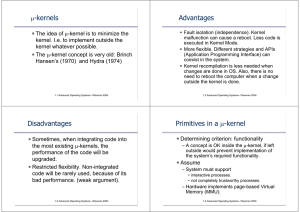
μ-kernels Advantages Disadvantages Primitives in a μ
... The memory models differ in: – What is the maximum virtual address space? – Is the address space segmented or flat? – Does it support the segment model? – Is the TLB tagged? – What is the cache writing policy? • Write-through or write-back? Write-through policy does not require a dirty bit. 1.20 Adv ...
... The memory models differ in: – What is the maximum virtual address space? – Is the address space segmented or flat? – Does it support the segment model? – Is the TLB tagged? – What is the cache writing policy? • Write-through or write-back? Write-through policy does not require a dirty bit. 1.20 Adv ...
Chapter 3
... operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information between processes executing either on the same computer or on different systems tied toge ...
... operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information between processes executing either on the same computer or on different systems tied toge ...
Hassan Al-Makso`s presentation on Making OS Reliable and Secure
... mechanisms for process management, implements interprocess communication, and performs process scheduling. Each I/O device has its own driver that runs as a separate process in its own private address space, protected by the memory management unit (MMU) hardware. The drivers run in user mode and ...
... mechanisms for process management, implements interprocess communication, and performs process scheduling. Each I/O device has its own driver that runs as a separate process in its own private address space, protected by the memory management unit (MMU) hardware. The drivers run in user mode and ...
AOSScheduling
... Give processes lottery tickets for various system resources, such as CPU time. Whenever a scheduling decision has to be made, a lottery ticket is chosen at random, and the process holding that ticket gets the resource. When applied to CPU scheduling, the system might hold a lottery 50 times a secon ...
... Give processes lottery tickets for various system resources, such as CPU time. Whenever a scheduling decision has to be made, a lottery ticket is chosen at random, and the process holding that ticket gets the resource. When applied to CPU scheduling, the system might hold a lottery 50 times a secon ...
Real-Time Operating Systems Lecture for the Embedded Systems
... Small kernel footprint : ~28 KB in size ...
... Small kernel footprint : ~28 KB in size ...
Chapter-3-OpratingSystemSupport
... But network operating system are in wide use for various reasons both technical and non-technical. Users have much invested in their application software; they will not adopt a new operating system that will not run their applications. ...
... But network operating system are in wide use for various reasons both technical and non-technical. Users have much invested in their application software; they will not adopt a new operating system that will not run their applications. ...
Windows Academic Program
... introducing case studies from the Windows kernel into operating system courses ...
... introducing case studies from the Windows kernel into operating system courses ...
system programs
... System programs • Provide a general-purpose lower-level function. System functions include: – file manipulation: create, delete, copy etc. – status info: date, available memory. – program loading and execution. – communication between processes. – Command interpreters (a.k.a. shell programs). The s ...
... System programs • Provide a general-purpose lower-level function. System functions include: – file manipulation: create, delete, copy etc. – status info: date, available memory. – program loading and execution. – communication between processes. – Command interpreters (a.k.a. shell programs). The s ...
Discovering Computers Fundamentals 4th Edition
... in a program that allow users to bypass security controls when accessing a computer resource Spoofing is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network p. 367 ...
... in a program that allow users to bypass security controls when accessing a computer resource Spoofing is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network p. 367 ...
All versions of the Microsoft Windows operating system create
... Operating System Files All versions of the Microsoft Windows operating system create folders on your computer hard drive into which are placed files that the operating system (OS) requires. These folders are most often identified by the names WINDOWS or WINNT. Primarily contained within these folder ...
... Operating System Files All versions of the Microsoft Windows operating system create folders on your computer hard drive into which are placed files that the operating system (OS) requires. These folders are most often identified by the names WINDOWS or WINNT. Primarily contained within these folder ...
Firewall Toolkit (FWTK)
... Tools for Proxying • Many available applications provide proxy capabilities. The major commercial vendors have embraced hybrid technologies that combine proxy and stateful technologies, making it harder to identify when proxy techniques are used in their products. Mergers and acquisitions in the fi ...
... Tools for Proxying • Many available applications provide proxy capabilities. The major commercial vendors have embraced hybrid technologies that combine proxy and stateful technologies, making it harder to identify when proxy techniques are used in their products. Mergers and acquisitions in the fi ...
lect8_9 - Computer and Information Sciences
... Benefits of Threads • Takes less time to create a new thread than a process • Less time to terminate a thread than a process • Less time to switch between two threads within the same process • Since threads within the same process share memory and files, they can communicate with each other withou ...
... Benefits of Threads • Takes less time to create a new thread than a process • Less time to terminate a thread than a process • Less time to switch between two threads within the same process • Since threads within the same process share memory and files, they can communicate with each other withou ...
Tips: To get information about installed OS quickly (for Windows)
... the Applications tab, this tab has the ability to display all programs that are running even if they were started by another user or the operating system itself. To list all processes press “Show processes from all users”. This list indicates the amount of CPU power that the process is currently usi ...
... the Applications tab, this tab has the ability to display all programs that are running even if they were started by another user or the operating system itself. To list all processes press “Show processes from all users”. This list indicates the amount of CPU power that the process is currently usi ...
What is an Operating System?
... Time-Sharing Systems Personal-Computer Systems Parallel Systems Distributed Systems ...
... Time-Sharing Systems Personal-Computer Systems Parallel Systems Distributed Systems ...
Operating-System Structures
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them Many types of resources - CPU cycles, main memory, file storage, I/O devices. Accounting - To keep track of which users use how much and what kinds of computer resources ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them Many types of resources - CPU cycles, main memory, file storage, I/O devices. Accounting - To keep track of which users use how much and what kinds of computer resources ...
Chapter 2: Operating
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
ch2 - EECS User Home Pages
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...