Android Reverse Engineering
... Malware is a piece of code which changes the behavior of either the operating system kernel or some security sensitive applications, without a user consent and in such a way that it is then impossible to detect those changes using a documented features of the operating system or the application.[2] ...
... Malware is a piece of code which changes the behavior of either the operating system kernel or some security sensitive applications, without a user consent and in such a way that it is then impossible to detect those changes using a documented features of the operating system or the application.[2] ...
... In most computer operating systems, the kernel is the central component. It is the bridge between the user and applications and the computer hardware. It also is the mechanism that allows the computer to handle multiple users and multiple tasks simultaneously. The types of kernels are the monolithic ...
Proceedings of the 9th USENIX Security Symposium USENIX Association Denver, Colorado, USA
... cameras, and even game consoles are identi able. Many of these systems, like routers, are important parts of the Internet infrastructure, and compromising infrastructure is a more serious problem than compromising end hosts. Therefore a general mechanism to protect any system is needed. Some people ...
... cameras, and even game consoles are identi able. Many of these systems, like routers, are important parts of the Internet infrastructure, and compromising infrastructure is a more serious problem than compromising end hosts. Therefore a general mechanism to protect any system is needed. Some people ...
ppt
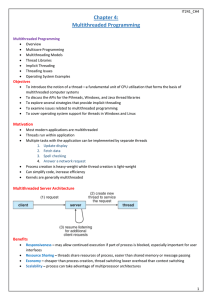
... Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
... Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
ch4-v2
... Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
... Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
Capture the flag for education and mentoring
... generates multiple representations of the same characters. As an example the slash (“/”) is represented by “%c0%af” in Unicode. So normally when a user types this as their URL into a web browser: “http://192.168.1.1//scripts/../../winnt/system32/cmd.exe?/c+dir+c:\” the IIS server would recognize thi ...
... generates multiple representations of the same characters. As an example the slash (“/”) is represented by “%c0%af” in Unicode. So normally when a user types this as their URL into a web browser: “http://192.168.1.1//scripts/../../winnt/system32/cmd.exe?/c+dir+c:\” the IIS server would recognize thi ...
Week_3 Operating system File
... memory and the resources of the process to which they belong. It allows an application to have several different threads of activity within the same address space. Economy: Allocating memory and resources for process creation is costly, it is more economical to create and context-switch threads. ...
... memory and the resources of the process to which they belong. It allows an application to have several different threads of activity within the same address space. Economy: Allocating memory and resources for process creation is costly, it is more economical to create and context-switch threads. ...
Module 6: CPU Scheduling
... jumping to the proper location in the user program to restart that program ...
... jumping to the proper location in the user program to restart that program ...
Chapter 10: Mass-Storage Structure
... a network rather than over a local connection (such as a bus) ...
... a network rather than over a local connection (such as a bus) ...
Chapter 10: Mass-Storage Systems
... a network rather than over a local connection (such as a bus) ...
... a network rather than over a local connection (such as a bus) ...
ppt
... Thread creation is done through clone() system call clone() allows a child task to share the address space ...
... Thread creation is done through clone() system call clone() allows a child task to share the address space ...
Threads
... Supported by the Kernel Kernel threads is slower to create and manage than user threads If a thread performs a blocking system call, the kernel can schedule ...
... Supported by the Kernel Kernel threads is slower to create and manage than user threads If a thread performs a blocking system call, the kernel can schedule ...
Chapter 3
... But if we want to start several processes, then the running program in CPU (current process) has to be stopped for a while and other program (process) has to run in CPU. – Process management becomes an important issue – To do process switch, we have to save the state/context (register values) of the ...
... But if we want to start several processes, then the running program in CPU (current process) has to be stopped for a while and other program (process) has to run in CPU. – Process management becomes an important issue – To do process switch, we have to save the state/context (register values) of the ...
Multithreaded Programming
... To examine issues related to multithreaded programming To cover operating system support for threads in Windows and Linux ...
... To examine issues related to multithreaded programming To cover operating system support for threads in Windows and Linux ...
Chapter 10: Mass-Storage Systems
... a network rather than over a local connection (such as a bus) ...
... a network rather than over a local connection (such as a bus) ...
ch04
... Thread creation is done through clone() system call clone() allows a child task to share the address space ...
... Thread creation is done through clone() system call clone() allows a child task to share the address space ...
Chapter 9: Virtual Memory
... Used up by process pages Also in demand from the kernel, I/O buffers, etc How much to allocate to each? Page replacement – find some page in memory, but not really in ...
... Used up by process pages Also in demand from the kernel, I/O buffers, etc How much to allocate to each? Page replacement – find some page in memory, but not really in ...
ppt
... then no other processes can be executing in their critical sections 2. Progress - If no process is executing in its critical section and there exist some processes that wish to enter their critical section, then the selection of the processes that will enter the critical section next cannot be postp ...
... then no other processes can be executing in their critical sections 2. Progress - If no process is executing in its critical section and there exist some processes that wish to enter their critical section, then the selection of the processes that will enter the critical section next cannot be postp ...
NAVAL POSTGRADUATE SCHOOL
... images of itself allows efficient testing of differing design decisions of system programs. In order to create multiple running simulated copies on a single host machine, IBM developed a construct it called the Control Program or CP for short. IBM also developed a simple single user operating system ...
... images of itself allows efficient testing of differing design decisions of system programs. In order to create multiple running simulated copies on a single host machine, IBM developed a construct it called the Control Program or CP for short. IBM also developed a simple single user operating system ...
CS370: Operating Systems [Spring 2017] Dept. Of Computer
... you don’t have the discipline to show up, you will most likely not have the discipline to catch up ...
... you don’t have the discipline to show up, you will most likely not have the discipline to catch up ...
Chapter 9: Virtual Memory
... Used up by process pages Also in demand from the kernel, I/O buffers, etc How much to allocate to each? Page replacement – find some page in memory, but not really in ...
... Used up by process pages Also in demand from the kernel, I/O buffers, etc How much to allocate to each? Page replacement – find some page in memory, but not really in ...



















![CS370: Operating Systems [Spring 2017] Dept. Of Computer](http://s1.studyres.com/store/data/017525483_1-ea24308b61da8fee3e73be7a64a63be6-300x300.png)

