03-60-330-01 Winter 2010 - School of Computer Science
... 55. The most volatile form of computer storage is ____. A) random access memory B) CPU registers C) tape drive D) magnetic disk ...
... 55. The most volatile form of computer storage is ____. A) random access memory B) CPU registers C) tape drive D) magnetic disk ...
ppt
... are child processes and the creator is the parent. In some systems, the parent defines (or donates) resources and privileges for its children. When a child is created, the parent may either wait for it to finish its task, or continue in parallel. In Unix, subprocesses are created by a call to Fork; ...
... are child processes and the creator is the parent. In some systems, the parent defines (or donates) resources and privileges for its children. When a child is created, the parent may either wait for it to finish its task, or continue in parallel. In Unix, subprocesses are created by a call to Fork; ...
In today lecture we take a closer look at how the different types of
... Lightweight process (LWP) is the solution to these problems. It lies in a hybrid form of user-level & kernel-level threads. LWP runs in the context of a single (Heavyweight) process, and there can be several LWPs per process. In addition to having LWPs, a system also offers a user-level thread packa ...
... Lightweight process (LWP) is the solution to these problems. It lies in a hybrid form of user-level & kernel-level threads. LWP runs in the context of a single (Heavyweight) process, and there can be several LWPs per process. In addition to having LWPs, a system also offers a user-level thread packa ...
course syllabus
... By the end of the semester, students in this course would have developed their own basic functions of an operating system through the completion of a series of laboratory assignment. The lectures will help to familiarize students with the main concepts of an operating system. Technical Requirements: ...
... By the end of the semester, students in this course would have developed their own basic functions of an operating system through the completion of a series of laboratory assignment. The lectures will help to familiarize students with the main concepts of an operating system. Technical Requirements: ...
History of OS
... Schedule :6:20-9:00 pm 236 NE Textbook : Operating System Concepts, 7th edition, by Silbcrsehatz, Galvin, Gagne. ISBN: 0-471-69466-5 ...
... Schedule :6:20-9:00 pm 236 NE Textbook : Operating System Concepts, 7th edition, by Silbcrsehatz, Galvin, Gagne. ISBN: 0-471-69466-5 ...
PPT
... – ready: The process is waiting to run – running: Instructions are being executed – waiting: Process waiting for some event to occur – terminated: The process has finished execution ...
... – ready: The process is waiting to run – running: Instructions are being executed – waiting: Process waiting for some event to occur – terminated: The process has finished execution ...
MIDTERM #1 - School of Computer Science
... 2. An operating system may be viewed as a resource allocator of such things as CPU time, memory space, file-storage space, I/O devices, and so on, due to the requirement that _________ . A) such things need to allocated to be useful for operating systems to work B) conflicts of resource usage must n ...
... 2. An operating system may be viewed as a resource allocator of such things as CPU time, memory space, file-storage space, I/O devices, and so on, due to the requirement that _________ . A) such things need to allocated to be useful for operating systems to work B) conflicts of resource usage must n ...
operating systems - Ronny`s Web Site
... system keeps several programs in memory simultaneously. it increases CPU utilization by organizing job so that the CPU always has one to executed. Operating system ...
... system keeps several programs in memory simultaneously. it increases CPU utilization by organizing job so that the CPU always has one to executed. Operating system ...
Lecture 7: Critical review of semaphores
... processes share critical sections (i.e. parts of two or more processes which need to access some shared resource which can only safely be used by one process at a time). This is possible where lots of processes share lots of resources, in which case a separate binary sem4 is needed for mutual exclus ...
... processes share critical sections (i.e. parts of two or more processes which need to access some shared resource which can only safely be used by one process at a time). This is possible where lots of processes share lots of resources, in which case a separate binary sem4 is needed for mutual exclus ...
CS 111 Processes
... Processes can also cause each other to exit with signals (see the next lecture). Usually such system calls have special access checks -- for example, a process owned by user U can only kill other processes owned by user U. Otherwise, users could arbitrarily kill each other's jobs. Note that a parent ...
... Processes can also cause each other to exit with signals (see the next lecture). Usually such system calls have special access checks -- for example, a process owned by user U can only kill other processes owned by user U. Otherwise, users could arbitrarily kill each other's jobs. Note that a parent ...
Chapter 2 Operating System Overview
... involves the use of multiple components that either perform the same function simultaneously or are configured so that one component is available as a backup in case of the failure of another component ...
... involves the use of multiple components that either perform the same function simultaneously or are configured so that one component is available as a backup in case of the failure of another component ...
pdf
... Consider the various definitions of operating system. Next, consider whether the operating system should include applications such as Web browsers and mail programs. Argue both that it should and that it should not, and support your answers. Answer: Point. Applications such as web browsers and email ...
... Consider the various definitions of operating system. Next, consider whether the operating system should include applications such as Web browsers and mail programs. Argue both that it should and that it should not, and support your answers. Answer: Point. Applications such as web browsers and email ...
ppt - Computer Science
... generation micro-kernels such as Mach or Chorus). Really fast message passing systems were needed to run device drivers and other performance critical components at the user-level. • So, programmers started to circumvent ipc. For example, co-locating device drivers and other components back into the ...
... generation micro-kernels such as Mach or Chorus). Really fast message passing systems were needed to run device drivers and other performance critical components at the user-level. • So, programmers started to circumvent ipc. For example, co-locating device drivers and other components back into the ...
