fi routers satisfy the required number of wired connections to existing central offices (q). ...
... feet, so 6930 feet is used for the maximum distance for Wi-Fi point to point interconnection (W) The required number of Wi-Fi routers (p) is specified to be in the range of 8–29. It is assumed that 20% of Wi-Fi routers satisfy the required number of wired connections to existing central offices (q). ...
Advanced Computer Networks cs538, Fall 2014 @ UIUC
... • Identify endpoints of a connection (“association”) • Rejected design: • connection at host level • packet may include bytes for multiple processes ...
... • Identify endpoints of a connection (“association”) • Rejected design: • connection at host level • packet may include bytes for multiple processes ...
Theoretical Result: References: II: Improving the Basic Model (BMS)
... -> network level understanding of the system behaviour; -> weak form of initial conditions sensitivity due to the presence of the sharp spiking threshold ...
... -> network level understanding of the system behaviour; -> weak form of initial conditions sensitivity due to the presence of the sharp spiking threshold ...
RailTel - akwl.org
... Railtel has exclusive right of way along railway track giving it a freedom to establish OFC network promptly as per need. ...
... Railtel has exclusive right of way along railway track giving it a freedom to establish OFC network promptly as per need. ...
WT8266-S1 FAQ Forum: bbs.wireless-tag.com
... joined the router through network cable. The module connect with the ...
... joined the router through network cable. The module connect with the ...
Association Rule Mining in Peer-to
... Resource sharing with other applications Frequent failure and recovery of resources. ...
... Resource sharing with other applications Frequent failure and recovery of resources. ...
Chapter5
... together, so we need to create a VLSM network that will save address space. Looks like we have two block sizes of 32, a block size of 16, and a block size of 8, and our WANs each have a block size of 4. ...
... together, so we need to create a VLSM network that will save address space. Looks like we have two block sizes of 32, a block size of 16, and a block size of 8, and our WANs each have a block size of 4. ...
Network science

Network science is an academic field which studies complex networks such as telecommunication networks, computer networks, biological networks, cognitive and semantic networks, and social networks, considering distinct elements or actors represented by nodes (or vertices) and the connections between the elements or actors as links (or edges). The field draws on theories and methods including graph theory from mathematics, statistical mechanics from physics, data mining and information visualization from computer science, inferential modeling from statistics, and social structure from sociology. The United States National Research Council defines network science as ""the study of network representations of physical, biological, and social phenomena leading to predictive models of these phenomena.""