File
... This is a mechanism behind Windows 3.1 and while not in use to real time application for reasons which will become apparent it has been included for reference. ...
... This is a mechanism behind Windows 3.1 and while not in use to real time application for reasons which will become apparent it has been included for reference. ...
Best Practices for Data Sharing in a Grid Distributed
... make solid business decisions. This is true for many SAS customers who look for ways to distribute both their data and or their processing to help them meet ever-shrinking timelines. The performance and success of a solution depends on timely and reliable data access no matter where it resides. Cust ...
... make solid business decisions. This is true for many SAS customers who look for ways to distribute both their data and or their processing to help them meet ever-shrinking timelines. The performance and success of a solution depends on timely and reliable data access no matter where it resides. Cust ...
Hybrid vs. Monolithic OS Kernels
... Fig. 1 shows the memory latency for the A64 in 32-bit mode for Linux. It is typical of all the graphs on this architecture. The stride size is the offset into a fixed array for each access. The small memory size operations were very fast and did not differ between operating systems or hardware platf ...
... Fig. 1 shows the memory latency for the A64 in 32-bit mode for Linux. It is typical of all the graphs on this architecture. The stride size is the offset into a fixed array for each access. The small memory size operations were very fast and did not differ between operating systems or hardware platf ...
LectureNotes - Cabrillo College
... Supports timesharing and multi-user systems An excellent server operating system as it utilizes resources carefully, allowing only the required services to be loaded ...
... Supports timesharing and multi-user systems An excellent server operating system as it utilizes resources carefully, allowing only the required services to be loaded ...
Lecture 4
... Maintains the computers clocks Starts applications Assigns the computers resources, such as devices, programs, data, and information Each time you boot a computer, the kernel and other frequently used operating system instructions are loaded Loading a file means the file is copied from the h ...
... Maintains the computers clocks Starts applications Assigns the computers resources, such as devices, programs, data, and information Each time you boot a computer, the kernel and other frequently used operating system instructions are loaded Loading a file means the file is copied from the h ...
Public Presentation - Academic Conferences
... Adversaries can use 30 + years experience – The threat has only increased with time – Trojan horses – application subversion • Thousands in products, e.g., viruses and “Easter Eggs” ...
... Adversaries can use 30 + years experience – The threat has only increased with time – Trojan horses – application subversion • Thousands in products, e.g., viruses and “Easter Eggs” ...
Chapter 1: Field Guide to Identifying Computers in the Wild
... • Press [Enter] to make the commands go – You need to know the commands or names of executable (program) files for the command line to work properly. ...
... • Press [Enter] to make the commands go – You need to know the commands or names of executable (program) files for the command line to work properly. ...
Dr. Clifford Neuman University of Southern California Information
... Usually IP address and asserted account name. Privileged port means accept asserted identity. If not trusted, request unix password in clear. Kerberos based options available Kerberos based authentication and optional encryption Copyright © 1995-2003 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORN ...
... Usually IP address and asserted account name. Privileged port means accept asserted identity. If not trusted, request unix password in clear. Kerberos based options available Kerberos based authentication and optional encryption Copyright © 1995-2003 Clifford Neuman - UNIVERSITY OF SOUTHERN CALIFORN ...
CS345 02 - Computer Systems
... • Processor’s time is shared among multiple users • Multiple users simultaneously access the system through terminals. ...
... • Processor’s time is shared among multiple users • Multiple users simultaneously access the system through terminals. ...
Course Descriptions (CSE)-2010
... parallel to one or both reference planes, contained by one or both planes, perpendicular to one of the planes, inclined to one plane but parallel to the other plane, inclined to both the planes, true length of a line and its inclinations with reference planes, traces of a line. Projections of Polyhe ...
... parallel to one or both reference planes, contained by one or both planes, perpendicular to one of the planes, inclined to one plane but parallel to the other plane, inclined to both the planes, true length of a line and its inclinations with reference planes, traces of a line. Projections of Polyhe ...
ICT Security
... leave. Passwords should also contain a mixture of numbers, letters (both lower and upper case) and symbols. All staff must respect the need to keep passwords confidential, and switch off computers when they are not in use. Networking software provides the option for password control, and this should ...
... leave. Passwords should also contain a mixture of numbers, letters (both lower and upper case) and symbols. All staff must respect the need to keep passwords confidential, and switch off computers when they are not in use. Networking software provides the option for password control, and this should ...
