Introduction to Distributed Systems
... user at one site may be able to use the resources available at another. Resource sharing in distributed systems provide mechanism for sharing files at remote site, processing information in a distributed database, printing files at remote sites, using specialized hardware devices (high speed array p ...
... user at one site may be able to use the resources available at another. Resource sharing in distributed systems provide mechanism for sharing files at remote site, processing information in a distributed database, printing files at remote sites, using specialized hardware devices (high speed array p ...
On-Line & Real-Time Modes of Use Presentation
... The trolley would very soon leave the black line because it would not be steering quickly enough. ...
... The trolley would very soon leave the black line because it would not be steering quickly enough. ...
The Java Virtual Shell and Kernel
... operating systems that supports Java Runtime Environment. The shell and kernel would be designed in such a way that the beneath platform (operating system and hardware) should not impact on the syntax and output. Also there should be a unique set of commands that we are going to develop, which will ...
... operating systems that supports Java Runtime Environment. The shell and kernel would be designed in such a way that the beneath platform (operating system and hardware) should not impact on the syntax and output. Also there should be a unique set of commands that we are going to develop, which will ...
Processes and Threads - University of Waterloo
... open/close a file (open/close); send a message over a pipe (send); create another process (fork/clone); change its own scheduling priority (setpriority); change the size of its address space; change the user it is associated with (setuid); terminate itself (exit). ...
... open/close a file (open/close); send a message over a pipe (send); create another process (fork/clone); change its own scheduling priority (setpriority); change the size of its address space; change the user it is associated with (setuid); terminate itself (exit). ...
Module 4: Processes
... Interrupt handler may simply perform its function and then return to the same process that was interrupted (restoring the PC and PSW from the stack). Alternatively, may no longer be appropriate to resume execution of process that was running because: process has used up its current CPU quantum p ...
... Interrupt handler may simply perform its function and then return to the same process that was interrupted (restoring the PC and PSW from the stack). Alternatively, may no longer be appropriate to resume execution of process that was running because: process has used up its current CPU quantum p ...
on Operating Systems
... – Ready to run but waiting for a processor ready status – There also exists a group of processes that are waiting for some service or communication - blocked status – There also exists a group of processes that are currently running - running status – The latter two are not strictly speaking queues, ...
... – Ready to run but waiting for a processor ready status – There also exists a group of processes that are waiting for some service or communication - blocked status – There also exists a group of processes that are currently running - running status – The latter two are not strictly speaking queues, ...
Solutions - Philadelphia University Jordan
... Question 3:Describe the three general methods used to pass parameters to the operating system during system calls. 3 points 1- pass the parameters in registers which is useful if the amount of data is small and can be fit in register. This method is fast but can pass large amount of data. 2- parame ...
... Question 3:Describe the three general methods used to pass parameters to the operating system during system calls. 3 points 1- pass the parameters in registers which is useful if the amount of data is small and can be fit in register. This method is fast but can pass large amount of data. 2- parame ...
Nachos Overview - Computer and Information Science | Brooklyn
... effects. Our course project, which is based on Nachos, provides you an opportunity to learn how basic concepts may be used to solve real problems. ...
... effects. Our course project, which is based on Nachos, provides you an opportunity to learn how basic concepts may be used to solve real problems. ...
FileSystems
... Levels of structuring None - sequence of words, bytes Simple record structure Lines Fixed length Variable length Complex structures Formatted document Relocatable load file Can simulate last two with first method by inserting appropriate control characters. Need at least execut ...
... Levels of structuring None - sequence of words, bytes Simple record structure Lines Fixed length Variable length Complex structures Formatted document Relocatable load file Can simulate last two with first method by inserting appropriate control characters. Need at least execut ...
Processes
... – the program counter (PC), indicating the next instruction – general-purpose processor registers and their values – a set of OS resources • open files, network connections, sound channels, … ...
... – the program counter (PC), indicating the next instruction – general-purpose processor registers and their values – a set of OS resources • open files, network connections, sound channels, … ...
Advanced Interactive Executive (AIX) operating system overview
... underlying hardware. We had decided to start with the U N I X system as a base. In view of our requirements, however, we were faced with the question of how best to provide the required enhancements. Two strategies could be followed. One was to rewrite the entire kernel. Although theoretically possi ...
