The Theory of Polynomial Functors
... thinking you could begin with a little starter. How would you like to explore the connection between polynomial and strict polynomial functors?” Not knowing better, we acquiesced, mainly because the word “polynomial” did not ring any alarm bells. It thus all began like an appetiser. It ended up a do ...
... thinking you could begin with a little starter. How would you like to explore the connection between polynomial and strict polynomial functors?” Not knowing better, we acquiesced, mainly because the word “polynomial” did not ring any alarm bells. It thus all began like an appetiser. It ended up a do ...
pdf
... is given, and synthesizing programs from existing programs along with a fully or partially available new specification. In approaches where the entire specification must be available, changes in specification, e.g., addition of a new property, requires us to begin from scratch. By contrast, in the l ...
... is given, and synthesizing programs from existing programs along with a fully or partially available new specification. In approaches where the entire specification must be available, changes in specification, e.g., addition of a new property, requires us to begin from scratch. By contrast, in the l ...
4 slides/page
... • Step 1: Find suitable moduli m1, . . . , mn so that mi’s are relatively prime and m1 · · · mn is bigger than the answer. • Step 2: Perform all the operations mod mj , j = 1, . . . , n. ◦ This means we’re working with much smaller numbers (no bigger than mj ) ◦ The operations are much faster ◦ Can ...
... • Step 1: Find suitable moduli m1, . . . , mn so that mi’s are relatively prime and m1 · · · mn is bigger than the answer. • Step 2: Perform all the operations mod mj , j = 1, . . . , n. ◦ This means we’re working with much smaller numbers (no bigger than mj ) ◦ The operations are much faster ◦ Can ...
KMS states on self-similar groupoid actions
... Note: it suffices to verify the above for analytic elements that span a dense subalgebra, In our case, the spanning set {sµ ug sν∗ : µ, ν ∈ E ∗ , g ∈ G and s(µ) = g · s(ν)}. ...
... Note: it suffices to verify the above for analytic elements that span a dense subalgebra, In our case, the spanning set {sµ ug sν∗ : µ, ν ∈ E ∗ , g ∈ G and s(µ) = g · s(ν)}. ...
Worksheet 61 (11
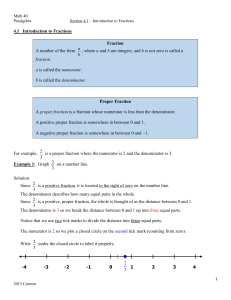
... Warm-up 2. a) The number of bacteria present in a certain culture after t hours is given by the equation Q = Q0 e0.3t, where Q0 represents the number of bacteria initially. If 18,149 bacteria are present after 6 hours, find how many bacteria were present in the culture initially. ...
... Warm-up 2. a) The number of bacteria present in a certain culture after t hours is given by the equation Q = Q0 e0.3t, where Q0 represents the number of bacteria initially. If 18,149 bacteria are present after 6 hours, find how many bacteria were present in the culture initially. ...
Stochastic Search and Surveillance Strategies for
... [1]. V. Srivastava and F. Bullo. Knapsack problems with sigmoid utility: Approximation algorithms via hybrid optimization. European Journal of Operational Research, October 2012. Sumitted. [2]. L. Carlone, V. Srivastava, F. Bullo, and G. C. Calafiore. Distributed random convex programming via constr ...
... [1]. V. Srivastava and F. Bullo. Knapsack problems with sigmoid utility: Approximation algorithms via hybrid optimization. European Journal of Operational Research, October 2012. Sumitted. [2]. L. Carlone, V. Srivastava, F. Bullo, and G. C. Calafiore. Distributed random convex programming via constr ...