Threads - 5th Semester Notes
... • Multiplexes many user level threads to a smaller or equal number of kernel threads. • The model suffers from neither of those shortcomings of many-to-one and one-to-one models. – No Concurrency, Expensive Threads ...
... • Multiplexes many user level threads to a smaller or equal number of kernel threads. • The model suffers from neither of those shortcomings of many-to-one and one-to-one models. – No Concurrency, Expensive Threads ...
How to Detect Mainframe Intrusion Attempts
... Most of the users are oblivious to the design of the Internet and its components and only use the services provided by their operating system or applications. However, there is a small minority of advanced users who use their knowledge to exploit potential system vulnerabilities. With time and adequ ...
... Most of the users are oblivious to the design of the Internet and its components and only use the services provided by their operating system or applications. However, there is a small minority of advanced users who use their knowledge to exploit potential system vulnerabilities. With time and adequ ...
IBM AIX to Oracle Solaris Technology Mapping Guide
... Host Security .....................................................................................................................41 Network Security ...............................................................................................................41 On-Disk Encryption ........ ...
... Host Security .....................................................................................................................41 Network Security ...............................................................................................................41 On-Disk Encryption ........ ...
Resource Management in a Multicore Operating System
... response times and the ability to react to ad-hoc workload changes. Leveraging and managing the existing potential for parallelization thus presents a difficult challenge for the development of both commodity operating systems and application programs, which have to keep up with hardware development ...
... response times and the ability to react to ad-hoc workload changes. Leveraging and managing the existing potential for parallelization thus presents a difficult challenge for the development of both commodity operating systems and application programs, which have to keep up with hardware development ...
hello world - Computer Engineering
... • Protocol to enable running programs on the web server •These programs produce HTML output which is sent to the client (browser) •Programs can be written in any language (most popular is PERL) ...
... • Protocol to enable running programs on the web server •These programs produce HTML output which is sent to the client (browser) •Programs can be written in any language (most popular is PERL) ...
CodeMoctules O O O
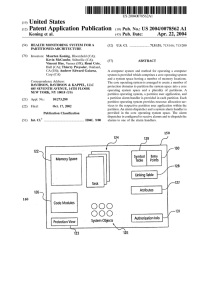
... including a partition operating system and a partition user application. The method further includes generating an alarm in one of the partition protection domains; transmit ting the alarm to the core operating system via the partition operating system in said one of the partitions; accessing an ala ...
... including a partition operating system and a partition user application. The method further includes generating an alarm in one of the partition protection domains; transmit ting the alarm to the core operating system via the partition operating system in said one of the partitions; accessing an ala ...
Lecture-Review-Process
... – can be intended (“trap”): for system call (process wants to enter kernel to obtain services) – or unintended (usually): (“fault/exception”) (division by zero, attempt to execute privileged instruction in user mode, memory access violation, invalid instruction, alignment error, etc.) ...
... – can be intended (“trap”): for system call (process wants to enter kernel to obtain services) – or unintended (usually): (“fault/exception”) (division by zero, attempt to execute privileged instruction in user mode, memory access violation, invalid instruction, alignment error, etc.) ...
The Internet and Its Uses
... Since that time, thousands of organizations rely on this list to prioritize their efforts so they can close the most dangerous holes first. The threat landscape is very dynamic, which in turn makes it necessary to adopt newer security measures. Just over the last few years, the kinds of vulnerabilit ...
... Since that time, thousands of organizations rely on this list to prioritize their efforts so they can close the most dangerous holes first. The threat landscape is very dynamic, which in turn makes it necessary to adopt newer security measures. Just over the last few years, the kinds of vulnerabilit ...
Processes
... process has one or more last-in-first-out (LIFO) stacks associated with it. A stack is used to store parameters and returning addresses for procedure and system calls. ...
... process has one or more last-in-first-out (LIFO) stacks associated with it. A stack is used to store parameters and returning addresses for procedure and system calls. ...
Operating Systems
... Learn the links between the abstract concepts and the concrete implementations Use the tools that get used building an Operating System CPSC 457 - Tyson Kendon 2016 ...
... Learn the links between the abstract concepts and the concrete implementations Use the tools that get used building an Operating System CPSC 457 - Tyson Kendon 2016 ...
Operating System
... 1. Single-user, dedicated. Previously thought as individuals have sole use of computer, do not need advanced CPU utilization, protection features (see Fig. 1.3). 2. Not still true. May run several different types of OS (Windows, Mac OS X, UNIX, and Linux) which offer multitasking and virtual memory ...
... 1. Single-user, dedicated. Previously thought as individuals have sole use of computer, do not need advanced CPU utilization, protection features (see Fig. 1.3). 2. Not still true. May run several different types of OS (Windows, Mac OS X, UNIX, and Linux) which offer multitasking and virtual memory ...
