UNIX I
... puts the parameters on the stack performs a system ÔtrapÕ Ð hardware dependent ✰ ✰ now in system mode ✰ ✰ ...
... puts the parameters on the stack performs a system ÔtrapÕ Ð hardware dependent ✰ ✰ now in system mode ✰ ✰ ...
Quick UNIX Tutorial
... • The Unix process that interprets your commands is called the “shell” • When you login, the login process, after it verifies the user’s username and password, creates a shell process. • The shell process displays a prompt on the screen and waits. • When the user enters a command, the shell examines ...
... • The Unix process that interprets your commands is called the “shell” • When you login, the login process, after it verifies the user’s username and password, creates a shell process. • The shell process displays a prompt on the screen and waits. • When the user enters a command, the shell examines ...
The Operating System
... Three general methods used to pass parameters to the OS Simplest: pass the parameters in registers In some cases, may be more parameters than registers Parameters stored in a block, or table, in memory, and address of block passed as a parameter in a register This approach taken by Linux a ...
... Three general methods used to pass parameters to the OS Simplest: pass the parameters in registers In some cases, may be more parameters than registers Parameters stored in a block, or table, in memory, and address of block passed as a parameter in a register This approach taken by Linux a ...
Computer Systems - Korea University
... The use of a Linux operating system in embedded computer systems According to survey conducted by Venture Development Corporation, Linux was used by 18% of embedded engineers Embedded versions of Linux are designed for devices with relatively limited resources, such as cell phones and set-top boxes ...
... The use of a Linux operating system in embedded computer systems According to survey conducted by Venture Development Corporation, Linux was used by 18% of embedded engineers Embedded versions of Linux are designed for devices with relatively limited resources, such as cell phones and set-top boxes ...
Computer Systems - BYU Computer Science Students Homepage
... Operating systems have to deal with issues like disconnected operation and mobility. Media rich information within the grasp of common people - information with psuedo-real time components like voice and video. Operating systems will have to adjust to deliver acceptable performance for these new for ...
... Operating systems have to deal with issues like disconnected operation and mobility. Media rich information within the grasp of common people - information with psuedo-real time components like voice and video. Operating systems will have to adjust to deliver acceptable performance for these new for ...
Chapter 1 (Part 2) Introduction to Operating System
... time constraints. Processing must be done within the defined constraints, or the system will fail. Real-Time systems may be either hard or soft realtime. Hard Real-Time Systems guarantee that critical tasks be completed on time. Soft Real-Time Systems prioritize critical tasks. That is, a crit ...
... time constraints. Processing must be done within the defined constraints, or the system will fail. Real-Time systems may be either hard or soft realtime. Hard Real-Time Systems guarantee that critical tasks be completed on time. Soft Real-Time Systems prioritize critical tasks. That is, a crit ...
Operating Systems
... 1. protect applications from each other, yet 2. share physical resources between them. • Also usually want to abstract away from grungy harware, i.e. OS provides a virtual machine: – share CPU (in time) and provide each app with a virtual processor, – allocate and protect memory, and provide applica ...
... 1. protect applications from each other, yet 2. share physical resources between them. • Also usually want to abstract away from grungy harware, i.e. OS provides a virtual machine: – share CPU (in time) and provide each app with a virtual processor, – allocate and protect memory, and provide applica ...
Arrakis: A Case for the End of the Empire
... What we need is something more: the ability to give any application direct access to its own virtual disk blocks from user space. Unlike a fixed disk partition, applications could request the kernel to extend or shrink their allocation, as they are able to do for main memory today. The disk device m ...
... What we need is something more: the ability to give any application direct access to its own virtual disk blocks from user space. Unlike a fixed disk partition, applications could request the kernel to extend or shrink their allocation, as they are able to do for main memory today. The disk device m ...
Chapter 8 Operating Systems and Utility Programs Chapter 8
... contains active application - the one you currently are using Background contains inactive programs that are running but are not in use ...
... contains active application - the one you currently are using Background contains inactive programs that are running but are not in use ...
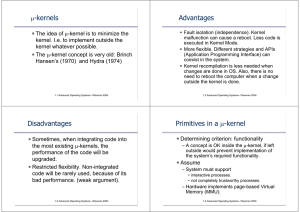
μ-kernels Advantages Disadvantages Primitives in a μ
... The µ-kernel design is extensively depending on the CPU structure. The only µ-kernel feature that can be portable is the scheduler. Large monolithic kernel can have many more portable features. In the early 70's, large portions of the kernel have been started to be written in C, so they could be por ...
... The µ-kernel design is extensively depending on the CPU structure. The only µ-kernel feature that can be portable is the scheduler. Large monolithic kernel can have many more portable features. In the early 70's, large portions of the kernel have been started to be written in C, so they could be por ...
Operating Systems - Lecture #5: File Management
... records stored one after another any record can be found and read by knowing its starting address and size ease of direct access, every part of the file is stored in the same compact area file cant be expanded unless there is empty space immediately following it - also causing fragmentation ...
... records stored one after another any record can be found and read by knowing its starting address and size ease of direct access, every part of the file is stored in the same compact area file cant be expanded unless there is empty space immediately following it - also causing fragmentation ...
