A Technical Introduction to NGSCB Security Summit East 2003
... Nothing about this architecture prevents any nexus from running; however, the owner can control which nexuses are allowed to run ...
... Nothing about this architecture prevents any nexus from running; however, the owner can control which nexuses are allowed to run ...
Guide to Network Defense and Countermeasures
... • A network intrusion that is increasing in frequency is the use of scripts – Executable code attached to e-mail messages or downloaded files that infiltrates a system – Difficult for firewalls and intrusion-detection and prevention systems (IDPSs) to block all scripts – Specialty firewalls and othe ...
... • A network intrusion that is increasing in frequency is the use of scripts – Executable code attached to e-mail messages or downloaded files that infiltrates a system – Difficult for firewalls and intrusion-detection and prevention systems (IDPSs) to block all scripts – Specialty firewalls and othe ...
sending alerts when things change. Change management is critical.
... Following the coffee break, I attended Stucchi Massimiliano and Matteo Riondato’s “code walkthrough and a case study” of the FreeSBIE system, a LiveCD based on FreeBSD. Stucchi and Matteo won the award for the third-best paper, based on the positive feedback that conference attendants showed for thi ...
... Following the coffee break, I attended Stucchi Massimiliano and Matteo Riondato’s “code walkthrough and a case study” of the FreeSBIE system, a LiveCD based on FreeBSD. Stucchi and Matteo won the award for the third-best paper, based on the positive feedback that conference attendants showed for thi ...
Chapter 2 – Operating System Overview
... 1. The operating system’s ___________________ refers to its inherent flexibility in permitting functional modifications to the system without interruption of services. ANS: ability to evolve 2. The operating system masks the details of the _______________ from the application programmer. ANS: hardwa ...
... 1. The operating system’s ___________________ refers to its inherent flexibility in permitting functional modifications to the system without interruption of services. ANS: ability to evolve 2. The operating system masks the details of the _______________ from the application programmer. ANS: hardwa ...
Computer Science - Rainhill High School
... Be able to identify advantages and disadvantages of both graphical and command line methods for managing files and folders Understand the link between the GUI and the text-based commands that execute within an operating system Suggest situations where the command line would be preferable to a GUI fo ...
... Be able to identify advantages and disadvantages of both graphical and command line methods for managing files and folders Understand the link between the GUI and the text-based commands that execute within an operating system Suggest situations where the command line would be preferable to a GUI fo ...
Windows Academic Program
... from memory objects Advanced VM features for databases (app management of virtual addresses, physical memory, I/O, dirty bits, and large pages) Plug-and-play, power-management System library mapped in every process ...
... from memory objects Advanced VM features for databases (app management of virtual addresses, physical memory, I/O, dirty bits, and large pages) Plug-and-play, power-management System library mapped in every process ...
Chapter 2: Operating-System Structures Silberschatz, Galvin and Gagne ©2013 – 9
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
OPERATINGSYSTEMS 2015
... Operating system (OS) is the most important type of system software in a computer system. Without an operating system, a user cannot run an application program on their computer. Operating systems are found on almost any device that contains a computer – from cellular phones and video game consoles ...
... Operating system (OS) is the most important type of system software in a computer system. Without an operating system, a user cannot run an application program on their computer. Operating systems are found on almost any device that contains a computer – from cellular phones and video game consoles ...
Chapter 2: Operating-System Structures
... Some of them are simply user interfaces to system calls; others are considerably ...
... Some of them are simply user interfaces to system calls; others are considerably ...
Chapter X Slides
... • NIPS Network Based Intrusion Protection System In series In parallel Examines every packet Does not protect against “Atomic” attacks Delay is a problem for voice ...
... • NIPS Network Based Intrusion Protection System In series In parallel Examines every packet Does not protect against “Atomic” attacks Delay is a problem for voice ...
UNIX Notes:
... operating systems. Starting with Windows 2000; Windows XP, Vista and Windows 7 -all have POSIX compliant kernels. Popular Linux OS distributions include: Ubuntu, Fedora, Cygwin, UWin, GNU-win, Debian, Redhat, Knoppix, DSL, Gentu, TinyCore, and MSys. Since it started more than 50 years ago, UNIX has ...
