Combining Events And Threads For Scalable
... handlers and represented as some form of state machine with explicit message passing or in continuation-passing style (CPS). Both representations are difficult to program with and reason about, as indicated by the name of Python’s popular, event-driven networking framework, “Twisted” [24]. Performan ...
... handlers and represented as some form of state machine with explicit message passing or in continuation-passing style (CPS). Both representations are difficult to program with and reason about, as indicated by the name of Python’s popular, event-driven networking framework, “Twisted” [24]. Performan ...
unit-1-The-UNIX-Operating-System
... that allow users and application programs to access system resources (e.g. the CPU, memory, disks, modems, printers, network cards etc.) in a safe, efficient and abstract way. For example, an OS ensures safe access to a printer by allowing only one application program to send data directly to the pr ...
... that allow users and application programs to access system resources (e.g. the CPU, memory, disks, modems, printers, network cards etc.) in a safe, efficient and abstract way. For example, an OS ensures safe access to a printer by allowing only one application program to send data directly to the pr ...
Chapter 22 - Windows XP
... Executive — Local Procedure Call Facility The LPC passes requests and results between client and server ...
... Executive — Local Procedure Call Facility The LPC passes requests and results between client and server ...
UI Resources
... • They are XML files located in the res\layout folder. • A layout file may be associated with one or more Activities. • YOU may recall the setContentView(R.layout.activity_main) method that associates an Activity with a layout file(activity_main.xml). ...
... • They are XML files located in the res\layout folder. • A layout file may be associated with one or more Activities. • YOU may recall the setContentView(R.layout.activity_main) method that associates an Activity with a layout file(activity_main.xml). ...
Threads
... API specifies behavior of the thread library, implementation is up to development of the library. Common in UNIX operating systems. ...
... API specifies behavior of the thread library, implementation is up to development of the library. Common in UNIX operating systems. ...
AIM COLLEGE-HISAR What is an Operating System?
... One way that operating-system designers reduce the chance of thrashing is by reducing the need for new processes to perform various tasks. Some operating systems allow for a "process-lite," called a thread, that can deal with all the CPU-intensive work of a normal process, but generally does not dea ...
... One way that operating-system designers reduce the chance of thrashing is by reducing the need for new processes to perform various tasks. Some operating systems allow for a "process-lite," called a thread, that can deal with all the CPU-intensive work of a normal process, but generally does not dea ...
Chapter 21 - Linux Operating System
... The environment vector is a list of “NAME=VALUE” pairs that associates named environment variables with arbitrary textual values ...
... The environment vector is a list of “NAME=VALUE” pairs that associates named environment variables with arbitrary textual values ...
Multithreaded Programming
... To examine issues related to multithreaded programming To cover operating system support for threads in Windows and Linux ...
... To examine issues related to multithreaded programming To cover operating system support for threads in Windows and Linux ...
Presentation
... • For users, one of the most important features of a file system is the ability to store information according to a pattern of organization that is enabled by the use of directories • In the early Windows systems and UNIX systems, files are organized by directories, while in later Windows versions a ...
... • For users, one of the most important features of a file system is the ability to store information according to a pattern of organization that is enabled by the use of directories • In the early Windows systems and UNIX systems, files are organized by directories, while in later Windows versions a ...
A Taxonomy of Computer Program Security Flaws, with Examples
... We distinguish the nature of a flaw from the nature of its exploitation, and we focus on the former. For example, although the covert channel used in the TENEX password compromise scheme (case DT in the Appendix) could be exploited maliciously, it was introduced innocently. Consequently, we place th ...
... We distinguish the nature of a flaw from the nature of its exploitation, and we focus on the former. For example, although the covert channel used in the TENEX password compromise scheme (case DT in the Appendix) could be exploited maliciously, it was introduced innocently. Consequently, we place th ...
Operating Systems (Notes to prepare in 1 night before Exam)
... Communication • Create, delete communication connections • Send, receive messages • Transfer status information • Attach or detach remote devices ...
... Communication • Create, delete communication connections • Send, receive messages • Transfer status information • Attach or detach remote devices ...
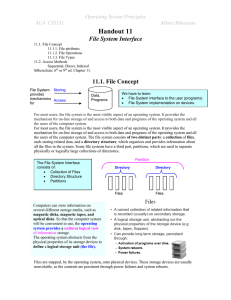
H 10.1. File-System Interface
... Most of the file operations mentioned involve searching the directory for the entry associated with the named file. To avoid this constant searching, many systems require that an open system call be used before that file is first used actively. The operating system keeps a small table containing inf ...
... Most of the file operations mentioned involve searching the directory for the entry associated with the named file. To avoid this constant searching, many systems require that an open system call be used before that file is first used actively. The operating system keeps a small table containing inf ...
Notes
... System Calls • System calls provide the interface between a running program and the operating system. – For example – open input file, create output file, print message to console, terminate with error or normally – Generally available as routines written in C and C++ – Certain low-level tasks (dir ...
... System Calls • System calls provide the interface between a running program and the operating system. – For example – open input file, create output file, print message to console, terminate with error or normally – Generally available as routines written in C and C++ – Certain low-level tasks (dir ...
