slides
... group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file ...
... group identifier (group ID) allows set of users to be defined and controls managed, then also associated with each process, file ...
OPERATING SYSTEMS
... file; and semi-private files allows some users with the correct password access to files. User also specifies if others can or cannot modify, erase these accessible files. Hence the OS keeps “directories of information about the location and characteristics of files stored on a computer’s secondary ...
... file; and semi-private files allows some users with the correct password access to files. User also specifies if others can or cannot modify, erase these accessible files. Hence the OS keeps “directories of information about the location and characteristics of files stored on a computer’s secondary ...
操作系统
... Which one is easer to use Windows / Linux 1. Windows temporarily keeps deleted files in Recycle Bin, while Linux rm delete them instantly. 2. Windows task manager allows us to kill processes with their program names, while Linux uses IDs to kill specific processes. 3. Windows starts an appropriate ...
... Which one is easer to use Windows / Linux 1. Windows temporarily keeps deleted files in Recycle Bin, while Linux rm delete them instantly. 2. Windows task manager allows us to kill processes with their program names, while Linux uses IDs to kill specific processes. 3. Windows starts an appropriate ...
powerpoint
... • structure - how is the OS organized? • sharing - how are resources shared among users? • naming - how are resources named by users or programs? • protection - how is one user/program protected from another? • security - how is the flow of information ...
... • structure - how is the OS organized? • sharing - how are resources shared among users? • naming - how are resources named by users or programs? • protection - how is one user/program protected from another? • security - how is the flow of information ...
Core System Services
... • Specify processes to be run when the specified run level is entered. • Specify certain actions or processes to be run if certain signals or user actions are indicated. ...
... • Specify processes to be run when the specified run level is entered. • Specify certain actions or processes to be run if certain signals or user actions are indicated. ...
ppt
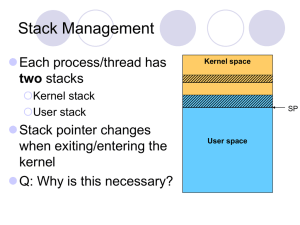
... Manage the resources Virtual memory, file system etc. are in application libraries Gives untrusted software as much control over hardware and software resources as possible Specialized applications can gain high performance without sacrificing the unmodified UNIX program ...
... Manage the resources Virtual memory, file system etc. are in application libraries Gives untrusted software as much control over hardware and software resources as possible Specialized applications can gain high performance without sacrificing the unmodified UNIX program ...
Operating System
... • 2 or more programs store in the main memory at the same time • when one job reeds to wait (e.g. I/O operation), CPU switch to another job to execute • when the first job finishes waiting, CPU will get back the first job to execute ...
... • 2 or more programs store in the main memory at the same time • when one job reeds to wait (e.g. I/O operation), CPU switch to another job to execute • when the first job finishes waiting, CPU will get back the first job to execute ...
Operating System
... • 2 or more programs store in the main memory at the same time • when one job reeds to wait (e.g. I/O operation), CPU switch to another job to execute • when the first job finishes waiting, CPU will get back the first job to execute ...
... • 2 or more programs store in the main memory at the same time • when one job reeds to wait (e.g. I/O operation), CPU switch to another job to execute • when the first job finishes waiting, CPU will get back the first job to execute ...
Operating System
... • 2 or more programs store in the main memory at the same time • when one job reeds to wait (e.g. I/O operation), CPU switch to another job to execute • when the first job finishes waiting, CPU will get back the first job to execute ...
... • 2 or more programs store in the main memory at the same time • when one job reeds to wait (e.g. I/O operation), CPU switch to another job to execute • when the first job finishes waiting, CPU will get back the first job to execute ...
system call.
... Job scheduling: Choose jobs to bring into memory. Memory management – the system must allocate the memory to several jobs. CPU scheduling – the system must choose among several jobs ready to run. Allocation of devices. ...
... Job scheduling: Choose jobs to bring into memory. Memory management – the system must allocate the memory to several jobs. CPU scheduling – the system must choose among several jobs ready to run. Allocation of devices. ...
Operating System Structure
... Security manager • The Security manager provides a mechanism for controlling access by programs, processes, or users to both system and user resources • The protection mechanism must: – distinguish between authorized and unauthorized usage – specify the controls to be imposed – provide a means of e ...
