ARM Based Customizing an Operating System for the Single Board
... separated from the operating system itself. That is, the operating system code runs in a privileged processor mode (referred to as kernel mode), with access to system data and to the hard-ware; applications run in a non-privileged processor mode (called the user mode), with a limited set of interfac ...
... separated from the operating system itself. That is, the operating system code runs in a privileged processor mode (referred to as kernel mode), with access to system data and to the hard-ware; applications run in a non-privileged processor mode (called the user mode), with a limited set of interfac ...
Implementing Processes, Threads, and Resources
... Mode and type of file Number of links to the file File owner’s userid and groupid Size of file (in bytes) Last access and last modified times Number of blocks allocated to the file Pointers to the first twelve blocks Pointers to three additional blocks of pointers ...
... Mode and type of file Number of links to the file File owner’s userid and groupid Size of file (in bytes) Last access and last modified times Number of blocks allocated to the file Pointers to the first twelve blocks Pointers to three additional blocks of pointers ...
Chapter 1 Study Outline
... (1) An intruder who misuses a legitimate program to gain access to a system. (2) Legitimate users who attempt to gain access to files that they should not have access to. D. Access controls. ...
... (1) An intruder who misuses a legitimate program to gain access to a system. (2) Legitimate users who attempt to gain access to files that they should not have access to. D. Access controls. ...
CSC 271 – Software I: Utilities and Internals What Is an Operating
... to build computers for individual users. These became known as PCs, first appearing in the 1970s. • PC operating systems were initially simple systems, lacking protection features of larger ...
... to build computers for individual users. These became known as PCs, first appearing in the 1970s. • PC operating systems were initially simple systems, lacking protection features of larger ...
Operating Systems and File Management
... Boot and Recovery Disks • You can create a custom recovery CD that contains your computer’s current settings and device drivers • Norton Ghost is a product of Symantec, which also provides a more specialized recovery disk called the Symantec Recovery Disk • Certain PC manufacturers have pre-install ...
... Boot and Recovery Disks • You can create a custom recovery CD that contains your computer’s current settings and device drivers • Norton Ghost is a product of Symantec, which also provides a more specialized recovery disk called the Symantec Recovery Disk • Certain PC manufacturers have pre-install ...
Chapter 3: Operating System Structures
... • People use computers for the potential of rapid information processing • There are several measures of performance – throughput – response time • The OS is an overhead function => should not use too much of machine resources • Provide an environment in which programmers can produce solutions in a ...
... • People use computers for the potential of rapid information processing • There are several measures of performance – throughput – response time • The OS is an overhead function => should not use too much of machine resources • Provide an environment in which programmers can produce solutions in a ...
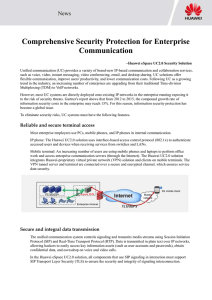
Comprehensive Security Protection for
... However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise may reach 15%. For this reason, info ...
... However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise may reach 15%. For this reason, info ...
Introduction to Computer and Operating Systems
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
Introduction to Computer and Operating Systems
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
... – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what – User identities (user IDs, security IDs) include name and associated number, one per user – User ID then associated with all fil ...
Database Security
... – site begins by generating a public key and a private key, and sending a request to Verisign, along with the site’s public key – Verisign issues an encrypted certificate to the site; Certificate also contains the site’s public key – Customer browser asks the site for its Verisign certificate; recei ...
... – site begins by generating a public key and a private key, and sending a request to Verisign, along with the site’s public key – Verisign issues an encrypted certificate to the site; Certificate also contains the site’s public key – Customer browser asks the site for its Verisign certificate; recei ...
Document
... case, the UNIX prompt will be returned. Alternatively, there may already be some files inserted by the System Administrator when your account was created. ls does not, in fact, cause all the files in your home directory to be listed, but only those ones whose name does not begin with a dot (.) Files ...
... case, the UNIX prompt will be returned. Alternatively, there may already be some files inserted by the System Administrator when your account was created. ls does not, in fact, cause all the files in your home directory to be listed, but only those ones whose name does not begin with a dot (.) Files ...
ITE-II-ch13
... A hot-swap component has the capability to be added and removed from a computer while the computer is running and have the operating system automatically recognize the change. Warm swaps are generally done in conjunction with the failure of a hard drive. In this case, it is necessary to shut down th ...
