Physical Unclonable Functions
... [3] Gassend, Blaise, et al. "Controlled physical random functions and applications." ACM Transactions on Information and System Security (TISSEC) 10.4 (2008): 3. [4] J.W. Lee, D. Lim, B. Gassend, G. E. Suh, M. van Dijk and S. Devadas, “ A technique to build a secret key in integrated circuits with i ...
... [3] Gassend, Blaise, et al. "Controlled physical random functions and applications." ACM Transactions on Information and System Security (TISSEC) 10.4 (2008): 3. [4] J.W. Lee, D. Lim, B. Gassend, G. E. Suh, M. van Dijk and S. Devadas, “ A technique to build a secret key in integrated circuits with i ...
Topic 5 - Processors
... • RD (Read) - indicates that the selected memory location or the I/O device has to be read. • WR (Write) - indicates that data is available on the data bus and the data has to be written to the memory location or the I/O device Provided by the address bus. ...
... • RD (Read) - indicates that the selected memory location or the I/O device has to be read. • WR (Write) - indicates that data is available on the data bus and the data has to be written to the memory location or the I/O device Provided by the address bus. ...
Toolchains - Compiler and OS support for embedded multiprocessors
... It must be figured out on-the-fly if a new task can be accepted and on with processor it will be executed ...
... It must be figured out on-the-fly if a new task can be accepted and on with processor it will be executed ...
Multicore Organization
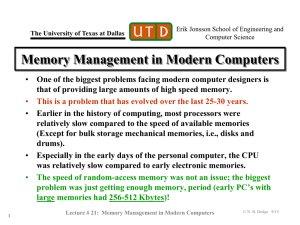
... Small amounts of serial code impact performance due to Communication, distribution of work and cache coherence overheads percentage of ...
... Small amounts of serial code impact performance due to Communication, distribution of work and cache coherence overheads percentage of ...
CPLD Basics
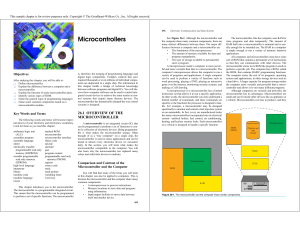
... re-compiled. The compiler translates from a higher-level language to binary values that the hardware device can understand. ...
... re-compiled. The compiler translates from a higher-level language to binary values that the hardware device can understand. ...
Chapter 21 - Web Services Overview
... sensor. These include movement detectors in individual rooms, door sensors that detect corridor doors opening, and window sensors on ground-floor windows that detect when a window has been opened. When a sensor detects the presence of an intruder, the system automatically calls the local police and, ...
... sensor. These include movement detectors in individual rooms, door sensors that detect corridor doors opening, and window sensors on ground-floor windows that detect when a window has been opened. When a sensor detects the presence of an intruder, the system automatically calls the local police and, ...
Emulator

In computing, an emulator is hardware or software that enables one computer system (called the host) to behave like another computer system (called the guest). An emulator typically enables the host system to run software or use peripheral devices designed for the guest system.