Understanding and Installing Firewalls
... Laboratories, and Marcus Ranum described a third generation firewall known as an application layer firewall. Marcus Ranum's work on the technology spearheaded the creation of the first commercial product. The product was released by DEC who named it the DEC SEAL product. DEC’s first major sale was o ...
... Laboratories, and Marcus Ranum described a third generation firewall known as an application layer firewall. Marcus Ranum's work on the technology spearheaded the creation of the first commercial product. The product was released by DEC who named it the DEC SEAL product. DEC’s first major sale was o ...
Differentiate PC, server, and handheld device operating system
... Windows CE, Pocket PC OS, and Palm OS. →Windows CE is a scaled-down Windows operating system designed for use on wireless communications devices and smaller computers such as handheld computers, in-vehicle devices, and Web-enabled devices. →Pocket PC OS is a scaled-down operating system developed by ...
... Windows CE, Pocket PC OS, and Palm OS. →Windows CE is a scaled-down Windows operating system designed for use on wireless communications devices and smaller computers such as handheld computers, in-vehicle devices, and Web-enabled devices. →Pocket PC OS is a scaled-down operating system developed by ...
Junior Enlisted - Cyber Security
... Assisted Marine Corps Network Operations and Security Center to prepare for Command Cyber Readiness Inspection (CCRI) resulting in the identification / mitigation of vulnerabilities Trained 150 System Administrators and Users in their roles and responsibilities to ensure network security to prevent ...
... Assisted Marine Corps Network Operations and Security Center to prepare for Command Cyber Readiness Inspection (CCRI) resulting in the identification / mitigation of vulnerabilities Trained 150 System Administrators and Users in their roles and responsibilities to ensure network security to prevent ...
Intrusion Prevention System (IPS)
... 1. Log onto the infected system and download 'Stinger' from the McAfee site: http://vil.nai.com/vil/stinger/ Set the product to scan all the local drives, following the instructions on the site. ...
... 1. Log onto the infected system and download 'Stinger' from the McAfee site: http://vil.nai.com/vil/stinger/ Set the product to scan all the local drives, following the instructions on the site. ...
TrendMicro Titanium - A New Concept in Security by Ira Wilsker
... smallest memory footprint (least resources used), fastest file copy, and took up the smallest amount of hard drive space. While the default settings are entirely adequate to provide reasonable security, the user can control the virus and spyware settings, degree of protection from web threats, set ...
... smallest memory footprint (least resources used), fastest file copy, and took up the smallest amount of hard drive space. While the default settings are entirely adequate to provide reasonable security, the user can control the virus and spyware settings, degree of protection from web threats, set ...
Powerpoint with iClicker Questions
... Describe methods of protecting against malware attacks Describe the types of network attacks Identify physical security attacks and vulnerabilities ...
... Describe methods of protecting against malware attacks Describe the types of network attacks Identify physical security attacks and vulnerabilities ...
Remote Domain Security Awareness Training
... C-Brain: January 1986 Damaged millions of personal computers. Virus enters the machine memory once the PC is booted with the infected floppy. It infect other floppy disk accessed while it is in memory It slow down disk access and cause timeouts, make disks unusable and create data loss ...
... C-Brain: January 1986 Damaged millions of personal computers. Virus enters the machine memory once the PC is booted with the infected floppy. It infect other floppy disk accessed while it is in memory It slow down disk access and cause timeouts, make disks unusable and create data loss ...
Microsoft Word File
... month, complete with full customer service and account management features. ...
... month, complete with full customer service and account management features. ...
Here are the PowerPoint slides with links - Auto
... evidence that China’s intelligence agencies are involved, as attacks spread from hits on large technology companies to the hacking of startups and even law firms. “The government can basically put their hands in and take whatever they want,” says Michael Wessel, who sits on the U.S.-China Economic a ...
