Operating System Structure
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
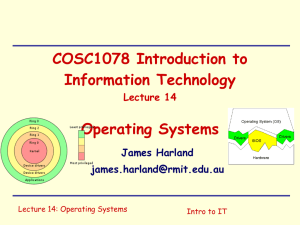
Operating Systems
... Must be done in groups of 2 or 3 Can change groups from Assignment 1 (if you wish) Must have a blog on Blackboard Lecture 14: Operating Systems ...
... Must be done in groups of 2 or 3 Can change groups from Assignment 1 (if you wish) Must have a blog on Blackboard Lecture 14: Operating Systems ...
My Problems: 1. Suppose that it is time for the operating system to
... 3.5 What is the purpose of the command interpreter? Why is it usually separate from the kernel? Answer: It reads commands from the user or from a file of commands and executes them, usually by turning them into one or more system calls. It is usually not part of the kernel since the command interpre ...
... 3.5 What is the purpose of the command interpreter? Why is it usually separate from the kernel? Answer: It reads commands from the user or from a file of commands and executes them, usually by turning them into one or more system calls. It is usually not part of the kernel since the command interpre ...
Intro to CS162
... • Many of you will create systems that utilize the core concepts in operating systems. – Whether you build software or hardware – The concepts and design patterns appear at many levels ...
... • Many of you will create systems that utilize the core concepts in operating systems. – Whether you build software or hardware – The concepts and design patterns appear at many levels ...
Chapter 2
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
Chapter 2 - cse.sc.edu
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
Chapter 1 Bootstrap
... 8088, a virtual address consists of a 16-bit segment register combined with a 16-bit general-purpose register, for example 0x8765:0x4321, and translates to a 20-bit physical address sent to the memory chips, in this case 0x87650+0x4321 = 0x8b971. PC BIOSes guarantee to copy the boot sector to physi ...
... 8088, a virtual address consists of a 16-bit segment register combined with a 16-bit general-purpose register, for example 0x8765:0x4321, and translates to a 20-bit physical address sent to the memory chips, in this case 0x87650+0x4321 = 0x8b971. PC BIOSes guarantee to copy the boot sector to physi ...
Operating System Structure
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
... Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system Block and stack methods do not limit the number or length of ...
Chapter 5 - Nawar.us
... individuals should back up their PC occasionally and all important files each time they are modified. ...
... individuals should back up their PC occasionally and all important files each time they are modified. ...
B - Chulmleigh ICT Department
... • Make appropriate improvements to solutions based on feedback received, and comment on the success of the solution ...
... • Make appropriate improvements to solutions based on feedback received, and comment on the success of the solution ...
Virtual Machine Systems
... – More than one instance of that operating system run on the same hardware at the same time? – More than one different operating system can share the same hardware at the same time? ...
... – More than one instance of that operating system run on the same hardware at the same time? – More than one different operating system can share the same hardware at the same time? ...
Operating Systems and File Management
... 042200 Today’s popular operating systems include Windows, Mac OS, Linux, Android, and iOS. Each has strengths and weaknesses that are important to understand. Which of the following statements is correct? A. iOS is built on the Windows kernel, so it is ideal for smartphones because it has good r ...
... 042200 Today’s popular operating systems include Windows, Mac OS, Linux, Android, and iOS. Each has strengths and weaknesses that are important to understand. Which of the following statements is correct? A. iOS is built on the Windows kernel, so it is ideal for smartphones because it has good r ...
Chapter 1 - PowerPoint
... Symmetric multiprocessing (SMP) Each processor runs an identical copy of the operating system. Many processes can run at once without performance deterioration. Most modern operating systems support SMP Asymmetric multiprocessing Each processor is assigned a specific task; master process ...
... Symmetric multiprocessing (SMP) Each processor runs an identical copy of the operating system. Many processes can run at once without performance deterioration. Most modern operating systems support SMP Asymmetric multiprocessing Each processor is assigned a specific task; master process ...
Operating System Support for Virtual Machines
... • Restricts the set of system calls allowed by guest OS • VMM uses “ptrace” to mediate access between guest machine process and host OS. * ptrace is a system call to observe and control another process, and examine and change its core image and registers. It is primarily used to implement breakpoint ...
... • Restricts the set of system calls allowed by guest OS • VMM uses “ptrace” to mediate access between guest machine process and host OS. * ptrace is a system call to observe and control another process, and examine and change its core image and registers. It is primarily used to implement breakpoint ...
Chapter 6: Operating Systems: The Genie in the Computer
... • Compatibility: Before you purchase software, examine the box. It will tell you which operating system and which version of the operating system is required. • Compatibility problems may arise if an operating system is updated. One of two things might happen after updating: 1. The operating system ...
... • Compatibility: Before you purchase software, examine the box. It will tell you which operating system and which version of the operating system is required. • Compatibility problems may arise if an operating system is updated. One of two things might happen after updating: 1. The operating system ...
Week-2
... The operating system is responsible for the following activities in connection with process management: Creating and deleting both user and system processes Suspending and resuming processes ...
... The operating system is responsible for the following activities in connection with process management: Creating and deleting both user and system processes Suspending and resuming processes ...
An Introduction to Linux Operating System
... the whole computer. It provides resources to all other programs that you run under Linux, and manages all other programs as they run. The kernel includes the code that performs certain specialized tasks, including TCP/IP networking. The kernel design is modular, so that the actual OS code is ver ...
... the whole computer. It provides resources to all other programs that you run under Linux, and manages all other programs as they run. The kernel includes the code that performs certain specialized tasks, including TCP/IP networking. The kernel design is modular, so that the actual OS code is ver ...
ppt
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
I/O devices
... Block at once, not individual locations Write through is impractical Use write-back Dirty bit in PTE set when page is written ...
... Block at once, not individual locations Write through is impractical Use write-back Dirty bit in PTE set when page is written ...
Identify Steps in the Startup Process
... hardware and loads the operating system, completes hardware setup, and produces a fully functional operating system. ...
... hardware and loads the operating system, completes hardware setup, and produces a fully functional operating system. ...
the case for embedded linux
... Linux systems to do the graphics processing for the movie “Titanic”. The Case For Linux Linux is an operating system that is similar to Unix, but is a completely independent product. It has been or is being ported to run on many processors and scales well from small embedded systems to the HP IA-64 ...
... Linux systems to do the graphics processing for the movie “Titanic”. The Case For Linux Linux is an operating system that is similar to Unix, but is a completely independent product. It has been or is being ported to run on many processors and scales well from small embedded systems to the HP IA-64 ...
ch21-The_Linux_System
... schedules processes and provides interprocess communication To look at memory management in Linux ...
... schedules processes and provides interprocess communication To look at memory management in Linux ...
Low-level formatting or physical formatting
... (a) The first step is Partition the disk into one or more groups of cylinders. Among the partitions, one partition can hold a copy of the OS‘s executable code, while another holds user files. (b) The second step is logical formatting .The operating system stores the initial file-system data structur ...
... (a) The first step is Partition the disk into one or more groups of cylinders. Among the partitions, one partition can hold a copy of the OS‘s executable code, while another holds user files. (b) The second step is logical formatting .The operating system stores the initial file-system data structur ...