No Slide Title - ECE Users Pages - Georgia Institute of Technology
... 4.6. Attempts to circumvent security Users are prohibited from attempting to circumvent or subvert any system.s security measures. This section does not prohibit use of security tools by personnel authorized by OIT or their unit. 4.6.1. Decoding access control information Users are prohibited from u ...
... 4.6. Attempts to circumvent security Users are prohibited from attempting to circumvent or subvert any system.s security measures. This section does not prohibit use of security tools by personnel authorized by OIT or their unit. 4.6.1. Decoding access control information Users are prohibited from u ...
Document
... – code rigorously developed an analyzed so we can trust that it does all and only what specs say Trusted code establishes foundation upon which untrusted code runs Trusted code establishes security baseline for the whole system In particular, OS can be trusted s/w ...
... – code rigorously developed an analyzed so we can trust that it does all and only what specs say Trusted code establishes foundation upon which untrusted code runs Trusted code establishes security baseline for the whole system In particular, OS can be trusted s/w ...
ICS 143 - Introduction to Operating Systems
... Allows overlap - I/O of one job with computation of another. Introduces notion of a job pool that allows OS choose next job to run so as to increase CPU utilization. ...
... Allows overlap - I/O of one job with computation of another. Introduces notion of a job pool that allows OS choose next job to run so as to increase CPU utilization. ...
Lecture 8 - Bhecker.com
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
Modern Operating System - Tanenbaum solution 3rd
... 1. Multiprogramming is the rapid switching of the CPU between multiple processes in memory. It is commonly used to keep the CPU busy while one or more processes are doing I/O. 2. Input spooling is the technique of reading in jobs, for example, from cards, onto the disk, so that when the currently ex ...
... 1. Multiprogramming is the rapid switching of the CPU between multiple processes in memory. It is commonly used to keep the CPU busy while one or more processes are doing I/O. 2. Input spooling is the technique of reading in jobs, for example, from cards, onto the disk, so that when the currently ex ...
ppt
... were first brought to market in the 1980s. • At one time, these systems were considered appropriate only for desktop publishing and games. • Today they are seen as technology enablers for users with little formal computer education. • Once solely a server operating system, Linux holds the promise of ...
... were first brought to market in the 1980s. • At one time, these systems were considered appropriate only for desktop publishing and games. • Today they are seen as technology enablers for users with little formal computer education. • Once solely a server operating system, Linux holds the promise of ...
Commercial Real-Time Operating Systems – An
... POSIX-compliant Unix-like real-time operating system. Microkernel design – kernel provides essential threads and real-time services use of a microkernel allows users (developers) to turn off any functionality they do not require without having to change the OS itself. The system is quite small, fitt ...
... POSIX-compliant Unix-like real-time operating system. Microkernel design – kernel provides essential threads and real-time services use of a microkernel allows users (developers) to turn off any functionality they do not require without having to change the OS itself. The system is quite small, fitt ...
Operating Systems
... memory control info, etc.) transparently to user process. Note on terminology. It’s common to use ‘process’ for task with independent address space, espec. in Unix setting, but this is not a universal definition. Tasks sharing the same address space are called ‘tasks’ (IBM) or ‘threads’ (Unix). But ...
... memory control info, etc.) transparently to user process. Note on terminology. It’s common to use ‘process’ for task with independent address space, espec. in Unix setting, but this is not a universal definition. Tasks sharing the same address space are called ‘tasks’ (IBM) or ‘threads’ (Unix). But ...
Chapter 6: Operating Systems: The Genie in the Computer
... • The proper software drivers must be added to the operating system’s collection of programs. – Device Driver: A program that will allow communication between the operating system and another part of the computer, usually a peripheral device like a printer or scanner. It is an addition to the operat ...
... • The proper software drivers must be added to the operating system’s collection of programs. – Device Driver: A program that will allow communication between the operating system and another part of the computer, usually a peripheral device like a printer or scanner. It is an addition to the operat ...
Operating Systems
... A computer description can be given to provide additional information Computer names must be unique and should be consistent IP addresses are like phone numbers on the network IP addresses must be unique ...
... A computer description can be given to provide additional information Computer names must be unique and should be consistent IP addresses are like phone numbers on the network IP addresses must be unique ...
Module 1: Introduction What is an Operating System?
... • Simple Batch Systems • Multiprogramming Batched Systems • Time-Sharing Systems • Personal-Computer Systems • Parallel Systems • Distributed Systems ...
... • Simple Batch Systems • Multiprogramming Batched Systems • Time-Sharing Systems • Personal-Computer Systems • Parallel Systems • Distributed Systems ...
