Operating-System - Jyoti Computer Centre
... 61. An operating system is a program that controls the…………of an application program and acts as an……..between the user and………. Operating system is an example of……….software. a) Hardware, System, Variable, Application. b) Interface, Execution, Computer software, system c) Execution, interface, comput ...
... 61. An operating system is a program that controls the…………of an application program and acts as an……..between the user and………. Operating system is an example of……….software. a) Hardware, System, Variable, Application. b) Interface, Execution, Computer software, system c) Execution, interface, comput ...
A real-time operating system
... systems that had been developed for mainframes and minis; minimalistic operating systems were developed, often loaded from ROM and known as monitors. One notable early disk operating system was CP/M, which was supported on many early microcomputers and was closely imitated by Microsoft's MS-DOS, whi ...
... systems that had been developed for mainframes and minis; minimalistic operating systems were developed, often loaded from ROM and known as monitors. One notable early disk operating system was CP/M, which was supported on many early microcomputers and was closely imitated by Microsoft's MS-DOS, whi ...
virtualization
... • Dom0 is in the TCB of DomU because it can access the memory of DomU, which may cause information leakage/modification ...
... • Dom0 is in the TCB of DomU because it can access the memory of DomU, which may cause information leakage/modification ...
Lect0698
... be stored in the register dl (it would not fit in 8 bits), so the behaviour of the int 21h for outputting strings will clearly have to be different to its behaviour for outputting a single character. ...
... be stored in the register dl (it would not fit in 8 bits), so the behaviour of the int 21h for outputting strings will clearly have to be different to its behaviour for outputting a single character. ...
CATCHING EXCEPTIONS
... __except( Filter( GetExceptionCode() ) ) //the filter expression is called & makes decisions based on exception code ...
... __except( Filter( GetExceptionCode() ) ) //the filter expression is called & makes decisions based on exception code ...
Communication - Computer Science Division
... Migration and Local Resources • Types of process-to-resource binding – Binding by identifier (e.g., URL, (IPaddr:Port)) – Binding by value (e.g., standard libraries) – Binding by type (e.g., monitor, printer) ...
... Migration and Local Resources • Types of process-to-resource binding – Binding by identifier (e.g., URL, (IPaddr:Port)) – Binding by value (e.g., standard libraries) – Binding by type (e.g., monitor, printer) ...
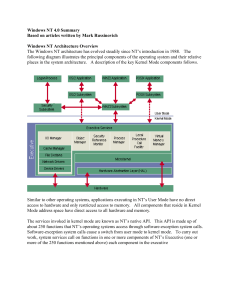
Windows_NT_4
... The Virtual Memory Manager creates and manages address maps for processes. The Virtual Memory Manager also does all physical memory allocation. To improve performance, the VMM implements file memory mapping, memory sharing, and copy-on-write page protection. File memory mapping involves the automati ...
... The Virtual Memory Manager creates and manages address maps for processes. The Virtual Memory Manager also does all physical memory allocation. To improve performance, the VMM implements file memory mapping, memory sharing, and copy-on-write page protection. File memory mapping involves the automati ...
Process Description and Control
... First a program statically consists of a set of instructions that manipulate data, thus the operating system needs to allocate space for its code and data. In addition, the dynamic execution of a program requires a stack that is used to keep track of procedure calls and parameter passing between pro ...
... First a program statically consists of a set of instructions that manipulate data, thus the operating system needs to allocate space for its code and data. In addition, the dynamic execution of a program requires a stack that is used to keep track of procedure calls and parameter passing between pro ...
Protocols used by the virtual private network.
... Internet Protocol Security (IPsec). The main protocol for VPNs is called Internet Protocol Security (IPsec). It isn't actually a protocol in itself. Instead, it is an entire set of protocols. IPsec works at Layer 3 of the OSI model or above. It is the most common suite of protocols used to secure a ...
... Internet Protocol Security (IPsec). The main protocol for VPNs is called Internet Protocol Security (IPsec). It isn't actually a protocol in itself. Instead, it is an entire set of protocols. IPsec works at Layer 3 of the OSI model or above. It is the most common suite of protocols used to secure a ...
1 Introduction C H A P T E R
... of a modern computer and modern operating system. For example, a DECSYSTEM-20 simulator running on Mac OS X can boot TOPS-20, load the source tapes, and modify and compile a new TOPS-20 kernel. An interested student can search the Internet to find the original papers that describe the operating syst ...
... of a modern computer and modern operating system. For example, a DECSYSTEM-20 simulator running on Mac OS X can boot TOPS-20, load the source tapes, and modify and compile a new TOPS-20 kernel. An interested student can search the Internet to find the original papers that describe the operating syst ...
Chapter 9
... You can set up the freeware IDS Snort as a packet sniffer so that you can capture packets and study their contents. Parts of a packet header indicate whether a Windows or Linux system is being used. The TCP flags are used in sequence to create a normal three-way handshake between two computers. By l ...
... You can set up the freeware IDS Snort as a packet sniffer so that you can capture packets and study their contents. Parts of a packet header indicate whether a Windows or Linux system is being used. The TCP flags are used in sequence to create a normal three-way handshake between two computers. By l ...