Standard Operating and Maintenance Procedures
... • Operating system directories are typically placed in the root directory and have appropriate subdirectories under a main directory. – Windows 7 OS system files are contained in the Windows directory, which has subdirectories such as System, System32, and SysWOW64. – Macintosh system files are kept ...
... • Operating system directories are typically placed in the root directory and have appropriate subdirectories under a main directory. – Windows 7 OS system files are contained in the Windows directory, which has subdirectories such as System, System32, and SysWOW64. – Macintosh system files are kept ...
Operating System
... then they will compete for these resources. It is the job of the operating system to allocate these resources to the various applications so that: ...
... then they will compete for these resources. It is the job of the operating system to allocate these resources to the various applications so that: ...
EuroDesign embedded technologies GmbH
... seconds. The operating system then can already be loaded and started. Because the configuration is always the same the HyperBoot loader doesn’t have menu, like a setup in BIOS. Nevertheless for development, maintenance or repair in can be practical, to proceed on the boot process. The HyperBoot load ...
... seconds. The operating system then can already be loaded and started. Because the configuration is always the same the HyperBoot loader doesn’t have menu, like a setup in BIOS. Nevertheless for development, maintenance or repair in can be practical, to proceed on the boot process. The HyperBoot load ...
AppGuard - UTSA CS
... component in the guest kernel; 3) AppGuard directly traps the events that need to be intercepted without going through the guest kernel as in AppShield, thus not relying on any trusted components of the guest OS. This makes AppGuard backward compatiable. Secure processor based protection. A secure p ...
... component in the guest kernel; 3) AppGuard directly traps the events that need to be intercepted without going through the guest kernel as in AppShield, thus not relying on any trusted components of the guest OS. This makes AppGuard backward compatiable. Secure processor based protection. A secure p ...
Lesson 4: Process Synchronization
... nextConsumed = buffer[out]; out = (out + 1) % BUF_SZ; signal(mutex); signal(free); /* Process the item from nextConsumed */ ...
... nextConsumed = buffer[out]; out = (out + 1) % BUF_SZ; signal(mutex); signal(free); /* Process the item from nextConsumed */ ...
Porting a SAS/AF Application from PC to a MAC
... ports very smoothly. Watch out for code that does not check upperJlower case names though, since the Mac supports lowercase folder and file names. (This will apply to code ported to UNIX as well.) ...
... ports very smoothly. Watch out for code that does not check upperJlower case names though, since the Mac supports lowercase folder and file names. (This will apply to code ported to UNIX as well.) ...
Introduction to the Solaris Operating Environment
... The UNIX operating system was originally developed at AT&T Bell Laboratories in 1969. It was created as a tool set by programmers for programmers. The early source code was made available to universities all over the country. More in lecture hours Main Components of a Computer The core of all comput ...
... The UNIX operating system was originally developed at AT&T Bell Laboratories in 1969. It was created as a tool set by programmers for programmers. The early source code was made available to universities all over the country. More in lecture hours Main Components of a Computer The core of all comput ...
2005-03-midterm.pdf
... (1) A resource is assigned to at most one process at a time; (2) Processes can request a resource while holding another; (3) A resource cannot be taken away from a process; (4) Two or more processes must be waiting for release of a resource held by another. 3b What is the fundamental difference betw ...
... (1) A resource is assigned to at most one process at a time; (2) Processes can request a resource while holding another; (3) A resource cannot be taken away from a process; (4) Two or more processes must be waiting for release of a resource held by another. 3b What is the fundamental difference betw ...
03_processes
... • Use ps command to see the currently started processes in the system • Use ps aux to get more detailed information • See the manual page of the ps to get help about the ps: – Type: man ps • The man command gives info about a command, program, library function, or system call. • The /proc file syste ...
... • Use ps command to see the currently started processes in the system • Use ps aux to get more detailed information • See the manual page of the ps to get help about the ps: – Type: man ps • The man command gives info about a command, program, library function, or system call. • The /proc file syste ...
Ceng 334 - Operating Systems
... • OS services only accessed via system calls • Users and programs can’t directly access the hardware Set of System Calls (APIs) is what programs think the operating system is. Ceng 334 - Operating Systems ...
... • OS services only accessed via system calls • Users and programs can’t directly access the hardware Set of System Calls (APIs) is what programs think the operating system is. Ceng 334 - Operating Systems ...
Lecture 5: September 19 5.1 Scheduling
... The long-term, or admission, scheduler decides which jobs or processes are to be admitted to the ready queue and how many processes should be admitted into the ready queue. This controls the total number of jobs which can be running within the system. In practice, this limit is generally not reached ...
... The long-term, or admission, scheduler decides which jobs or processes are to be admitted to the ready queue and how many processes should be admitted into the ready queue. This controls the total number of jobs which can be running within the system. In practice, this limit is generally not reached ...
lec-3 - WordPress.com
... Distributed Systems: Networking and internetworking have created a new dimension in operating systems. A job that was previously done on one computer can now be shared between computers that may be thousands of miles apart. A program can be run partially on one computer and partially on another if t ...
... Distributed Systems: Networking and internetworking have created a new dimension in operating systems. A job that was previously done on one computer can now be shared between computers that may be thousands of miles apart. A program can be run partially on one computer and partially on another if t ...