... Security manager • The Security manager provides a mechanism for controlling access by programs, processes, or users to both system and user resources • The protection mechanism must: – distinguish between authorized and unauthorized usage – specify the controls to be imposed – provide a means of e ...
Operating System
... • One person used the computer at a time • “Job Scheduling” • Libraries 1st procedure ...
... • One person used the computer at a time • “Job Scheduling” • Libraries 1st procedure ...
virtual machine
... and batch users. Many commands are given to the operating system by control statements which deal with: Process creation and management, Main-memory management, file-system access, I/O handling, secondary-storage management, Networking, Protection. ...
... and batch users. Many commands are given to the operating system by control statements which deal with: Process creation and management, Main-memory management, file-system access, I/O handling, secondary-storage management, Networking, Protection. ...
Chapter 1: Intro to OS
... 3. renamed MULTICS to “UNICS” (Uniplexed Information and Computer Service), later the spelling was changes to UNIX which is a trademark of Bell Lab. 4. Dennis Ritchie and Thompson at Bell Lab rewrote UNIX in C 5. AT&T Bell lab licensed UNIX to universities free, then for a ...
... 3. renamed MULTICS to “UNICS” (Uniplexed Information and Computer Service), later the spelling was changes to UNIX which is a trademark of Bell Lab. 4. Dennis Ritchie and Thompson at Bell Lab rewrote UNIX in C 5. AT&T Bell lab licensed UNIX to universities free, then for a ...
1.operating systems overview
... of the hardware from the programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
... of the hardware from the programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
1.operating systems overview
... of the hardware from the programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
... of the hardware from the programmer and provides the programmer with a convenient interface for using system resources (system calls) ...
Computer science The Tired Librarian 80
... Often, today’s computers have even more levels of caching ...
... Often, today’s computers have even more levels of caching ...
Operating Systems - Home - KSU Faculty Member websites
... • Timesharing (multitasking) is logical extension in which CPU switches jobs so frequently that users can interact with each job while it is running, creating interactive computing – Response time should be < 1 second – Each user has at least one program executing in memory process – If several job ...
... • Timesharing (multitasking) is logical extension in which CPU switches jobs so frequently that users can interact with each job while it is running, creating interactive computing – Response time should be < 1 second – Each user has at least one program executing in memory process – If several job ...
Operating System: A Software Engineering Perspective
... Idea: Implement OS as a set of layers The first description of this approach was Dijkstra’s THE system (1968!) Layer 5: Job Managers Execute users’ programs ...
... Idea: Implement OS as a set of layers The first description of this approach was Dijkstra’s THE system (1968!) Layer 5: Job Managers Execute users’ programs ...
Lecture 22 File-System Interface
... collection of similar records treated as a single entity have unique file names may restrict access ...
... collection of similar records treated as a single entity have unique file names may restrict access ...
3. Data Communications
... Operating systems, such as Macintosh System 7, DOS and Windows, are single user, designed for one person at a desktop computer Windows NT and UNIX on the other hand are network operating systems, because they are designed to manage multiple user requests at the same time ...
... Operating systems, such as Macintosh System 7, DOS and Windows, are single user, designed for one person at a desktop computer Windows NT and UNIX on the other hand are network operating systems, because they are designed to manage multiple user requests at the same time ...
Document
... • A filename potentially has two parts to it: – the filename (up to 8 letters) – the extension (up to three letters) • The “.” is merely a separator, used to keep the two elements apart, so that DOS can find files of a particular type. ...
... • A filename potentially has two parts to it: – the filename (up to 8 letters) – the extension (up to three letters) • The “.” is merely a separator, used to keep the two elements apart, so that DOS can find files of a particular type. ...
The Linux System
... /etc All the configuration files for the various software are stored here. Don't play with this directory. /home All users will have their 'My Documents' under this directory. If your id is rossi, your 'My Documents' (called home-directory) is /home/rossi. /lib The libraries required by system-appli ...
... /etc All the configuration files for the various software are stored here. Don't play with this directory. /home All users will have their 'My Documents' under this directory. If your id is rossi, your 'My Documents' (called home-directory) is /home/rossi. /lib The libraries required by system-appli ...
PowerPoint 2003 - FSU Computer Science
... How do we make different file systems work together, even across machines? How do we provide consistency, availability, and reliability to copies of a file across multiple machines? How do we handle very large data ...
... How do we make different file systems work together, even across machines? How do we provide consistency, availability, and reliability to copies of a file across multiple machines? How do we handle very large data ...