Operating-System Structures
... concurrently, resources must be allocated to each of them Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code Accounting - To keep track of which users use how ...
... concurrently, resources must be allocated to each of them Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code Accounting - To keep track of which users use how ...
ch21-The_Linux_System
... First developed as a small but self-contained kernel in 1991 by Linus Torvalds, with the major design goal of UNIX compatibility Its history has been one of collaboration by many users from all ...
... First developed as a small but self-contained kernel in 1991 by Linus Torvalds, with the major design goal of UNIX compatibility Its history has been one of collaboration by many users from all ...
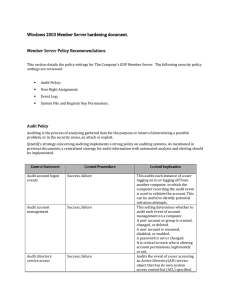
Server hardening - Cisco Security Solutions
... computer to the network can access resources on that computer for which they have permission. Users requiring access to member servers resources should be authenticated. This allows a process to assume the identity of any user and thus gain access to the resources that the user is authorised to acce ...
... computer to the network can access resources on that computer for which they have permission. Users requiring access to member servers resources should be authenticated. This allows a process to assume the identity of any user and thus gain access to the resources that the user is authorised to acce ...
Anti-Virus - F5 Application Brief
... API, is the unifying prevention point. Specialized devices can inject their knowledge by creating, deleting or editing iRules, which are then enforced by the UIE. This functionality can be used to secure anti-virus systems, web services, mobile applications, and nearly any IP based enterprise applic ...
... API, is the unifying prevention point. Specialized devices can inject their knowledge by creating, deleting or editing iRules, which are then enforced by the UIE. This functionality can be used to secure anti-virus systems, web services, mobile applications, and nearly any IP based enterprise applic ...
PPT Chap 1103
... Operating System Components • User Interface: Communicates with users – Text based (Shell) – Graphical user interface (GUI) • Kernel: Performs basic required functions – File manager – Device drivers – Memory manager – Scheduler and dispatcher Copyright © 2012 Pearson Education, Inc. ...
... Operating System Components • User Interface: Communicates with users – Text based (Shell) – Graphical user interface (GUI) • Kernel: Performs basic required functions – File manager – Device drivers – Memory manager – Scheduler and dispatcher Copyright © 2012 Pearson Education, Inc. ...
OPERATING SYSTEMS DESIGN AND IMPLEMENTATION Third
... No process should have to wait forever to enter its critical region. (wait only limited time) No assumptions may be made about speeds or the number of CPUs. (give up CPU while waiting) ...
... No process should have to wait forever to enter its critical region. (wait only limited time) No assumptions may be made about speeds or the number of CPUs. (give up CPU while waiting) ...
Chapter 4 - people.vcu.edu
... • Operating system supports multiple threads of execution within a single process • MS-DOS supports a single thread • UNIX supports multiple user processes but only supports one thread per process • Windows 2000, Solaris, Linux, Mach, and OS/2 support multiple threads ...
... • Operating system supports multiple threads of execution within a single process • MS-DOS supports a single thread • UNIX supports multiple user processes but only supports one thread per process • Windows 2000, Solaris, Linux, Mach, and OS/2 support multiple threads ...
Windows Server 2008 - Information Technology of Falcon High School
... Copyright © 2012 Cengage Learning. All rights reserved. ...
... Copyright © 2012 Cengage Learning. All rights reserved. ...
ch12
... – Using real programs, usually production programs • Run with different configurations of CPUs, operating systems, and other components • Results are called benchmarks ...
... – Using real programs, usually production programs • Run with different configurations of CPUs, operating systems, and other components • Results are called benchmarks ...
file (1.5 MB, ppt)
... based on their priorities UNIX shares memory among processes by dividing RAM into equal-sized pages (e.g., 4K bytes) and allocating them; only those pages of a process that are needed in RAM are loaded from disk while pages of RAM that are not accessed are saved back to disk UNIX shares disk spa ...
... based on their priorities UNIX shares memory among processes by dividing RAM into equal-sized pages (e.g., 4K bytes) and allocating them; only those pages of a process that are needed in RAM are loaded from disk while pages of RAM that are not accessed are saved back to disk UNIX shares disk spa ...