2.01
... among processes, users, and computer systems Allow users to send messages to one another’s screens, browse web pages, send electronic-mail messages, log in remotely, transfer files from one machine to another ...
... among processes, users, and computer systems Allow users to send messages to one another’s screens, browse web pages, send electronic-mail messages, log in remotely, transfer files from one machine to another ...
Lecture10c,Boot,process
... Using Safe Mode to Start the Computer: Safe mode is a method of starting Windows XP Professional by using only default settings, which include a VGA video driver, a Microsoft mouse driver, and the minimum device drivers necessary to start the computer. When your computer will not start normally, yo ...
... Using Safe Mode to Start the Computer: Safe mode is a method of starting Windows XP Professional by using only default settings, which include a VGA video driver, a Microsoft mouse driver, and the minimum device drivers necessary to start the computer. When your computer will not start normally, yo ...
Compilation I: Java Byte Code
... A just-in-time compiler (a JIT) compiles Java byte code to the native machine code of the machine which we are using (for example, an Intel Pentium processor or a SUN Sparc chip). This compilation is performed at the time when the request is made to execute the program (hence the name “just in time” ...
... A just-in-time compiler (a JIT) compiles Java byte code to the native machine code of the machine which we are using (for example, an Intel Pentium processor or a SUN Sparc chip). This compilation is performed at the time when the request is made to execute the program (hence the name “just in time” ...
Formatting and Partitioning Hard Drives, and DOS
... 7. Once data has been deleted, it is impossible to retrieve it under any circumstances ...
... 7. Once data has been deleted, it is impossible to retrieve it under any circumstances ...
1. design principle
... pages in the computer’s memory. I/O Manager manages all input and output for the operating system, including cache manager, file system drivers, hardware device drivers, and network device drivers. Win32K window manager and GDI - Functions from Win32k.sys for graphics support and communication w ...
... pages in the computer’s memory. I/O Manager manages all input and output for the operating system, including cache manager, file system drivers, hardware device drivers, and network device drivers. Win32K window manager and GDI - Functions from Win32k.sys for graphics support and communication w ...
Lecture #6
... that forms the basis of multithreaded computer systems To discuss the APIs for the Pthreads, Win32, and Java thread libraries To examine issues related to multithreaded programming ...
... that forms the basis of multithreaded computer systems To discuss the APIs for the Pthreads, Win32, and Java thread libraries To examine issues related to multithreaded programming ...
Introduction to Operating Systems
... • Multiplexing of physical memory and disk blocks to create illusion of separate memory per process ...
... • Multiplexing of physical memory and disk blocks to create illusion of separate memory per process ...
Computer System Arch..
... • Dynamic Loading - Routine is not loaded until it is called. • Dynamic Linking - Linking postponed until execution time • Overlays - Keep in memory only those instructions and data that are needed at any given time • Swapping - A process can be swapped temporarily out of memory to a backing store a ...
... • Dynamic Loading - Routine is not loaded until it is called. • Dynamic Linking - Linking postponed until execution time • Overlays - Keep in memory only those instructions and data that are needed at any given time • Swapping - A process can be swapped temporarily out of memory to a backing store a ...
Ceng 334 - Operating Systems
... but if hardware supports they can be separate): Text : executable code (which is shared in the figure) Data : variables, strings, arrays etc. ...
... but if hardware supports they can be separate): Text : executable code (which is shared in the figure) Data : variables, strings, arrays etc. ...
Discovering Computers Fundamentals 3rd Edition
... What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
... What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
A TOTAL SOLUTION
... Although the preceding sample programs illustrate several important features of the Java language, they are not very useful. Even though you do not know much about Java at this point, you can still put what you have learned to work to create a practical program. In this project, we will create a pro ...
... Although the preceding sample programs illustrate several important features of the Java language, they are not very useful. Even though you do not know much about Java at this point, you can still put what you have learned to work to create a practical program. In this project, we will create a pro ...
Slide set 14
... The system call code executes, control is returned to the calling program, (another context switch) and the machine switches back to user mode. ...
... The system call code executes, control is returned to the calling program, (another context switch) and the machine switches back to user mode. ...
Chapter 14
... • How to access MS-DOS emulators from other operating systems • How MS-DOS provided a foundation for early Microsoft Windows releases • The basics of command-driven systems and how to construct simple batch files • How one processor can be shared among multiple processes • The limitations of MS-DOS ...
... • How to access MS-DOS emulators from other operating systems • How MS-DOS provided a foundation for early Microsoft Windows releases • The basics of command-driven systems and how to construct simple batch files • How one processor can be shared among multiple processes • The limitations of MS-DOS ...
ppt
... • Unbounded-buffer places no practical limit on the size of the buffer. Consumer may wait, producer never waits. • Bounded-buffer assumes that there is a fixed buffer size. Consumer waits for new item, producer waits if buffer is full. Producer and Consumer must synchronize. ...
... • Unbounded-buffer places no practical limit on the size of the buffer. Consumer may wait, producer never waits. • Bounded-buffer assumes that there is a fixed buffer size. Consumer waits for new item, producer waits if buffer is full. Producer and Consumer must synchronize. ...
Operating System
... What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
... What are other program management features of operating systems? multiprocessing Can support two or more processors running programs at same time ...
2.01 - Computer Science at Rutgers
... Programming interface to the services provided by the OS Typically written in a high-level language (C or C++) Mostly accessed by programs via a high-level Application ...