Concurrency: Threads, Address Spaces, and Processes
... and tossed with a pair of dedicated hands. There are a number of benefits for an operating system to provide concurrency: 1. Of course, the most obvious benefit is to be able to run multiple applications at the same time. 2. Since resources that are unused by one application can be used for other ap ...
... and tossed with a pair of dedicated hands. There are a number of benefits for an operating system to provide concurrency: 1. Of course, the most obvious benefit is to be able to run multiple applications at the same time. 2. Since resources that are unused by one application can be used for other ap ...
The Life of A Thread
... • Prevent collisions in which more than one thread attempts to modify the same object at the same time. • Java Object class provides each object a lock. The lock can be manipulated only by JVM (Java Virtual Machine) and allow only one thread at a time to access the object. ...
... • Prevent collisions in which more than one thread attempts to modify the same object at the same time. • Java Object class provides each object a lock. The lock can be manipulated only by JVM (Java Virtual Machine) and allow only one thread at a time to access the object. ...
CSE244 Compiler (a.k.a. Programming Language Translation)
... • Two-pass Assembly: – First Pass: all identifiers are assigned to memory addresses (0offset) – e.g. substitute 0 for a, and 4 for b – Second Pass: produce relocatable machine code: ...
... • Two-pass Assembly: – First Pass: all identifiers are assigned to memory addresses (0offset) – e.g. substitute 0 for a, and 4 for b – Second Pass: produce relocatable machine code: ...
pptx
... – serial – blocks removed in FIFO order, queue is per process, called main queue • Programmers can create additional serial queues within program ...
... – serial – blocks removed in FIFO order, queue is per process, called main queue • Programmers can create additional serial queues within program ...
ch2
... Mostly accessed by programs via a high-level Application Program Interface (API) rather than direct system call use Three most common APIs are Win32 API for Windows, POSIX API for POSIX-based systems (including virtually all versions of UNIX, Linux, and Mac OS X), and Java API for the Java virtual m ...
... Mostly accessed by programs via a high-level Application Program Interface (API) rather than direct system call use Three most common APIs are Win32 API for Windows, POSIX API for POSIX-based systems (including virtually all versions of UNIX, Linux, and Mac OS X), and Java API for the Java virtual m ...
Windows
... – ProductType: WinNT=Workstation, ServerNT=Server not a domain controller, LanManNT=Server that is a Domain Controller – ProductSuite: indicates type of Server (Advanced, Datacenter, or ...
... – ProductType: WinNT=Workstation, ServerNT=Server not a domain controller, LanManNT=Server that is a Domain Controller – ProductSuite: indicates type of Server (Advanced, Datacenter, or ...
File System - UC Davis Computer Science
... Authenticate that process can access the file Create an internal file descriptor in primary memory Create an entry in a “per process” open file status table Allocate resources, e.g., buffers, to support file usage ...
... Authenticate that process can access the file Create an internal file descriptor in primary memory Create an entry in a “per process” open file status table Allocate resources, e.g., buffers, to support file usage ...
Library (computing)
In computer science, a library is a collection of non-volatile resources used by computer programs, often to develop software. These may include configuration data, documentation, help data, message templates, pre-written code and subroutines, classes, values or type specifications. In IBM's OS/360 and its successors they are referred to as partitioned data sets.In computer science, a library is a collection of implementations of behavior, written in terms of a language, that has a well-defined interface by which the behavior is invoked. This means that as long as a higher level program uses a library to make system calls, it does not need to be re-written to implement those system calls over and over again. In addition, the behavior is provided for reuse by multiple independent programs. A program invokes the library-provided behavior via a mechanism of the language. For example, in a simple imperative language such as C, the behavior in a library is invoked by using C's normal function-call. What distinguishes the call as being to a library, versus being to another function in the same program, is the way that the code is organized in the system. Library code is organized in such a way that it can be used by multiple programs that have no connection to each other, while code that is part of a program is organized to only be used within that one program. This distinction can gain a hierarchical notion when a program grows large, such as a multi-million-line program. In that case, there may be internal libraries that are reused by independent sub-portions of the large program. The distinguishing feature is that a library is organized for the purposes of being reused by independent programs or sub-programs, and the user only needs to know the interface, and not the internal details of the library.The value of a library is the reuse of the behavior. When a program invokes a library, it gains the behavior implemented inside that library without having to implement that behavior itself. Libraries encourage the sharing of code in a modular fashion, and ease the distribution of the code. The behavior implemented by a library can be connected to the invoking program at different program lifecycle phases. If the code of the library is accessed during the build of the invoking program, then the library is called a static library. An alternative is to build the executable of the invoking program and distribute that, independently from the library implementation. The library behavior is connected after the executable has been invoked to be executed, either as part of the process of starting the execution, or in the middle of execution. In this case the library is called a dynamic library. A dynamic library can be loaded and linked as part of preparing a program for execution, by the linker. Alternatively, in the middle of execution, an application may explicitly request that a module be loaded.Most compiled languages have a standard library although programmers can also create their own custom libraries. Most modern software systems provide libraries that implement the majority of system services. Such libraries have commoditized the services which a modern application requires. As such, most code used by modern applications is provided in these system libraries.