DECsystem-10 PROLOG USER`S MANUAL
... interpreted, while any directives are obeyed as they are encountered. When the end of the file is found, the interpreter displays on the terminal the time spent for read-in and the number of words occupied by the program. This indicates the completion of the command. In general, this directive can b ...
... interpreted, while any directives are obeyed as they are encountered. When the end of the file is found, the interpreter displays on the terminal the time spent for read-in and the number of words occupied by the program. This indicates the completion of the command. In general, this directive can b ...
CLAN Manual - CHILDES - Carnegie Mellon University
... 7.2.1 Linking to an already existing transcript ...................................................... 50 7.2.2 To create a new transcript ............................................................................. 50 7.2.3 Sparse Annotation .................................... ...
... 7.2.1 Linking to an already existing transcript ...................................................... 50 7.2.2 To create a new transcript ............................................................................. 50 7.2.3 Sparse Annotation .................................... ...
CLAN Manual - CHILDES - Carnegie Mellon University
... Send to Sound Analyzer.................................................................................... 40 6.10 Tiers Menu Items .............................................................................................. 40 6.11 Running CHECK Inside the Editor.............................. ...
... Send to Sound Analyzer.................................................................................... 40 6.10 Tiers Menu Items .............................................................................................. 40 6.11 Running CHECK Inside the Editor.............................. ...
DVTk
... This tool is used for editing DICOM part-10 files and generating test data. It has the capability to: Display all DICOM attributes in tabular format with indicating beginning & ending of sequence items. Add/delete DICOM attributes. Add/delete DICOM sequence attributes and sequence items. Mod ...
... This tool is used for editing DICOM part-10 files and generating test data. It has the capability to: Display all DICOM attributes in tabular format with indicating beginning & ending of sequence items. Add/delete DICOM attributes. Add/delete DICOM sequence attributes and sequence items. Mod ...
Streams and File I/O
... Creating a Binary File Writing Primitive Values to a Binary File Writing Strings to a Binary File The Class EOFException ...
... Creating a Binary File Writing Primitive Values to a Binary File Writing Strings to a Binary File The Class EOFException ...
Experience of Building and Deployment Debian on Elbrus Architecture
... source packages, maintained by Debian developers (for example dpkg) may not comprise *.diff.gz file because they already have a Debian information inside. Binary packages can contain binary and configuration files, scripts, man pages, documentation and another files to install on the system. In addi ...
... source packages, maintained by Debian developers (for example dpkg) may not comprise *.diff.gz file because they already have a Debian information inside. Binary packages can contain binary and configuration files, scripts, man pages, documentation and another files to install on the system. In addi ...
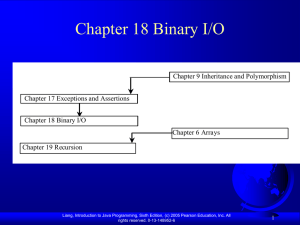
Chapter 18 Binary I/O
... BufferedInputStream/BufferedOutputStream does not contain new methods. All the methods BufferedInputStream/BufferedOutputStream are inherited from the InputStream/OutputStream classes. Liang, Introduction to Java Programming, Sixth Edition, (c) 2005 Pearson Education, Inc. All rights reserved. 0-13- ...
... BufferedInputStream/BufferedOutputStream does not contain new methods. All the methods BufferedInputStream/BufferedOutputStream are inherited from the InputStream/OutputStream classes. Liang, Introduction to Java Programming, Sixth Edition, (c) 2005 Pearson Education, Inc. All rights reserved. 0-13- ...
FILE SYSTEM STRUCTURE Disk provide the bulk of secondary
... 1. They can be rewritten in place, it is possible to read a block from the disk, to modify the block and to write it back into the same place. 2. They can access directly any given block of information to the disk. To produce an efficient and convenient access to the disk, the operating system impos ...
... 1. They can be rewritten in place, it is possible to read a block from the disk, to modify the block and to write it back into the same place. 2. They can access directly any given block of information to the disk. To produce an efficient and convenient access to the disk, the operating system impos ...
17slide
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
Chapter 17
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
... An array is serializable if all its elements are serializable. So an entire array can be saved using writeObject into a file and later restored using readObject. Here is an example that stores an array of five int values and an array of three strings, and reads them back to display on the console. ...
AdvancedUNIXDec16
... are specifically in a unix/linux shell. Most of the commands that you would use when doing basic unix/linux will be the same in any shell that you are in. However, the use shell variables and of shells for scripts and programming requires choosing a shell and adhering to its commands and way of form ...
... are specifically in a unix/linux shell. Most of the commands that you would use when doing basic unix/linux will be the same in any shell that you are in. However, the use shell variables and of shells for scripts and programming requires choosing a shell and adhering to its commands and way of form ...
douglas_daniel_rw01
... Our revised solution first makes a list of all text files in the database. This list is filtered for the desired date range and the resulting text files are searched for our string pattern. This pipeline is more efficient than our original solution. The result is 3/200,000 matched files. Problem 2: ...
... Our revised solution first makes a list of all text files in the database. This list is filtered for the desired date range and the resulting text files are searched for our string pattern. This pipeline is more efficient than our original solution. The result is 3/200,000 matched files. Problem 2: ...