... operating systems. Starting with Windows 2000; Windows XP, Vista and Windows 7 -all have POSIX compliant kernels. Popular Linux OS distributions include: Ubuntu, Fedora, Cygwin, UWin, GNU-win, Debian, Redhat, Knoppix, DSL, Gentu, TinyCore, and MSys. Since it started more than 50 years ago, UNIX has ...
unit-1-The-UNIX-Operating-System
... UNIX can be installed on many hardware platforms. Its widespread use can be traced to the decision to develop it using the C language. Multiuser The UNIX design allows multiple users to concurrently share hardware and software Multitasking UNIX allows a user to run more than one program at a time. I ...
... UNIX can be installed on many hardware platforms. Its widespread use can be traced to the decision to develop it using the C language. Multiuser The UNIX design allows multiple users to concurrently share hardware and software Multitasking UNIX allows a user to run more than one program at a time. I ...
UNIX Notes:
... GNU Linux is currently the leading popular “Open Source” implementation of a UNIX clone standard operating system. POSIX is the validation standard, set for UNIX-like operating systems. Starting with Windows 2000; Windows XP, Vista and Windows 7 -all have POSIX compliant kernels. Popular Linux OS di ...
... GNU Linux is currently the leading popular “Open Source” implementation of a UNIX clone standard operating system. POSIX is the validation standard, set for UNIX-like operating systems. Starting with Windows 2000; Windows XP, Vista and Windows 7 -all have POSIX compliant kernels. Popular Linux OS di ...
TreVisor
... TRESOR [19] runs encryption securely outside RAM; it is a Linux kernel patch for the x64 architecture designed to run AES resistant against cold boot attacks. TRESOR avoids RAM usage completely and runs the key management as well as the AES algorithm entirely on the microprocessor. To that end, some ...
... TRESOR [19] runs encryption securely outside RAM; it is a Linux kernel patch for the x64 architecture designed to run AES resistant against cold boot attacks. TRESOR avoids RAM usage completely and runs the key management as well as the AES algorithm entirely on the microprocessor. To that end, some ...
What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
What is an Operating System?
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
ch1
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
... Typically system has many processes, some user, some operating system running concurrently on one or more CPUs ...
ch02
... Attacks (continued) Mail bombing: also a DoS; attacker routes large quantities of e-mail to target Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skill ...
... Attacks (continued) Mail bombing: also a DoS; attacker routes large quantities of e-mail to target Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network Social engineering: using social skill ...
What is an Operating System?
... Many systems now servers, responding to requests generated by clients Compute-server provides an interface to client to request ...
... Many systems now servers, responding to requests generated by clients Compute-server provides an interface to client to request ...
Computer Network and Infrastructure
... Interrupts increase the efficiency of the processor by allowing multiple tasks which may not be sequential in order However if the time required for I/O operations is longer than the user operation (this is the true case) the processor will be idle for a long time. Multiprogramming which has more th ...
... Interrupts increase the efficiency of the processor by allowing multiple tasks which may not be sequential in order However if the time required for I/O operations is longer than the user operation (this is the true case) the processor will be idle for a long time. Multiprogramming which has more th ...
Security Features in Windows CE
... inside a database volume does not give it any additional security. Therefore, this feature is most useful in databases that are stored within the object store. Removing the system file attribute from a database volume that contains a system database will expose that database to access by untrusted a ...
... inside a database volume does not give it any additional security. Therefore, this feature is most useful in databases that are stored within the object store. Removing the system file attribute from a database volume that contains a system database will expose that database to access by untrusted a ...
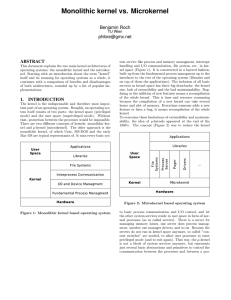
Monolithic kernel vs. Microkernel
... In case of a µ-kernel the services are isolated from each other through the message system. It is enough to reimplement the new memory manager. The processes which formerly used the other manager, do not notice the change. µ-kernels also show their flexibility in removing features 6 . That way a µ-k ...
... In case of a µ-kernel the services are isolated from each other through the message system. It is enough to reimplement the new memory manager. The processes which formerly used the other manager, do not notice the change. µ-kernels also show their flexibility in removing features 6 . That way a µ-k ...