Elements of Modern Algebra
... that could be used to solve problems of the same type, and treatments were generalized to deal with whole classes of problems rather than individual ones. In our study of abstract algebra, we shall make use of our knowledge of the various number systems. At the same time, in many cases we wish to ex ...
... that could be used to solve problems of the same type, and treatments were generalized to deal with whole classes of problems rather than individual ones. In our study of abstract algebra, we shall make use of our knowledge of the various number systems. At the same time, in many cases we wish to ex ...
Notes on Galois Theory
... Definition 1.1. Let E be a field. An automorphism of E is a (ring) isomorphism from E to itself. The set of all automorphisms of E forms a group under function composition, which we denote by Aut E. Let E be a finite extension of a field F . Define the Galois group Gal(E/F ) to be the subset of Aut ...
... Definition 1.1. Let E be a field. An automorphism of E is a (ring) isomorphism from E to itself. The set of all automorphisms of E forms a group under function composition, which we denote by Aut E. Let E be a finite extension of a field F . Define the Galois group Gal(E/F ) to be the subset of Aut ...
Information Protection Based on Extraction of Square Roots of
... Hence, on the decryption stage, if Bob gets (2755, 3466) and (3466, 2755), there is no way to decide which of two Gaussians is authentic. In general, for p = 6221 there are several hundreds Gaussians that have this property, which creates ambiguity. Indeed, consider a Gaussian with three-digit compo ...
... Hence, on the decryption stage, if Bob gets (2755, 3466) and (3466, 2755), there is no way to decide which of two Gaussians is authentic. In general, for p = 6221 there are several hundreds Gaussians that have this property, which creates ambiguity. Indeed, consider a Gaussian with three-digit compo ...
CParrish - Mathematics
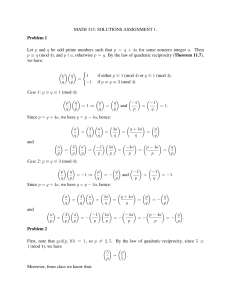
... (GCD) of a and b. We will denote a GCD of a and b by gcd(a, b). (You may be somewhat mystified by what seems to be an effort to make a simple concept appear more complex. Please be patient; you will see that this definition of a GCD will generalize readily to other mathematical entities, which in so ...
... (GCD) of a and b. We will denote a GCD of a and b by gcd(a, b). (You may be somewhat mystified by what seems to be an effort to make a simple concept appear more complex. Please be patient; you will see that this definition of a GCD will generalize readily to other mathematical entities, which in so ...
Results on Some Generalizations of Interval Graphs
... v ∈ V (G), v is not in one of N [X], N [Y ], or N [Z]. Thus N [X] ∩ N [Y ] ∩ N [Z] = ∅. ⇐ Suppose G is an n − star graph with middle clique C. Let (P, <) be the middle clique partial order for middle clique C. Suppose (P, <) has a covering with three chains with top elements X, Y, Z such that N [X] ...
... v ∈ V (G), v is not in one of N [X], N [Y ], or N [Z]. Thus N [X] ∩ N [Y ] ∩ N [Z] = ∅. ⇐ Suppose G is an n − star graph with middle clique C. Let (P, <) be the middle clique partial order for middle clique C. Suppose (P, <) has a covering with three chains with top elements X, Y, Z such that N [X] ...
Lecture 5 Message Authentication and Hash Functions
... • if x is composite it outputs yes with probability at most ¼. Probability is taken only over the internal randomness of the algorithm, so we can iterate! The error goes to zero exponentially fast. This algorithm is fast and practical! ...
... • if x is composite it outputs yes with probability at most ¼. Probability is taken only over the internal randomness of the algorithm, so we can iterate! The error goes to zero exponentially fast. This algorithm is fast and practical! ...
, Elementary Number Theory
... where a,b, and m are large numbers All computations will involve repeated modular multiplications (one multiplication followed by one division by the modulus m, to get the remainder) If modulus m is a n-bit number the largest possible value after a multiplication is guaranteed to be less than 2nbits ...
... where a,b, and m are large numbers All computations will involve repeated modular multiplications (one multiplication followed by one division by the modulus m, to get the remainder) If modulus m is a n-bit number the largest possible value after a multiplication is guaranteed to be less than 2nbits ...
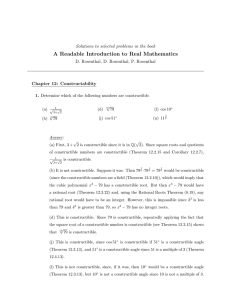
Algebraic Number Theory, a Computational Approach
... groups, and such a presentation can be reinterpreted in terms of matrices over the integers. Next we describe how to use row and column operations over the integers to show that every matrix over the integers is equivalent to one in a canonical diagonal form, called the Smith normal form. We obtain ...
... groups, and such a presentation can be reinterpreted in terms of matrices over the integers. Next we describe how to use row and column operations over the integers to show that every matrix over the integers is equivalent to one in a canonical diagonal form, called the Smith normal form. We obtain ...
Revision 2 - Electronic Colloquium on Computational Complexity
... codes and PCPs of proximity). We define a concrete-efficiency threshold that indicates the smallest problem size beyond which the PCP becomes “useful”, in the sense that using it actually pays off relative to naive verification by simply rerunning the computation; our definition takes into account b ...
... codes and PCPs of proximity). We define a concrete-efficiency threshold that indicates the smallest problem size beyond which the PCP becomes “useful”, in the sense that using it actually pays off relative to naive verification by simply rerunning the computation; our definition takes into account b ...