Threads, SMP, and Microkernels
... ▫ Changes needed to port the system to a new processor is changed in the microkernel - not in the other services ...
... ▫ Changes needed to port the system to a new processor is changed in the microkernel - not in the other services ...
Module 4: Processes
... Takes less time to create a new thread than a process Less time to terminate a thread than a process ...
... Takes less time to create a new thread than a process Less time to terminate a thread than a process ...
sem1 - Devi Ahilya Vishwavidyalaya
... 2. To understand the philosophy, mechanism and principles of operation of corporate world so that they are aware about their career and performance 3. To prepare individuals suitable for better performance Course Description : The course is specially meant for Development of personality, imparting o ...
... 2. To understand the philosophy, mechanism and principles of operation of corporate world so that they are aware about their career and performance 3. To prepare individuals suitable for better performance Course Description : The course is specially meant for Development of personality, imparting o ...
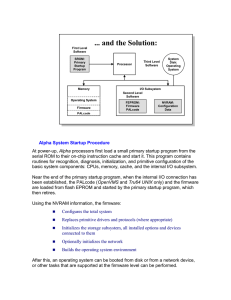
Alpha System Startup Procedure
... protocols are installed at the operating system level rather than at the firmware level. Test routines and exercisers are useful tools for checking the hardware to find or exclude hardware errors in case of trouble. ...
... protocols are installed at the operating system level rather than at the firmware level. Test routines and exercisers are useful tools for checking the hardware to find or exclude hardware errors in case of trouble. ...
Threads, SMP, and Microkernels
... – Changes needed to port the system to a new processor is changed in the microkernel not in the other services ...
... – Changes needed to port the system to a new processor is changed in the microkernel not in the other services ...
Computer Software - Welcome to the UNC Department of
... • How can something as simple-minded as a processor and memory present you with something as rich as the Mac or Windows GUI? COMP 4—Power Tools for the Mind ...
... • How can something as simple-minded as a processor and memory present you with something as rich as the Mac or Windows GUI? COMP 4—Power Tools for the Mind ...
1.01 - Kau
... Timesharing (multitasking) is logical extension in which CPU switches jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
... Timesharing (multitasking) is logical extension in which CPU switches jobs so frequently that users can interact with each job while it is running, creating interactive computing ...
Slide 1
... OS, Linux, Android, and Google Chrome. Each has strengths and weaknesses that are important to understand. Which of the following statements is correct? – A. Google Chrome is built on the Windows kernel, so it is ideal for netbooks because it has good resistance to malware. – B. If you don’t like th ...
... OS, Linux, Android, and Google Chrome. Each has strengths and weaknesses that are important to understand. Which of the following statements is correct? – A. Google Chrome is built on the Windows kernel, so it is ideal for netbooks because it has good resistance to malware. – B. If you don’t like th ...
CS3204 Operating Systems - Spring 2001 Instructor: Dr. Craig A
... Multiprogramming Batch OS Simulation Assigned: Monday, Feb. 26 ...
... Multiprogramming Batch OS Simulation Assigned: Monday, Feb. 26 ...
Course outline - Fiji National University | E
... Trade Diploma in Applied Computing programme. This unit is a core unit for the students who have completed Systems Support. 2.0 Unit Description This unit offers students an understanding of a typical internal structure of a multi-user system and sufficient experience with the use of both single and ...
... Trade Diploma in Applied Computing programme. This unit is a core unit for the students who have completed Systems Support. 2.0 Unit Description This unit offers students an understanding of a typical internal structure of a multi-user system and sufficient experience with the use of both single and ...
Operating Systems
... All I/O instructions are privileged instructions. Must ensure that a user program could never gain control of the computer in monitor mode (I.e., a user program that, as part of its execution, stores a new address in the interrupt vector). ...
... All I/O instructions are privileged instructions. Must ensure that a user program could never gain control of the computer in monitor mode (I.e., a user program that, as part of its execution, stores a new address in the interrupt vector). ...
Chapter 4
... to use the Open and Save dialog boxes in a typical Windows application. Take time to show all the information the Save dialog box provides—location for the file, file name, and file type—or use Figures 4-33 and 4-35. The best way to understand how to manage files using the Open, Save, and Save As co ...