... underlying hardware. We had decided to start with the U N I X system as a base. In view of our requirements, however, we were faced with the question of how best to provide the required enhancements. Two strategies could be followed. One was to rewrite the entire kernel. Although theoretically possi ...
15 - Web Services Overview
... Typing Control-D (“End of file”) causes the read request to be satisfied immediately Do not wait for “enter key” Do not wait for any characters at all May return 0 characters Within the user program count = Read (fd, buffer, buffSize) if count == 0 -- Assume end-of-file reached... ...
... Typing Control-D (“End of file”) causes the read request to be satisfied immediately Do not wait for “enter key” Do not wait for any characters at all May return 0 characters Within the user program count = Read (fd, buffer, buffSize) if count == 0 -- Assume end-of-file reached... ...
slides - Department of Computer Science
... Large write sharing costs on many platforms Large secondary caches needed to mask disk delays NUMA h/w, which suffers from false sharing of cache lines Contention for shared objects ...
... Large write sharing costs on many platforms Large secondary caches needed to mask disk delays NUMA h/w, which suffers from false sharing of cache lines Contention for shared objects ...
Lecture7
... waits on the corresponding condition variable. Two operations can be performed on a condition variable: Wait(v) and Signal(v). Memory-mapped file: a segment of virtual memory which has been assigned a direct byte-for-byte correlation with some portion of a file or file-like resource. This resource c ...
... waits on the corresponding condition variable. Two operations can be performed on a condition variable: Wait(v) and Signal(v). Memory-mapped file: a segment of virtual memory which has been assigned a direct byte-for-byte correlation with some portion of a file or file-like resource. This resource c ...
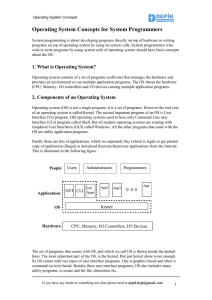
Operating System Concepts for System Programmers
... So OS comes with two types of user interface programs. One is graphics based and other is command (or text) based. Besides these user interface programs, OS also includes many utility programs, to create and list file, directories etc.. If you have any doubt or something not clear please mail to dep ...
... So OS comes with two types of user interface programs. One is graphics based and other is command (or text) based. Besides these user interface programs, OS also includes many utility programs, to create and list file, directories etc.. If you have any doubt or something not clear please mail to dep ...
Module 3: Operating
... memory owned by other processes. Both processes must agree to remove O.S. memory restriction so that they can access the same region of memory. The processes are responsible for the form and location of the data. The processes are responsible for making sure that they are not writing to the same mem ...
... memory owned by other processes. Both processes must agree to remove O.S. memory restriction so that they can access the same region of memory. The processes are responsible for the form and location of the data. The processes are responsible for making sure that they are not writing to the same mem ...
No Slide Title
... 1991 by Linus Torvalds, with the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet. It has been designed to run efficiently and reliably on common PC hardware, but also runs o ...
... 1991 by Linus Torvalds, with the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet. It has been designed to run efficiently and reliably on common PC hardware, but also runs o ...
Silberschatz, Galvin and Gagne ©2013 Operating System Concepts
... - STREAM head interfaces with the user process - driver end interfaces with the device - zero or more STREAM modules between them ...
... - STREAM head interfaces with the user process - driver end interfaces with the device - zero or more STREAM modules between them ...
ppt
... Provides a controlled communication facility between extensions and the base system Extensions in SPIN are defined in terms of events and handlers The primary right to handle an event is restricted to the default implementation module for the event, which is the module that statically exports the pr ...
... Provides a controlled communication facility between extensions and the base system Extensions in SPIN are defined in terms of events and handlers The primary right to handle an event is restricted to the default implementation module for the event, which is the module that statically exports the pr ...
Slide 11 : Uniprocessor Scheduling
... their complexity, their characteristic time scale, and their level of abstraction ...
... their complexity, their characteristic time scale, and their level of abstraction ...
Mach Memory
... Default Pager: Similar interface to other data managers, but a trusted component. ...
... Default Pager: Similar interface to other data managers, but a trusted component. ...