... Programming interface to the services provided by the OS Typically written in a high-level language (C or C++) Mostly accessed by programs via a high-level Application ...
lecture8
... which is why it should not be mistaken for Windows XP Embedded, which is NT. Windows CE was used in the Sega Dreamcast along with Sega's own proprietary OS for the console. Windows Lifecycle Policy Microsoft has stopped releasing updates and hotfixes for many old Windows operating systems, including ...
... which is why it should not be mistaken for Windows XP Embedded, which is NT. Windows CE was used in the Sega Dreamcast along with Sega's own proprietary OS for the console. Windows Lifecycle Policy Microsoft has stopped releasing updates and hotfixes for many old Windows operating systems, including ...
Lesson 8
... called file systems. The Linux partition used to install the Linux system on is called the root partition. The root partition ( indicated by a single slash, /) contains the main file system and user subdirectories. To access files on another file system, say a CD-ROM, you need to attach that file sy ...
... called file systems. The Linux partition used to install the Linux system on is called the root partition. The root partition ( indicated by a single slash, /) contains the main file system and user subdirectories. To access files on another file system, say a CD-ROM, you need to attach that file sy ...
Operating System
... They are used to request kernel to provide various services, such as reading from a file stored on hard disk. They can be invoked via library procedures, or via command provided by shell, or even directly from C programs in UNIX. System calls are similar to user-defined functions. Differenc ...
... They are used to request kernel to provide various services, such as reading from a file stored on hard disk. They can be invoked via library procedures, or via command provided by shell, or even directly from C programs in UNIX. System calls are similar to user-defined functions. Differenc ...
The Styx Architecture for Distributed Systems
... accessed by standard file I/O mechanisms but is nonetheless a transient object fabricated dynamically by a running program; it has no permanent existence. By following this approach throughout the system, Plan 9 achieves a remarkable degree of transparency in the distribution of resources[PPTTW93]. ...
... accessed by standard file I/O mechanisms but is nonetheless a transient object fabricated dynamically by a running program; it has no permanent existence. By following this approach throughout the system, Plan 9 achieves a remarkable degree of transparency in the distribution of resources[PPTTW93]. ...
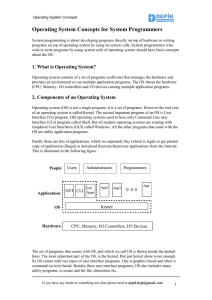
Operating System Concepts for System Programmers
... is called booting process. Following are the various steps involved while booting the OS: The BIOS program present in the non-volatile (ROM/Flash) memory of a computer will run first. In fact whenever a CPU is powered on, it tries to fetch (read) instructions from a fixed start address. The computer ...
... is called booting process. Following are the various steps involved while booting the OS: The BIOS program present in the non-volatile (ROM/Flash) memory of a computer will run first. In fact whenever a CPU is powered on, it tries to fetch (read) instructions from a fixed start address. The computer ...
Library (computing)
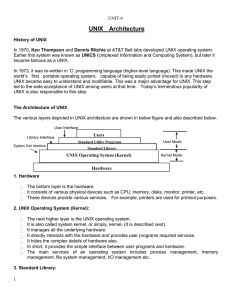
In computer science, a library is a collection of non-volatile resources used by computer programs, often to develop software. These may include configuration data, documentation, help data, message templates, pre-written code and subroutines, classes, values or type specifications. In IBM's OS/360 and its successors they are referred to as partitioned data sets.In computer science, a library is a collection of implementations of behavior, written in terms of a language, that has a well-defined interface by which the behavior is invoked. This means that as long as a higher level program uses a library to make system calls, it does not need to be re-written to implement those system calls over and over again. In addition, the behavior is provided for reuse by multiple independent programs. A program invokes the library-provided behavior via a mechanism of the language. For example, in a simple imperative language such as C, the behavior in a library is invoked by using C's normal function-call. What distinguishes the call as being to a library, versus being to another function in the same program, is the way that the code is organized in the system. Library code is organized in such a way that it can be used by multiple programs that have no connection to each other, while code that is part of a program is organized to only be used within that one program. This distinction can gain a hierarchical notion when a program grows large, such as a multi-million-line program. In that case, there may be internal libraries that are reused by independent sub-portions of the large program. The distinguishing feature is that a library is organized for the purposes of being reused by independent programs or sub-programs, and the user only needs to know the interface, and not the internal details of the library.The value of a library is the reuse of the behavior. When a program invokes a library, it gains the behavior implemented inside that library without having to implement that behavior itself. Libraries encourage the sharing of code in a modular fashion, and ease the distribution of the code. The behavior implemented by a library can be connected to the invoking program at different program lifecycle phases. If the code of the library is accessed during the build of the invoking program, then the library is called a static library. An alternative is to build the executable of the invoking program and distribute that, independently from the library implementation. The library behavior is connected after the executable has been invoked to be executed, either as part of the process of starting the execution, or in the middle of execution. In this case the library is called a dynamic library. A dynamic library can be loaded and linked as part of preparing a program for execution, by the linker. Alternatively, in the middle of execution, an application may explicitly request that a module be loaded.Most compiled languages have a standard library although programmers can also create their own custom libraries. Most modern software systems provide libraries that implement the majority of system services. Such libraries have commoditized the services which a modern application requires. As such, most code used by modern applications is provided in these system libraries.