Ch. 4 Operating System Fundamentals
... are software programs that control thousands of operations, provide an interface between the user and the computer, and run applications. • An OS is designed to control the operations of programs such as web browsers, word processors, and e-mail programs. ...
... are software programs that control thousands of operations, provide an interface between the user and the computer, and run applications. • An OS is designed to control the operations of programs such as web browsers, word processors, and e-mail programs. ...
Chapter 1 and 2 Computer System and Operating
... Operating Systems • It may be easier to understand the key requirements of an OS by considering the evolution of Operating Systems • Stages include ...
... Operating Systems • It may be easier to understand the key requirements of an OS by considering the evolution of Operating Systems • Stages include ...
System Calls
... they were all hardware • A virtual machine provides an interface identical to the underlying bare hardware • The operating system host creates the illusion that a process has its own processor and (virtual memory) • Each guest provided with a (virtual) copy of underlying computer ...
... they were all hardware • A virtual machine provides an interface identical to the underlying bare hardware • The operating system host creates the illusion that a process has its own processor and (virtual memory) • Each guest provided with a (virtual) copy of underlying computer ...
Overlay Networks
... – Node does a lookup on its own id – And learns the node responsible for that id – This node becomes the new node’s successor – And the node can learn that node’s predecessor (which will become the new node’s predecessor) ...
... – Node does a lookup on its own id – And learns the node responsible for that id – This node becomes the new node’s successor – And the node can learn that node’s predecessor (which will become the new node’s predecessor) ...
O(Log N) - DEIM (URV) - Universitat Rovira i Virgili
... • Maps keys onto nodes in a 1D circular space • Uses consistent hashing –D.Karger, E.Lehman • Aimed at large-scale peer-to-peer applications ...
... • Maps keys onto nodes in a 1D circular space • Uses consistent hashing –D.Karger, E.Lehman • Aimed at large-scale peer-to-peer applications ...
Architectural Support for Operating Systems
... • In the idle loop: – OS executes an infinite loop (UNIX) – OS performs some system management & profiling – OS halts the processor and enter in low-power mode (notebooks) – OS computes some function (DEC’s VMS on VAX computed Pi) • OS wakes up on: – interrupts from hardware devices – traps from use ...
... • In the idle loop: – OS executes an infinite loop (UNIX) – OS performs some system management & profiling – OS halts the processor and enter in low-power mode (notebooks) – OS computes some function (DEC’s VMS on VAX computed Pi) • OS wakes up on: – interrupts from hardware devices – traps from use ...
Administration of an Oracle Distributed Database System
... Recovery from isolated failures also has no effect on other nodes. ...
... Recovery from isolated failures also has no effect on other nodes. ...
Introduction to Operating Systems
... 80% of time taken by 20% of code 10% of memory absorbs 90% of references Basis behind cache: place 10% in fast memory, 90% in slow, usually looks like one big fast memory What’s the best cache entry to replace? ...
... 80% of time taken by 20% of code 10% of memory absorbs 90% of references Basis behind cache: place 10% in fast memory, 90% in slow, usually looks like one big fast memory What’s the best cache entry to replace? ...
Lecture3-os-support
... • Compiler checks safe memory access • In addition there are manifests w.r.t. what the process will and will not do • This way you get protection • And no need for hardware protection domains – everything can run in a single address space • Singularity: an OS from Microsoft implemented these concept ...
... • Compiler checks safe memory access • In addition there are manifests w.r.t. what the process will and will not do • This way you get protection • And no need for hardware protection domains – everything can run in a single address space • Singularity: an OS from Microsoft implemented these concept ...
lec1 - b
... Every node j has (model) data Mj , we want to compute an aggregate (e.g. sum) of all data vectors M and distribute it to all nodes. Each node class allreduce(Din, Dout, N) Allreduce is the synchronous version of this process. ...
... Every node j has (model) data Mj , we want to compute an aggregate (e.g. sum) of all data vectors M and distribute it to all nodes. Each node class allreduce(Din, Dout, N) Allreduce is the synchronous version of this process. ...
ch13
... To cope with device speed mismatch To cope with device transfer size mismatch To maintain “copy semantics” ...
... To cope with device speed mismatch To cope with device transfer size mismatch To maintain “copy semantics” ...