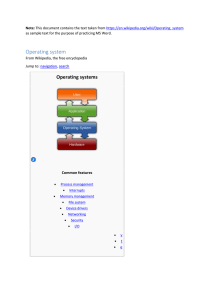
What is an Operating System?
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
... 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video game ...
High Performance Computing Prof. Matthew Jacob Department of Computer Science and Automation
... must be present in the main memory of the computer system, and it is in a state where it is instructions are being fetched from main memory, into the processor and executed, based on the hardware understanding, what those instructions mean. So, that is what it means for a program to be in execution, ...
... must be present in the main memory of the computer system, and it is in a state where it is instructions are being fetched from main memory, into the processor and executed, based on the hardware understanding, what those instructions mean. So, that is what it means for a program to be in execution, ...
Operating Systems
... Limiting times when someone can log in Automatic callback at number prespecified Limited number of login tries A database of all logins Simple login name/password as a trap security personnel ...
... Limiting times when someone can log in Automatic callback at number prespecified Limited number of login tries A database of all logins Simple login name/password as a trap security personnel ...
Computer Organisation Operating Systems
... • Processor’s time is shared among multiple users. • Because of slow human reaction time, a typical user needs 1-2 second to interact with the system. The idle system can be utilised by other user. • The OS is more complicate because a job may be swapped in and out of memory to disk. ...
... • Processor’s time is shared among multiple users. • Because of slow human reaction time, a typical user needs 1-2 second to interact with the system. The idle system can be utilised by other user. • The OS is more complicate because a job may be swapped in and out of memory to disk. ...
Chapter 5 - Input/Output
... cylinder 6 but it goes to 7) – The disk arm is positioned on cylinders by pulses (one pulse per cylinder). When the arm reaches its destination the cylinder number is checked (written when the drive was formatted). If the arm is in a wrong position then a seek error ...
... cylinder 6 but it goes to 7) – The disk arm is positioned on cylinders by pulses (one pulse per cylinder). When the arm reaches its destination the cylinder number is checked (written when the drive was formatted). If the arm is in a wrong position then a seek error ...
Chapter 1 - Computing
... the same time and share resources • Required OS to have an intermediate manager – Oversee the access of each operating system to the server’s physical resources ...
... the same time and share resources • Required OS to have an intermediate manager – Oversee the access of each operating system to the server’s physical resources ...
12_Auth_nemo
... – A information that proves identity – C information stored on computer and used to validate authentication information – F complementation function; f : A C – L functions that prove identity – S functions enabling entity to create, alter information in A or C June 1, 2004 ...
... – A information that proves identity – C information stored on computer and used to validate authentication information – F complementation function; f : A C – L functions that prove identity – S functions enabling entity to create, alter information in A or C June 1, 2004 ...
Processes
... • In the case of weak mobility, it also makes a difference if the migrated code is executed by the target process, or whether a separate process is started, e.g. Java applets sere executed in the browser’s address space. • For strong mobility model, instead of moving a running process, it can also b ...
... • In the case of weak mobility, it also makes a difference if the migrated code is executed by the target process, or whether a separate process is started, e.g. Java applets sere executed in the browser’s address space. • For strong mobility model, instead of moving a running process, it can also b ...
The Top Seven Security Problems of 802.11 Wireless
... network administrators must be conscious of the need to keep up with the latest techniques used in the cat-and-mouse game played out in the site audit. Access points can be deployed in any frequency band defined in 802.11, so it is important that any tools used in audits can scan the entire frequenc ...
... network administrators must be conscious of the need to keep up with the latest techniques used in the cat-and-mouse game played out in the site audit. Access points can be deployed in any frequency band defined in 802.11, so it is important that any tools used in audits can scan the entire frequenc ...
ppt
... L4Linux will use a single-server approach. A single Linux server will run on top of L4, multiplexing a single thread for system calls and page faults. The Linux server maps physical memory into its address space, and acts as the pager for any user processes it creates. The Server cannot directly acc ...
... L4Linux will use a single-server approach. A single Linux server will run on top of L4, multiplexing a single thread for system calls and page faults. The Linux server maps physical memory into its address space, and acts as the pager for any user processes it creates. The Server cannot directly acc ...
Module 4: Processes
... The context (or image) of a process can be described by – contents of main memory – contents of CPU registers – other info (open files, I/O in progress, etc.) Main memory -- three logically distinct regions of memory: – code region: contains executable code (typically read-only) – data region: stora ...
... The context (or image) of a process can be described by – contents of main memory – contents of CPU registers – other info (open files, I/O in progress, etc.) Main memory -- three logically distinct regions of memory: – code region: contains executable code (typically read-only) – data region: stora ...
Operating Systems I: Chapter 4
... Medium-Term schedulers - control the process mix and degree of multiprogramming for interactive time-shared systems – All jobs are accepted (little or no long-term scheduling) – Resource restrictions may not permit all jobs to be in memory concurrently Partially executed processes may be swapped o ...
... Medium-Term schedulers - control the process mix and degree of multiprogramming for interactive time-shared systems – All jobs are accepted (little or no long-term scheduling) – Resource restrictions may not permit all jobs to be in memory concurrently Partially executed processes may be swapped o ...