What is an Operating System?
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
What is an Operating System?
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
... When the operating system finishes the execution of one command, it seeks the next “control statement” from the user’s keyboard ...
Slides for week 2
... Process Vs. Programs: An Analogue A baker (CPU) uses a recipe (program) to transform the baking ingredients (input data), with the aid of cooking utensils and appliances (resources), into a cake (output). We recognize this entire activity as the process - an abstraction of an executing recipe. ...
... Process Vs. Programs: An Analogue A baker (CPU) uses a recipe (program) to transform the baking ingredients (input data), with the aid of cooking utensils and appliances (resources), into a cake (output). We recognize this entire activity as the process - an abstraction of an executing recipe. ...
Abstract View of System Components
... interaction with the computer system. But we can do that with Time Sharing system. A time-shared operating system allows many users to share the computer simultaneously. The CPU is multiplexed among several jobs that are kept in memory and on disk (the CPU is allocated to a job only if the job is in ...
... interaction with the computer system. But we can do that with Time Sharing system. A time-shared operating system allows many users to share the computer simultaneously. The CPU is multiplexed among several jobs that are kept in memory and on disk (the CPU is allocated to a job only if the job is in ...
Standard Operating and Maintenance Procedures
... • Operating system directories are typically placed in the root directory and have appropriate subdirectories under a main directory. – Windows 7 OS system files are contained in the Windows directory, which has subdirectories such as System, System32, and SysWOW64. – Macintosh system files are kept ...
... • Operating system directories are typically placed in the root directory and have appropriate subdirectories under a main directory. – Windows 7 OS system files are contained in the Windows directory, which has subdirectories such as System, System32, and SysWOW64. – Macintosh system files are kept ...
The Operating System (cont.)
... Copyright © 2012 Pearson Education, Inc. publishing as Prentice Hall ...
... Copyright © 2012 Pearson Education, Inc. publishing as Prentice Hall ...
Evolution of Operating Systems
... • Each processor can perform the same functions and share same main memory and I/O facilities (symmetric). • The OS schedule processes/threads across all the processors (real parallelism). • Existence of multiple processors is transparent to the user. • Incremental growth: just add another CPU! • Ro ...
... • Each processor can perform the same functions and share same main memory and I/O facilities (symmetric). • The OS schedule processes/threads across all the processors (real parallelism). • Existence of multiple processors is transparent to the user. • Incremental growth: just add another CPU! • Ro ...
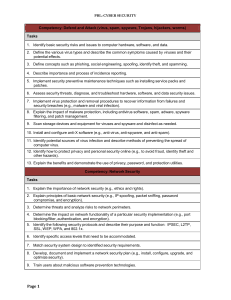
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 16. Develop and document a plan to avoid data loss, including backups and remote storage. Competency: Physical Security Tasks 1. Define physical security. 2. Identify names, purposes, and characteristics of hardware and software security issues including wireless, data, and physical security. 3. Des ...
... 16. Develop and document a plan to avoid data loss, including backups and remote storage. Competency: Physical Security Tasks 1. Define physical security. 2. Identify names, purposes, and characteristics of hardware and software security issues including wireless, data, and physical security. 3. Des ...
Network Security: Intrusion Detection and Protection
... Looks for a fixed sequence of bytes within each packet. To filter traffic inspection the pattern is also usually associated with a particular service and source or destination port. For example it looks for IPv4 packets that use TCP protocol, have destination port of 27015 and contain the string “ab ...
... Looks for a fixed sequence of bytes within each packet. To filter traffic inspection the pattern is also usually associated with a particular service and source or destination port. For example it looks for IPv4 packets that use TCP protocol, have destination port of 27015 and contain the string “ab ...
High Assurance MLS File Service - Center for Computer Systems
... sensitivity level of the source network with the contents of each packet it forwards from lowto-high. The guard then forwards these lowernetwork-labeled (“low-sealed”) packets over the system-high network to another guard at their intended destination. When delivering packets, the destination guard ...
... sensitivity level of the source network with the contents of each packet it forwards from lowto-high. The guard then forwards these lowernetwork-labeled (“low-sealed”) packets over the system-high network to another guard at their intended destination. When delivering packets, the destination guard ...
Introduction to Operating Systems
... • A mechanism by which the processor suspends execution of the current, running program and gives control to the OS • OS saves the state of the interrupted program so that it can be restarted later • OS then takes appropriate action CS-2301, B-Term 2009 ...
... • A mechanism by which the processor suspends execution of the current, running program and gives control to the OS • OS saves the state of the interrupted program so that it can be restarted later • OS then takes appropriate action CS-2301, B-Term 2009 ...