... to use the Open and Save dialog boxes in a typical Windows application. Take time to show all the information the Save dialog box provides—location for the file, file name, and file type—or use Figures 4-33 and 4-35. The best way to understand how to manage files using the Open, Save, and Save As co ...
Evolution of the Windows Kernel Architecture
... Kernel Architect at Microsoft for over 13 years Managed platform-independent kernel development in Win2K/XP Working on multi-core & heterogeneous parallel computing support Architect for UMS in Windows 7 / Windows Server 2008 R2 ...
... Kernel Architect at Microsoft for over 13 years Managed platform-independent kernel development in Win2K/XP Working on multi-core & heterogeneous parallel computing support Architect for UMS in Windows 7 / Windows Server 2008 R2 ...
View
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
Module 3: Operating
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
Chapter 3: Operating-System Structures Common System
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. ■ A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. ■ A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
Introduction - Computer Science
... sharing: how are resources shared across users? naming: how are resources named (by users or programs)? security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happen ...
... sharing: how are resources shared across users? naming: how are resources named (by users or programs)? security: how is the integrity of the OS and its resources ensured? protection: how is one user/program protected from another? performance: how do we make it all go fast? reliability: what happen ...
Understanding Computers, Chapter 5
... – Many variations of UNIX are in use today – Multiuser, multitasking operating system – More expensive, requires a higher level of PC knowledge, and tends to be harder to install, maintain, and upgrade than most other operating systems – “UNIX” initially referred to the original UNIX operating syste ...
... – Many variations of UNIX are in use today – Multiuser, multitasking operating system – More expensive, requires a higher level of PC knowledge, and tends to be harder to install, maintain, and upgrade than most other operating systems – “UNIX” initially referred to the original UNIX operating syste ...
1. A(n) ______ is the unit of work in a system. A) process B
... A) gathers together multiple CPUs to accomplish computational work B) is an operating system that provides file sharing across a network C) is used when rigid time requirements are present D) can only operate one application at a time Ans: A 21. An initial bootstrap program is in the form of random- ...
... A) gathers together multiple CPUs to accomplish computational work B) is an operating system that provides file sharing across a network C) is used when rigid time requirements are present D) can only operate one application at a time Ans: A 21. An initial bootstrap program is in the form of random- ...
BackDoors
... One of the first and oldest methods of intruders used to gain not only access to a Unix machine but backdoors was to run a password cracker. This uncovers weak passworded accounts. All these new accounts are now possible backdoors into a machine even if the system administrator locks out the intrude ...
... One of the first and oldest methods of intruders used to gain not only access to a Unix machine but backdoors was to run a password cracker. This uncovers weak passworded accounts. All these new accounts are now possible backdoors into a machine even if the system administrator locks out the intrude ...
Slide 1
... containing the operating system files needed to boot your computer without accessing the hard disk A recovery disk is a bootable CD, DVD, or other media that contains a complete copy of your computer’s hard disk as it existed when the computer was new ...
... containing the operating system files needed to boot your computer without accessing the hard disk A recovery disk is a bootable CD, DVD, or other media that contains a complete copy of your computer’s hard disk as it existed when the computer was new ...
CS 5204 Operating Systems Fall 2005
... the hardware is based on the assumption that it is possible both to define abstractions that are appropriate for all areas and to implement them to perform efficiently in all situations. We believe that the fallacy of this quixotic goal is self-evident, and that the OS problems of the last two decad ...
... the hardware is based on the assumption that it is possible both to define abstractions that are appropriate for all areas and to implement them to perform efficiently in all situations. We believe that the fallacy of this quixotic goal is self-evident, and that the OS problems of the last two decad ...
Abstract View of System Components
... logical conclusion. It treats hardware and the OS kernel as though they were all hardware. A virtual machine provides an interface identical to the underlying bare hardware. The operating system creates the illusion of multiple processes, each executing on its own processor with its own (virtual ...
... logical conclusion. It treats hardware and the OS kernel as though they were all hardware. A virtual machine provides an interface identical to the underlying bare hardware. The operating system creates the illusion of multiple processes, each executing on its own processor with its own (virtual ...