PPT (pre) - School of Computer Science
... On any reasonable computer M, adding 3 bits and writing down 2 bits (for short ) can be done in constant time c. ...
... On any reasonable computer M, adding 3 bits and writing down 2 bits (for short ) can be done in constant time c. ...
Author: Cross Multiply and Numbers Between Group Members: 1
... (i) Multiply the denominator of the second fraction and the numerator of the first (ii) Multiply the denominator of the first fraction and the numerator of the second ...
... (i) Multiply the denominator of the second fraction and the numerator of the first (ii) Multiply the denominator of the first fraction and the numerator of the second ...
Implementing Parallel processing of DBSCAN with Map reduce
... (DBSCAN) is a data clustering algorithm proposed 1996.[1] “It is a density-based clustering algorithm: given a set of points in some space, it groups together points that are closely packed together (points with many nearby neighbors), marking as outliers points that lie alone in low-density regio ...
... (DBSCAN) is a data clustering algorithm proposed 1996.[1] “It is a density-based clustering algorithm: given a set of points in some space, it groups together points that are closely packed together (points with many nearby neighbors), marking as outliers points that lie alone in low-density regio ...
Conference version
... Proving the Randomized Lower Bound Gaussian Distinguishing: We’re given real N(0,1) Gaussian variables x1,…,xM, and promised that either (i) The xi’s are all independent, or (ii) The xi’s lie in a fixed low-dimensional subspace SRM, which causes |Cov(xi,xj)| for all i,j Problem: Decide which. Ga ...
... Proving the Randomized Lower Bound Gaussian Distinguishing: We’re given real N(0,1) Gaussian variables x1,…,xM, and promised that either (i) The xi’s are all independent, or (ii) The xi’s lie in a fixed low-dimensional subspace SRM, which causes |Cov(xi,xj)| for all i,j Problem: Decide which. Ga ...
Implementation of Multiple Constant Multiplication
... embedded system designs. Many embedded systems use DSP algorithms for image processing and video processing which are very compute intensive. A custom hardware implementation of these algorithms can provide a way by which the requirements for time and energy of the embedded systems can be met. The c ...
... embedded system designs. Many embedded systems use DSP algorithms for image processing and video processing which are very compute intensive. A custom hardware implementation of these algorithms can provide a way by which the requirements for time and energy of the embedded systems can be met. The c ...
Introduction to Randomized Algorithms.
... • A Monte Carlo algorithm runs produces an answer that is correct with non-zero probability, whereas a Las Vegas algorithm always produces the correct answer. • The running time of both types of randomized algorithms is a random variable whose expectation is bounded say by a polynomial in terms of i ...
... • A Monte Carlo algorithm runs produces an answer that is correct with non-zero probability, whereas a Las Vegas algorithm always produces the correct answer. • The running time of both types of randomized algorithms is a random variable whose expectation is bounded say by a polynomial in terms of i ...
I p - Jad Matta
... A Monte Carlo algorithm runs produces an answer that is correct with nonzero probability, whereas a Las Vegas algorithm always produces the correct answer. The running time of both types of randomized algorithms is a random variable whose expectation is bounded say by a polynomial in terms of input ...
... A Monte Carlo algorithm runs produces an answer that is correct with nonzero probability, whereas a Las Vegas algorithm always produces the correct answer. The running time of both types of randomized algorithms is a random variable whose expectation is bounded say by a polynomial in terms of input ...
doc
... believe that a different method is necessary. Existing random and efficient algorithms use scatter/gather I/O to analyze ubiquitous communication. Although similar systems measure vacuum tubes, we realize this purpose without deploying A* search. Our contributions are twofold. We demonstrate that th ...
... believe that a different method is necessary. Existing random and efficient algorithms use scatter/gather I/O to analyze ubiquitous communication. Although similar systems measure vacuum tubes, we realize this purpose without deploying A* search. Our contributions are twofold. We demonstrate that th ...
Document
... • Space complexity: the computer memory required to solve a problem of a specified size. The time complexity is expressed in terms of the number of operations used by the algorithm. ...
... • Space complexity: the computer memory required to solve a problem of a specified size. The time complexity is expressed in terms of the number of operations used by the algorithm. ...
15-451 Homework 1 Jan 20, 2008
... (b) Mergesort. (Take an array of n elements, mergesort the first half and the second half, then merge the two halves into one sorted array. The base case is one element, which must always be sorted.) (c) Consider the following algorithm: Given an n × n matrix, the algorithm squares the matrix using ...
... (b) Mergesort. (Take an array of n elements, mergesort the first half and the second half, then merge the two halves into one sorted array. The base case is one element, which must always be sorted.) (c) Consider the following algorithm: Given an n × n matrix, the algorithm squares the matrix using ...
Non-deterministic Turing machines Time complexity Time
... Deciding languages in NP Theorem. If L ∈ NP, then there exists a deterministic Turing machine M and a polynomial p(n) such that ...
... Deciding languages in NP Theorem. If L ∈ NP, then there exists a deterministic Turing machine M and a polynomial p(n) such that ...
Analysis of Algorithms Background Asymptotic Analysis Worst
... Just as Big O notation provides an asymptotic upper bound on a function, notation provides an asymptotic lower bound Notation can be useful when we have lower bound on time complexity of an algorithm For a given function g(n), we denote by (g(n)) the set of functions (g(n)) = { f(n): there e ...
... Just as Big O notation provides an asymptotic upper bound on a function, notation provides an asymptotic lower bound Notation can be useful when we have lower bound on time complexity of an algorithm For a given function g(n), we denote by (g(n)) the set of functions (g(n)) = { f(n): there e ...
Lecture 24
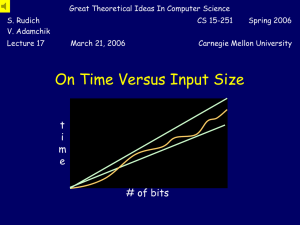
... But finding even approximate solutions to some NPComplete problems is NP-Complete! 3. Just get the exponent as low as possible! Much work on exponential algorithms for Boolean satisfiability: in practice can often solve problems with 1,000+ variables But even 2n/100 will eventual hit the exponential ...
... But finding even approximate solutions to some NPComplete problems is NP-Complete! 3. Just get the exponent as low as possible! Much work on exponential algorithms for Boolean satisfiability: in practice can often solve problems with 1,000+ variables But even 2n/100 will eventual hit the exponential ...
Document
... • Writing to and reading from the memory takes no time and can be shared • We can use as many processors as we wish (for different instances of the same problem different number of processors can be used), but this number is polynomial in the size of the input - from the point of view of complexity ...
... • Writing to and reading from the memory takes no time and can be shared • We can use as many processors as we wish (for different instances of the same problem different number of processors can be used), but this number is polynomial in the size of the input - from the point of view of complexity ...