... evidence that China’s intelligence agencies are involved, as attacks spread from hits on large technology companies to the hacking of startups and even law firms. “The government can basically put their hands in and take whatever they want,” says Michael Wessel, who sits on the U.S.-China Economic a ...
Computer Systems Security
... Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
... Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
Computer Security Presentation
... offices. Drivers and applicants endured sometimes long waits at the newly overhauled New Jersey Motor Vehicle Commission's (MVC) offices on three days last week after a hard charging computer virus struck its statewide system. A survey conducted by Internet service provider America Online Inc. found ...
... offices. Drivers and applicants endured sometimes long waits at the newly overhauled New Jersey Motor Vehicle Commission's (MVC) offices on three days last week after a hard charging computer virus struck its statewide system. A survey conducted by Internet service provider America Online Inc. found ...
Windows vs.. Linux Security - Montclair State University
... The Windows operating system is designed to support applications by moving more functionality into the operating system, and by more deeply integrating applications into the Windows kernel. ...
... The Windows operating system is designed to support applications by moving more functionality into the operating system, and by more deeply integrating applications into the Windows kernel. ...
PROFESSIONAL JOB DESCRIPTION Network Support Engineer
... PROFESSIONAL JOB DESCRIPTION Exempt; Full‐time POSITION TITLE: ...
... PROFESSIONAL JOB DESCRIPTION Exempt; Full‐time POSITION TITLE: ...
Module F - Columbus State University
... to be privileged to know about, or at least take seriously. Computers around the world are systematically being victimized by rampant hacking. This hacking is not only widespread, but is being executed so flawlessly that the attackers compromise a system, steal everything of value and completely era ...
... to be privileged to know about, or at least take seriously. Computers around the world are systematically being victimized by rampant hacking. This hacking is not only widespread, but is being executed so flawlessly that the attackers compromise a system, steal everything of value and completely era ...
Current Issues in Maintaining a Secure System
... Change in Language • MALicious softWARE • Software designed to destroy, aggravate, wreak havoc, hide incriminating information, disrupt, or damage computer systems • Includes all different types of viruses, spyware, and adware ...
... Change in Language • MALicious softWARE • Software designed to destroy, aggravate, wreak havoc, hide incriminating information, disrupt, or damage computer systems • Includes all different types of viruses, spyware, and adware ...
Do you know someone may be watching you?
... Internet malware detection, defense, and analysis Intrusion detection and anomaly detections Network security Web and social networking security ...
... Internet malware detection, defense, and analysis Intrusion detection and anomaly detections Network security Web and social networking security ...
Vulnerability analysis consists of several steps: Defining and
... NMAP - Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services ...
... NMAP - Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services ...
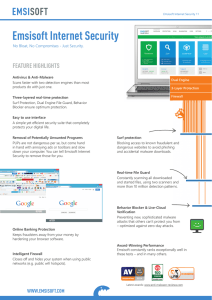
Emsisoft Internet Security
... Intelligent Firewall Closes off and hides your system when using public networks (e.g. public wifi hotspots). ...
... Intelligent Firewall Closes off and hides your system when using public networks (e.g. public wifi hotspots). ...
Tobias Herber (530) 723-6691
... - Performed routine hardware and software upgrades to local machines - Created customized Windows 7 images and scripts for workstation deployment - Administered Windows 2003-2012, CentOS, and vSphere ESXi servers - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastruct ...
... - Performed routine hardware and software upgrades to local machines - Created customized Windows 7 images and scripts for workstation deployment - Administered Windows 2003-2012, CentOS, and vSphere ESXi servers - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastruct ...
Looking into Windows
... security is a very significant concern. Lack of independent software vendor support Many software vendors no longer support their products that run on Windows XP as they are unable to receive Windows XP updates. For example, the new Microsoft Office package takes advantage of the newest Windows and ...
... security is a very significant concern. Lack of independent software vendor support Many software vendors no longer support their products that run on Windows XP as they are unable to receive Windows XP updates. For example, the new Microsoft Office package takes advantage of the newest Windows and ...