Week-2
... data that must be kept for a “long” period of time Proper management is of central importance Entire speed of computer operation hinges on disk subsystem and its ...
... data that must be kept for a “long” period of time Proper management is of central importance Entire speed of computer operation hinges on disk subsystem and its ...
CS430 – Operating Systems 07/06/2006 – 08/27/2006 – Fort Collins Facilitator Information
... (defined as using inappropriate sources of information on a test) or plagiarism (defined as presenting as one’s own, the ideas, words, or products of another). Such sanctions may include a failing grade on the assignment, failure of the course, or expulsion of the student from the course or the depa ...
... (defined as using inappropriate sources of information on a test) or plagiarism (defined as presenting as one’s own, the ideas, words, or products of another). Such sanctions may include a failing grade on the assignment, failure of the course, or expulsion of the student from the course or the depa ...
Chapter 5 - Input/Output
... scan and the other for new requests during the scan • When a scan begins, all new requests are in one of the queues, with the other being empty • During the scan, all new requests are put into the queue that was initially empty • Thus, service of new requests is deferred until all the old requests h ...
... scan and the other for new requests during the scan • When a scan begins, all new requests are in one of the queues, with the other being empty • During the scan, all new requests are put into the queue that was initially empty • Thus, service of new requests is deferred until all the old requests h ...
Support Notes for SUSE LINUX Enterprise Servers HP Part Number: 5900-0402
... will function and any iLO 2 vKVM mouse that has been configured, will be ignored. The vKVM mouse enabled in the Integrity Integrated Lights-Out (iLO 2) Advanced Pack will be ignored during installation. The vKVM mouse will function with the X11 server was the system has been installed. Another user ...
... will function and any iLO 2 vKVM mouse that has been configured, will be ignored. The vKVM mouse enabled in the Integrity Integrated Lights-Out (iLO 2) Advanced Pack will be ignored during installation. The vKVM mouse will function with the X11 server was the system has been installed. Another user ...
AIX is building momentum as the leading, UNIX operating system for
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
slides
... operations directly, the operating system must provide some means to perform I/O. • File-system manipulation – program capability to read, write, create, and delete files. • Communications – exchange of information between processes executing either on the same computer or on different systems tied ...
... operations directly, the operating system must provide some means to perform I/O. • File-system manipulation – program capability to read, write, create, and delete files. • Communications – exchange of information between processes executing either on the same computer or on different systems tied ...
Chapter 4
... renaming files not to change the extension. Explain that most programs, such as Microsoft Office XP and 2003 automatically add the extension to the filename. ...
... renaming files not to change the extension. Explain that most programs, such as Microsoft Office XP and 2003 automatically add the extension to the filename. ...
Operating Systems Cheat Sheet by makahoshi1
... Each queue also has it's own scheduling alogorithm, so System processes could use FCFS while student processes use RR. Each queue has absolute priority over lower priority queues, but it is possible to time-slice among queues so each queue gets a certain portion of CPU time. Describe a multilevel f ...
... Each queue also has it's own scheduling alogorithm, so System processes could use FCFS while student processes use RR. Each queue has absolute priority over lower priority queues, but it is possible to time-slice among queues so each queue gets a certain portion of CPU time. Describe a multilevel f ...
REF Chapter 3: Windows NT System Specifics
... A third way to abbreviate commands is to specify environment variables (also referred to as logical names) in place of part or all of a frequently-used file descriptor. An environment variable is used to achieve device/file independence by associating a physical file on the operating system with som ...
... A third way to abbreviate commands is to specify environment variables (also referred to as logical names) in place of part or all of a frequently-used file descriptor. An environment variable is used to achieve device/file independence by associating a physical file on the operating system with som ...
(IT) - Sem - III - Modern Operating System
... essentially merged, differing mostly in size, weight, and user interface. Almost all of them are based on 32-bit CPUs with protected mode and run a sophisticated operating system. One major difference between handhelds and PCs is that the former do not have multigigabyte hard disks, which changes a ...