... A hot-swap component has the capability to be added and removed from a computer while the computer is running and have the operating system automatically recognize the change. Warm swaps are generally done in conjunction with the failure of a hard drive. In this case, it is necessary to shut down th ...
Chapter 13 Troubleshooting the Operating System
... A hot-swap component has the capability to be added and removed from a computer while the computer is running and have the operating system automatically recognize the change. Warm swaps are generally done in conjunction with the failure of a hard drive. In this case, it is necessary to shut down th ...
... A hot-swap component has the capability to be added and removed from a computer while the computer is running and have the operating system automatically recognize the change. Warm swaps are generally done in conjunction with the failure of a hard drive. In this case, it is necessary to shut down th ...
View
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
... Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them ...
- Mitra.ac.in
... journaling file systems are also typically faster than non-journaling systems, as updates proceed much faster when they are applied to the in-memory journal rather than directly to the on-disk data structures. ...
... journaling file systems are also typically faster than non-journaling systems, as updates proceed much faster when they are applied to the in-memory journal rather than directly to the on-disk data structures. ...
Threat Intel Sharing: Deciphering the APTs secret handshakes
... What are the next steps? Try to understand who is interested in you Not always necessary to get 100% attribution Understand that once your are targeted by APT, you ...
... What are the next steps? Try to understand who is interested in you Not always necessary to get 100% attribution Understand that once your are targeted by APT, you ...
Tutorial 2: Question 1: The services and functions provided by an
... The services and functions provided by an operating system can be divided into two main categories. Briefly describe the two categories and discuss how they differ. Question 2: Describe three general methods for passing parameters to the operating system. Question 3: Describe how you could obtain a ...
... The services and functions provided by an operating system can be divided into two main categories. Briefly describe the two categories and discuss how they differ. Question 2: Describe three general methods for passing parameters to the operating system. Question 3: Describe how you could obtain a ...
What is an Operating System?
... do not run all the time. Also, can emulate: Cygwin/MKS are not OS; they are UNIX-like toolsets for Windows. The drivers that come with peripherals: those enable new hardware to be used by OS, but are OS extensions, not the OS itself. Like browser plugin vs. browser itself. Software that enables ...
... do not run all the time. Also, can emulate: Cygwin/MKS are not OS; they are UNIX-like toolsets for Windows. The drivers that come with peripherals: those enable new hardware to be used by OS, but are OS extensions, not the OS itself. Like browser plugin vs. browser itself. Software that enables ...
Slide Set 7
... pipes and network connections, because these use file descriptors. Associates an I/O stream with the descriptor. ...
... pipes and network connections, because these use file descriptors. Associates an I/O stream with the descriptor. ...
Operating System
... Early operating systems were custom-designed by each computer manufacturer to run on their hardware. The competition was in features of both the operating system and the underlying computer hardware. The features have been evolving from very rudimentary ones such as the ability of automatic loading ...
... Early operating systems were custom-designed by each computer manufacturer to run on their hardware. The competition was in features of both the operating system and the underlying computer hardware. The features have been evolving from very rudimentary ones such as the ability of automatic loading ...
Networking Security
... guessing all possible user IDs using a false password. • If an error message is returned indicating that the user ID is valid, they will store that to a file, and reverse the process and guessing the password for the successful ID they just obtained. ...
... guessing all possible user IDs using a false password. • If an error message is returned indicating that the user ID is valid, they will store that to a file, and reverse the process and guessing the password for the successful ID they just obtained. ...
Lec1
... is no way for a program to even talk about other program’s addresses; no way for it to touch operating system code or data. Translation also helps with the issue of how to stuff multiple programs into memory. Translation is implemented using some form of table lookup (we’ll discuss various optio ...
... is no way for a program to even talk about other program’s addresses; no way for it to touch operating system code or data. Translation also helps with the issue of how to stuff multiple programs into memory. Translation is implemented using some form of table lookup (we’ll discuss various optio ...
chapter4
... • In paging, memory is divided into equally sized sections called frames. • The program is divided into equally sized sections called pages. • The size of a page and a frame is usually the same and equal to the size of the block used by the system to retrieve information from a storage device. ...
... • In paging, memory is divided into equally sized sections called frames. • The program is divided into equally sized sections called pages. • The size of a page and a frame is usually the same and equal to the size of the block used by the system to retrieve information from a storage device. ...