Text files
... All data and programs are ultimately just zeros and ones » each digit can have one of two values, hence binary » bit is one binary digit » byte is a group of eight bits Text files: the bits represent printable characters » one byte per character for ASCII, the most common code » for example, Java so ...
... All data and programs are ultimately just zeros and ones » each digit can have one of two values, hence binary » bit is one binary digit » byte is a group of eight bits Text files: the bits represent printable characters » one byte per character for ASCII, the most common code » for example, Java so ...
Lecture 14 - The University of Texas at Dallas
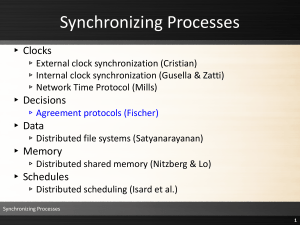
... on the servers to store the data in question until a user can resolve the problem later ▸These temporary repositories are called covolumes ▸Mitigate is the operation that transfers a file or directory from a workstation to a covolume Synchronizing Processes > Distributed File Systems > Coda > Discon ...
... on the servers to store the data in question until a user can resolve the problem later ▸These temporary repositories are called covolumes ▸Mitigate is the operation that transfers a file or directory from a workstation to a covolume Synchronizing Processes > Distributed File Systems > Coda > Discon ...
Chapter 9
... All data and programs are ultimately just zeros and ones » each digit can have one of two values, hence binary » bit is one binary digit » byte is a group of eight bits Text files: the bits represent printable characters » one byte per character for ASCII, the most common code » for example, Java so ...
... All data and programs are ultimately just zeros and ones » each digit can have one of two values, hence binary » bit is one binary digit » byte is a group of eight bits Text files: the bits represent printable characters » one byte per character for ASCII, the most common code » for example, Java so ...
- CSE@IIT Delhi
... • There are methods of storing more complex data (even objects like lists or dictionaries) in files • Can even store simple database of values in a single file ...
... • There are methods of storing more complex data (even objects like lists or dictionaries) in files • Can even store simple database of values in a single file ...
Lesson Plans - CRSD Moodle
... Americanism Essay sponsored by the local Fleet Reserve Association Students must compose a 300-35o word informative essay which explores the topic of "What Memorial Day Means." The essay is a class requirement for the students' writing portfolios and as a cross-curricular grade for both my and Mr. W ...
... Americanism Essay sponsored by the local Fleet Reserve Association Students must compose a 300-35o word informative essay which explores the topic of "What Memorial Day Means." The essay is a class requirement for the students' writing portfolios and as a cross-curricular grade for both my and Mr. W ...
Savitch Java Ch. 9 - University of Scranton: Computing Sciences Dept.
... There are three common ways to test for the end of a file: 1. Put a sentinel value at the end of the file and test for it. 2. Throw and catch an end-of-file exception. 3. Test for a special character that signals the end of the file (text files often have such a character). ...
... There are three common ways to test for the end of a file: 1. Put a sentinel value at the end of the file and test for it. 2. Throw and catch an end-of-file exception. 3. Test for a special character that signals the end of the file (text files often have such a character). ...
Chapter 9 Streams and File I/O
... • The \\ would be used if the path name is hardcoded, but the \ would be used if the path name is entered from the keyboard. • A Java program will accept a path name written in either Windows or UNIX format, even if a computer is using an operating system that does not match the syntax. ...(“D:/home ...
... • The \\ would be used if the path name is hardcoded, but the \ would be used if the path name is entered from the keyboard. • A Java program will accept a path name written in either Windows or UNIX format, even if a computer is using an operating system that does not match the syntax. ...(“D:/home ...
Notes - CSE Labs User Home Pages
... No updates are made in place – data written to new data blocks ...
... No updates are made in place – data written to new data blocks ...
9781285081953_PPT_ch13 - Business and Computer Science
... Creating Multiple Random Access Files Writing a Method to Create an Empty File Adding Data Entry Capability to the Program Setting Up a Program to Read the Created Files Displaying File Statistics Reading a File Sequentially Reading a File Randomly ...
... Creating Multiple Random Access Files Writing a Method to Create an Empty File Adding Data Entry Capability to the Program Setting Up a Program to Read the Created Files Displaying File Statistics Reading a File Sequentially Reading a File Randomly ...
UNIX---Operating System
... device is associated with a special file. – Named file system: named pipes. A pipe is a circular buffer allowing two processes to communicate on the producer-consumer model. ...
... device is associated with a special file. – Named file system: named pipes. A pipe is a circular buffer allowing two processes to communicate on the producer-consumer model. ...
Dia 1
... retracing without correction, e.g..: then [/] then retracing, with correction, e.g.: then [//] but quotation mark, used when the child literally repeats something ...
... retracing without correction, e.g..: then [/] then retracing, with correction, e.g.: then [//] but quotation mark, used when the child literally repeats something ...
Unix – Small Beginnings
... One reason Multics was so bulky was that too much functionality was put into the “kernel”, the core of the operating system. Thompson made the Unix kernel small by making it do as little as possible; much of Unix's functionality occurs through hundreds of small, independent, single-purpose utility p ...
... One reason Multics was so bulky was that too much functionality was put into the “kernel”, the core of the operating system. Thompson made the Unix kernel small by making it do as little as possible; much of Unix's functionality occurs through hundreds of small, independent, single-purpose utility p ...