Lecture 2
... – Keep multiple jobs in memory. – When one job blocks on I/O (or other events), the operating system: • Starts the I/O operation. • Switches to another job that is ready to execute. • Now the CPU and I/O device are executing in parallel. ...
... – Keep multiple jobs in memory. – When one job blocks on I/O (or other events), the operating system: • Starts the I/O operation. • Switches to another job that is ready to execute. • Now the CPU and I/O device are executing in parallel. ...
Operating Systems Security
... Linux, DOS, OS X • 32-bit Linux: Lower 3GB for user code/data, top 1GB for kernel • Corresponds to x86 privilege ring transitions • Windows and OS X similar • DOS had no such fence, any process could alter DOS and viruses could spread by hooking DOS interrupt handlers via kernel changes ...
... Linux, DOS, OS X • 32-bit Linux: Lower 3GB for user code/data, top 1GB for kernel • Corresponds to x86 privilege ring transitions • Windows and OS X similar • DOS had no such fence, any process could alter DOS and viruses could spread by hooking DOS interrupt handlers via kernel changes ...
OS 20 I/O Management
... I/O operations from user memory space creates problems The pages holding the data must remain in main memory Limits choices O.S. can make Cannot completely swap out process, or deadlock may result Process waiting for I/O to complete I/O waiting for process to be swapped in ...
... I/O operations from user memory space creates problems The pages holding the data must remain in main memory Limits choices O.S. can make Cannot completely swap out process, or deadlock may result Process waiting for I/O to complete I/O waiting for process to be swapped in ...
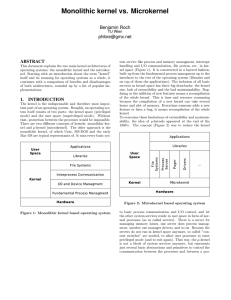
Monolithic kernel vs. Microkernel
... a socket, is also called server, while the other processes are called clients. Because messages sent through sockets are not limited to numerical values, the information could be more than just control signals. There is no limitation upon extensibility, as long as the server knows what the received ...
... a socket, is also called server, while the other processes are called clients. Because messages sent through sockets are not limited to numerical values, the information could be more than just control signals. There is no limitation upon extensibility, as long as the server knows what the received ...
CS_Course_Syllabus_Template
... c) An ability to design, implement, and evaluate a computer-based system, process, component, or program to meet desired needs. d) An ability to function effectively on teams to accomplish a common goal. e) An understanding of professional, ethical, legal, security and social issues and ...
... c) An ability to design, implement, and evaluate a computer-based system, process, component, or program to meet desired needs. d) An ability to function effectively on teams to accomplish a common goal. e) An understanding of professional, ethical, legal, security and social issues and ...
Chapter 2: Operating-System Structures • Operating-System
... rather for ensuring efficient system operations. • Resource allocation – allocating resources, such as CPU cycles, main memory, file storage, I/O devices, to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of c ...
... rather for ensuring efficient system operations. • Resource allocation – allocating resources, such as CPU cycles, main memory, file storage, I/O devices, to multiple users or multiple jobs running at the same time. • Accounting – keep track of and record which users use how much and what kinds of c ...
Operating system
... switches jobs so frequently that users can interact with each job while it is running, creating interactive computing – Response time should be < 1 second – Each user has at least one program executing in memory process – If several jobs ready to run at the same time CPU scheduling – If processes ...
... switches jobs so frequently that users can interact with each job while it is running, creating interactive computing – Response time should be < 1 second – Each user has at least one program executing in memory process – If several jobs ready to run at the same time CPU scheduling – If processes ...
The OS 215 Project
... Start_timer calls the Z215_DELAY_TIMER to give the request for a future interrupt. The timer starts thinking about the time, but interrupts in the future!! Start_timer realizes there’s nothing else to do and so calls Z215_IDLE. This routine says to idle the processor until an interrupt occurs. Svc m ...
... Start_timer calls the Z215_DELAY_TIMER to give the request for a future interrupt. The timer starts thinking about the time, but interrupts in the future!! Start_timer realizes there’s nothing else to do and so calls Z215_IDLE. This routine says to idle the processor until an interrupt occurs. Svc m ...
PPTX - Duke Computer Science
... conventions for use of the registers by executable code. • Each processor core has at least one register set for use by a code stream running on that core. – Multi-threaded cores (“SMT”) have multiple register sets and can run multiple streams of instructions simultaneously. ...
... conventions for use of the registers by executable code. • Each processor core has at least one register set for use by a code stream running on that core. – Multi-threaded cores (“SMT”) have multiple register sets and can run multiple streams of instructions simultaneously. ...
Introduction to Object Technology
... • usually based on the position of the requested sector rather than according to the process priority • shortest-service-time-first (SSTF): pick the request that requires the least movement of the head • SCAN (back and forth over disk): good distribution • C-SCAN(one way with fast return):lower serv ...
... • usually based on the position of the requested sector rather than according to the process priority • shortest-service-time-first (SSTF): pick the request that requires the least movement of the head • SCAN (back and forth over disk): good distribution • C-SCAN(one way with fast return):lower serv ...
Operating Systems CIS 250
... – done via a system call – usually done as a trap to a specific location in the interrupt vector – hardware treats a trap as a software interrupt, checks if a valid request, sets mode bit to ...
... – done via a system call – usually done as a trap to a specific location in the interrupt vector – hardware treats a trap as a software interrupt, checks if a valid request, sets mode bit to ...