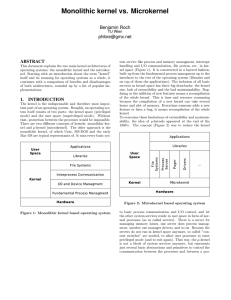
Monolithic kernel vs. Microkernel
... Monolithic kernels (and most of the first generation µ-kernels) run device drivers inside the kernel space. Hardware interrupts are directly handled by kernel processes. To add or change features provided by the hardware, all layers above the changed layer in the monolithic kernel also have to be ch ...
... Monolithic kernels (and most of the first generation µ-kernels) run device drivers inside the kernel space. Hardware interrupts are directly handled by kernel processes. To add or change features provided by the hardware, all layers above the changed layer in the monolithic kernel also have to be ch ...
Process Control
... z a) Is it possible that you would to allow a process to wait on more than one event at the same time? Provide an example. z b) In that case, how you modify the queuing structure of the figure to support this new feature? ...
... z a) Is it possible that you would to allow a process to wait on more than one event at the same time? Provide an example. z b) In that case, how you modify the queuing structure of the figure to support this new feature? ...
2.5.2 cray xt5 jaguar: the top supercomputer in 2009
... Users want to have a distributed system that can achieve scalable performance. Any resource upgrade in a system should be backward compatible with existing hardware and software resources. Overdesign may not be cost-effective. System scaling can increase or decrease resources depending on many pract ...
... Users want to have a distributed system that can achieve scalable performance. Any resource upgrade in a system should be backward compatible with existing hardware and software resources. Overdesign may not be cost-effective. System scaling can increase or decrease resources depending on many pract ...
William Stallings Computer Organization and Architecture
... • Simplifies handling of growing data structures • Allows programs to be altered and recompiled independently, without re-linking and re-loading • Lends itself to sharing among processes • Lends itself to protection • Some systems combine segmentation with ...
... • Simplifies handling of growing data structures • Allows programs to be altered and recompiled independently, without re-linking and re-loading • Lends itself to sharing among processes • Lends itself to protection • Some systems combine segmentation with ...
Document
... 17. What events occur to cause a process to change states? 18. Why should processes not be programmed with built-in assumptions about timing? 19. In what two places may threads be implemented? 20. Name the three states a process can be in A) B) C) 21. Describe why threads are useful. 22. What does i ...
... 17. What events occur to cause a process to change states? 18. Why should processes not be programmed with built-in assumptions about timing? 19. In what two places may threads be implemented? 20. Name the three states a process can be in A) B) C) 21. Describe why threads are useful. 22. What does i ...
Batch systems
... Then came a $FORTRAN card, telling the operating system to load the FORTRAN compiler from the system tape. It was followed by the program to be compiled, and then a $LOAD card, directing the operating system to load the object program just compiled. (Compiled programs were often written on scratch t ...
... Then came a $FORTRAN card, telling the operating system to load the FORTRAN compiler from the system tape. It was followed by the program to be compiled, and then a $LOAD card, directing the operating system to load the object program just compiled. (Compiled programs were often written on scratch t ...
OSCE Chapter 1. - UCSB Computer Science
... Multi-threaded process has one program counter per thread Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Multi-threaded process has one program counter per thread Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
Lecture3-os-support
... – Efficient scheduling, load balancing and thread switching – Efficient thread synchronization – Efficient inter-process communication (IPC) ...
... – Efficient scheduling, load balancing and thread switching – Efficient thread synchronization – Efficient inter-process communication (IPC) ...
1.1. OS Introduction Operating System Types
... in memory. The main advantage of the virtual-memory scheme is that programs can be larger than physical memory. Further, it abstracts main memory into a large, uniform array of storage, separating logical memory as viewed by the user from physical memory. This arrangement frees programmers from conc ...
... in memory. The main advantage of the virtual-memory scheme is that programs can be larger than physical memory. Further, it abstracts main memory into a large, uniform array of storage, separating logical memory as viewed by the user from physical memory. This arrangement frees programmers from conc ...
Distributed operating system
A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node’s hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.The microkernel and the management components collection work together. They support the system’s goal of integrating multiple resources and processing functionality into an efficient and stable system. This seamless integration of individual nodes into a global system is referred to as transparency, or single system image; describing the illusion provided to users of the global system’s appearance as a single computational entity.