... essentially merged, differing mostly in size, weight, and user interface. Almost all of them are based on 32-bit CPUs with protected mode and run a sophisticated operating system. One major difference between handhelds and PCs is that the former do not have multigigabyte hard disks, which changes a ...
Week_3 Operating system File
... A thread is a basic unit of CPU utilization; it comprises a thread ID, a program counter, a register set, and a stack. If a process has multiple threads of control, it can perform more than one task at a time. In certain situations, a single application may be required to perform several simil ...
... A thread is a basic unit of CPU utilization; it comprises a thread ID, a program counter, a register set, and a stack. If a process has multiple threads of control, it can perform more than one task at a time. In certain situations, a single application may be required to perform several simil ...
No Slide Title
... Coding is time-consuming Leads to missed opportunities for parallel processing Leads to errors where parallel processing is mistakenly indicated Programs are difficult to modify ...
... Coding is time-consuming Leads to missed opportunities for parallel processing Leads to errors where parallel processing is mistakenly indicated Programs are difficult to modify ...
CS345 02 - Computer Systems
... through Interrupts. For example when a disk driver has finished transferring the requested data, it generates an interrupt to the OS to inform the OS that the task is over. Interrupts occur asynchronously to the ongoing activity of the processor. Thus the times at which interrupts occur are unpr ...
... through Interrupts. For example when a disk driver has finished transferring the requested data, it generates an interrupt to the OS to inform the OS that the task is over. Interrupts occur asynchronously to the ongoing activity of the processor. Thus the times at which interrupts occur are unpr ...
Comparative Operating Systems Fall 2001 An Examination of
... sophisticated, highly reputable operating system for desktop PC's and servers. Since Linux is so well accepted, and free with open source code, it is no wonder that embedded developers have begun to look for ways to incorporate it into their devices. ...
... sophisticated, highly reputable operating system for desktop PC's and servers. Since Linux is so well accepted, and free with open source code, it is no wonder that embedded developers have begun to look for ways to incorporate it into their devices. ...
Silberschatz, Galvin and Gagne ©2009 Operating System Concepts
... Provide details of the performance aspects of I/O hardware and software ...
... Provide details of the performance aspects of I/O hardware and software ...
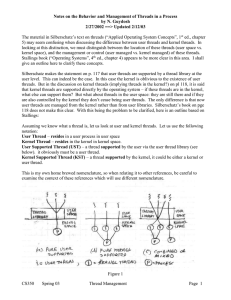
Notes by Guydosh on Thread managment
... LWPs are scheduled by the kernel independently, and may execute in parallel in a multiprocessor environment – a key reason for their existence. Kernel Threads: These are the fundamental entities that cab be scheduled and dispatched to run on one of a number of system processors. An LWP is visible ...
... LWPs are scheduled by the kernel independently, and may execute in parallel in a multiprocessor environment – a key reason for their existence. Kernel Threads: These are the fundamental entities that cab be scheduled and dispatched to run on one of a number of system processors. An LWP is visible ...
The Kernel Real Time Operating Systems and Middleware
... Programming Paradigms • Shared memory (threads) • The kernel must provide mutexes + condition variables • Real-time resource sharing protocols (PI, HLP, NPP, ...) must be implemented • Message passing (processes) • Interaction models: pipeline, client / server, ... • The kernel must provide some IP ...
... Programming Paradigms • Shared memory (threads) • The kernel must provide mutexes + condition variables • Real-time resource sharing protocols (PI, HLP, NPP, ...) must be implemented • Message passing (processes) • Interaction models: pipeline, client / server, ... • The kernel must provide some IP ...
1.01 - Kau
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
A Pattern Language for Secure Operating System Architectures
... into segments that correspond to logical units in the programs. Use special words (descriptors) to represent access rights for these segments. • Reference Monitor. How to enforce authorizations when a process requests access to an object? Define an abstract process that intercepts all requests for r ...
... into segments that correspond to logical units in the programs. Use special words (descriptors) to represent access rights for these segments. • Reference Monitor. How to enforce authorizations when a process requests access to an object? Define an abstract process that intercepts all requests for r ...