Threading
... own resources allocated by the operating system. Resources include memory, file handles, sockets, device handles, and windows. Processes do not share address spaces or file resources except through explicit methods such as inheriting file handles or shared memory segments, or mapping the same file i ...
... own resources allocated by the operating system. Resources include memory, file handles, sockets, device handles, and windows. Processes do not share address spaces or file resources except through explicit methods such as inheriting file handles or shared memory segments, or mapping the same file i ...
OperatingSystems_FA15_4_Threads
... User-level threads managed by user-space thread library. Does not require Kernel mode privileges and does not need to switch to Kernel mode for Thread Management. User Thread Manager scheduler does not affect System Kernel level processes. User Thread environment in the Threads Library, not in Kerne ...
... User-level threads managed by user-space thread library. Does not require Kernel mode privileges and does not need to switch to Kernel mode for Thread Management. User Thread Manager scheduler does not affect System Kernel level processes. User Thread environment in the Threads Library, not in Kerne ...
Electrical Engineering and Computer Science Department Technical
... As parallelism continues to increase in ubiquity—from mobile devices and GPUs to datacenters and supercomputers—parallel runtime systems occupy an increasingly important role in the system software stack. The needs of parallel runtimes and the increasingly sophisticated languages and compilers they ...
... As parallelism continues to increase in ubiquity—from mobile devices and GPUs to datacenters and supercomputers—parallel runtime systems occupy an increasingly important role in the system software stack. The needs of parallel runtimes and the increasingly sophisticated languages and compilers they ...
the thread - Bilkent University Computer Engineering Department
... • thread-local: global inside the thread (thread-wide global), but not global for the whole process. Other threads can not access it. But all functions of the thread can. • But we don’t have language support to define such variables. – C can not do that. • Therefore thread API has special functions ...
... • thread-local: global inside the thread (thread-wide global), but not global for the whole process. Other threads can not access it. But all functions of the thread can. • But we don’t have language support to define such variables. – C can not do that. • Therefore thread API has special functions ...
Design Tradeoffs For Software
... good for studying the components of a computer memory systems like TLBs. a sequence of memory references to the simulation model to mimic the way that a real processor might exercise the design. ...
... good for studying the components of a computer memory systems like TLBs. a sequence of memory references to the simulation model to mimic the way that a real processor might exercise the design. ...
Systematic setup of compartmentalised systems on the seL4
... system hardware and careful design and verification of the controlling software. When following a security architecture like MILS [AFOTH06] a microkernel controls the computer’s central processing unit. The microkernel abstracts hardware protection mechanisms and provides compartments that are perfe ...
... system hardware and careful design and verification of the controlling software. When following a security architecture like MILS [AFOTH06] a microkernel controls the computer’s central processing unit. The microkernel abstracts hardware protection mechanisms and provides compartments that are perfe ...
slide
... A saved context when not running – a separate program counter An execution stack Some static storage for local variables for this thread Access to memory and resources of its process, shared with all other threads in that process (global variables) ...
... A saved context when not running – a separate program counter An execution stack Some static storage for local variables for this thread Access to memory and resources of its process, shared with all other threads in that process (global variables) ...
Threads (and more on Processes)
... extern void thread_yield(); extern int TestAndSet(int &i); /* sets the value of i to 1 and returns the previous value of i. */ void enter_critical_region(int &lock) { while (TestAndSet(lock) == 1) thread_yield(); /* give up processor */ ...
... extern void thread_yield(); extern int TestAndSet(int &i); /* sets the value of i to 1 and returns the previous value of i. */ void enter_critical_region(int &lock) { while (TestAndSet(lock) == 1) thread_yield(); /* give up processor */ ...
Module 7: Process Synchronization
... The flag array is used to indicate if a process is ready to enter the critical section. flag[i] = true implies that process Pi is ready! ...
... The flag array is used to indicate if a process is ready to enter the critical section. flag[i] = true implies that process Pi is ready! ...
3 Threads SMP Microkernel
... – With scheduling done by each processor, kernel-level multithreading must avoid conflicts in scheduling multiple threads from the same process ...
... – With scheduling done by each processor, kernel-level multithreading must avoid conflicts in scheduling multiple threads from the same process ...
Power Point XP
... Can have long-running stateful handlers without freezes Scalable performance on multiple CPUs ...
... Can have long-running stateful handlers without freezes Scalable performance on multiple CPUs ...
Operating System Fundamentals
... available for computers. The most popular operating systems belong to the Microsoft Windows family (such as Windows 98, XP and Vista). Other examples are Unix and Linux, Mac OS X, and specialized operating systems for handheld devices like mobile phones. An operating system is the software that cont ...
... available for computers. The most popular operating systems belong to the Microsoft Windows family (such as Windows 98, XP and Vista). Other examples are Unix and Linux, Mac OS X, and specialized operating systems for handheld devices like mobile phones. An operating system is the software that cont ...