SGSNs in Pool
... the Gs interface to the MSC to be off-loaded. The corresponding IMSI Hash table is reconfigured to reflect the redistribution. If the SGSNs are also configured in a pool, this is repeated for any SGSN connected to that MSC. The IMSI Hash table have a consistent configuration in all SGSNs in the pool ...
... the Gs interface to the MSC to be off-loaded. The corresponding IMSI Hash table is reconfigured to reflect the redistribution. If the SGSNs are also configured in a pool, this is repeated for any SGSN connected to that MSC. The IMSI Hash table have a consistent configuration in all SGSNs in the pool ...
Institutionen f r systemteknik ö
... A Tactical Data Link (TDL) system has been deployed in many military missions as a winning strategy. The performance of a TDL system is governed by the MAC protocol. The MAC protocol that is able to provide more flexibility and high quality of services is more desirable. However, most MAC protocols ...
... A Tactical Data Link (TDL) system has been deployed in many military missions as a winning strategy. The performance of a TDL system is governed by the MAC protocol. The MAC protocol that is able to provide more flexibility and high quality of services is more desirable. However, most MAC protocols ...
FIRETIDE RFP RESPONSE TEMPLATE
... HotPort 7000 indoor and outdoor mesh nodes provide dual radios dedicated for backhaul, direct Ethernet connections for video cameras and other devices, and operate with Firetide or 3rd party APs. Indoor nodes include a built-in four port 10/100 / 1000 Ethernet switch. HotPort 7000 outdoor mesh nodes ...
... HotPort 7000 indoor and outdoor mesh nodes provide dual radios dedicated for backhaul, direct Ethernet connections for video cameras and other devices, and operate with Firetide or 3rd party APs. Indoor nodes include a built-in four port 10/100 / 1000 Ethernet switch. HotPort 7000 outdoor mesh nodes ...
Document
... problems will experience even a 10-fold speedup The implicit assumption that p is independent of N is virtually never the case In reality , the problem size scales with N, i.e. given a more powerful processor users gain control over grid resolution, number of timesteps, etc., allowing the progra ...
... problems will experience even a 10-fold speedup The implicit assumption that p is independent of N is virtually never the case In reality , the problem size scales with N, i.e. given a more powerful processor users gain control over grid resolution, number of timesteps, etc., allowing the progra ...
Planning Guide version 6.0
... Nova-network is a simple legacy network manager. It can operate with predefined Private IP spaces only. • If you do not want to split your VMs into isolated groups (tenants), you can choose the Nova-network with FlatDHCP topology. In this case, you will have one big network for all tenants and their ...
... Nova-network is a simple legacy network manager. It can operate with predefined Private IP spaces only. • If you do not want to split your VMs into isolated groups (tenants), you can choose the Nova-network with FlatDHCP topology. In this case, you will have one big network for all tenants and their ...
Experiment Manual
... parameter and determine the number of packets sent by TCP / UDP. (n0, n1 and n3 are nodes and n2 is router.). .......................................................................................................................28 Experiment 4: Simulate the different types of internet traffic such ...
... parameter and determine the number of packets sent by TCP / UDP. (n0, n1 and n3 are nodes and n2 is router.). .......................................................................................................................28 Experiment 4: Simulate the different types of internet traffic such ...
Document
... need to input the next-hop addresses along the path to the destination. Advantages: This idea solves certain network administrative problems involved with RSVP in networks where RSVP is used. Today due to RSVP not being enabled on an egress interface at certain nodes or insufficient RSVP bandwidth o ...
... need to input the next-hop addresses along the path to the destination. Advantages: This idea solves certain network administrative problems involved with RSVP in networks where RSVP is used. Today due to RSVP not being enabled on an egress interface at certain nodes or insufficient RSVP bandwidth o ...
ecs251 Spring 2007: Operating System Models #1: File Systems
... Load balance: distributed hash function, spreading keys evenly over peers Decentralization: chord is fully distributed, no node more important than other, improves robustness Scalability: logarithmic growth of lookup costs with number of peers in network, even very large systems are feasible Availab ...
... Load balance: distributed hash function, spreading keys evenly over peers Decentralization: chord is fully distributed, no node more important than other, improves robustness Scalability: logarithmic growth of lookup costs with number of peers in network, even very large systems are feasible Availab ...
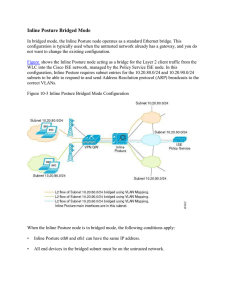
15360608-Inline Posture Bridged Mode
... Consider the following when configuring filters: • As typically implemented, Inline Posture enforces authentication requirements on endpoints that attempt to access the network. Device and subnet filters are used to validate or deny WLC and VPN devices. • For certain devices, you may want to bypass ...
... Consider the following when configuring filters: • As typically implemented, Inline Posture enforces authentication requirements on endpoints that attempt to access the network. Device and subnet filters are used to validate or deny WLC and VPN devices. • For certain devices, you may want to bypass ...
A Robust Push-to-Talk Service for Wireless Mesh Networks
... To participate in the mesh PTT session, the user specifies in his VoIP application the IP address of our virtual SIP server (i.e., “sip:[email protected]”). This IP is the same throughout the mesh. Every mesh node intercepts packets sent to this address and follows the SIP protocol to connect the cli ...
... To participate in the mesh PTT session, the user specifies in his VoIP application the IP address of our virtual SIP server (i.e., “sip:[email protected]”). This IP is the same throughout the mesh. Every mesh node intercepts packets sent to this address and follows the SIP protocol to connect the cli ...
Slide presentation with simulation results - OSPF
... there exists a bidirectional neighbor that does not satisfy condition (a) or (b). If a Backup MDR or non-flooding MDR receives a new LSA, it waits ½ sec plus jitter, then floods the LSA back out the receiving interface if there exists a bidirectional neighbor that does not satisfy condition (a) or ( ...
... there exists a bidirectional neighbor that does not satisfy condition (a) or (b). If a Backup MDR or non-flooding MDR receives a new LSA, it waits ½ sec plus jitter, then floods the LSA back out the receiving interface if there exists a bidirectional neighbor that does not satisfy condition (a) or ( ...