TF-Mobility
... › Activity level: HIGH › Number of participants 40-45 › Active members 20-25 › Activities/achievements: › Directories, Schema, PKI, Identity Federations, etc. › Supporting SCHAC, SCS, TACAR › Ad-hoc activities such as REFEDS › Supporting EuroCAMP › Engage close liaison with the Grid community Slide ...
... › Activity level: HIGH › Number of participants 40-45 › Active members 20-25 › Activities/achievements: › Directories, Schema, PKI, Identity Federations, etc. › Supporting SCHAC, SCS, TACAR › Ad-hoc activities such as REFEDS › Supporting EuroCAMP › Engage close liaison with the Grid community Slide ...
ePBX-100 User`s Manual
... 4.4 REBOOT SYSTEM ........................................................................................................41 ...
... 4.4 REBOOT SYSTEM ........................................................................................................41 ...
ICMP
... • but has no native mechanism for source host notification • This is where ICMP comes in • its used to report IP errors to the source host ...
... • but has no native mechanism for source host notification • This is where ICMP comes in • its used to report IP errors to the source host ...
MULTIMEDIA DATABASE MANAGEMENT SYSTEM ARCHITECTURE
... ◦ The number of queries that can be handled and the query response time depends, to a certain extent, on the speed of the system. ...
... ◦ The number of queries that can be handled and the query response time depends, to a certain extent, on the speed of the system. ...
INTERNET PROTOCOL IP datagram format is shown in
... reach the destination network. ii) A router will return a time exceeded message if the life time of the datagram expires. A host will send this message if it cannot complete reassembly within a life limit. iii) A syntactic or semantic error in an IP header will cause a parameter problem message to b ...
... reach the destination network. ii) A router will return a time exceeded message if the life time of the datagram expires. A host will send this message if it cannot complete reassembly within a life limit. iii) A syntactic or semantic error in an IP header will cause a parameter problem message to b ...
IMS_new_possibilities
... IMS Momentum The OMA (Open Mobile Alliance) “IMSinOMA” Requirements Document (RD) provides a single general use case which rationalizes IMS as the only globally standardized SIP-based architecture (to date) that addresses the needs of mobile operators in terms of session management, security, mob ...
... IMS Momentum The OMA (Open Mobile Alliance) “IMSinOMA” Requirements Document (RD) provides a single general use case which rationalizes IMS as the only globally standardized SIP-based architecture (to date) that addresses the needs of mobile operators in terms of session management, security, mob ...
TDMoIP - dspcsp
... that can readily use As we have shown, they are natural candidates for any application which needs to multiplex timeslots ...
... that can readily use As we have shown, they are natural candidates for any application which needs to multiplex timeslots ...
1. Workflow Manager Application – WFM
... Application is divided into several working panes: Information Pane, Design Pane and Log Message Pane. Each view has its own place in the application window. Information Pane presents different information based on the application state. Design pane it is used mainly by the VLBI operator for the VLB ...
... Application is divided into several working panes: Information Pane, Design Pane and Log Message Pane. Each view has its own place in the application window. Information Pane presents different information based on the application state. Design pane it is used mainly by the VLBI operator for the VLB ...
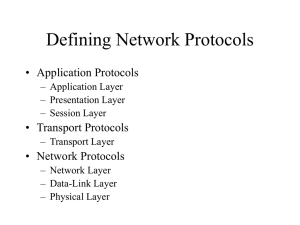
Defining Network Protocols
... arp -a or multi show/arp only local (router port) addresses shown ARP entries have a finite (timed) lifetime ARP entries are created by routers for non ethernet protocols (token ring, PPP) • tracing an ethernet address – Host system – Router – Switch ...
... arp -a or multi show/arp only local (router port) addresses shown ARP entries have a finite (timed) lifetime ARP entries are created by routers for non ethernet protocols (token ring, PPP) • tracing an ethernet address – Host system – Router – Switch ...
ACD: Average Call Duration is the average duration of the calls
... presence support, RADIUS/syslog accounting and authorization, XML-RPC-based remote control, etc. Web-based user provisioning, serweb, is available. SER's performance allows it to deal with operational burdens, such as broken network components, attacks, power-up reboots and a rapidly growing user p ...
... presence support, RADIUS/syslog accounting and authorization, XML-RPC-based remote control, etc. Web-based user provisioning, serweb, is available. SER's performance allows it to deal with operational burdens, such as broken network components, attacks, power-up reboots and a rapidly growing user p ...
山东建筑大学试卷 共 4页 第 1 页 至 学年 第 1 学期 课程名称 计算机
... 3 、 _______________________________________ is called transportlayer multiplexing and demultiplexing. 4 、 Computer networks that__________________________ are called virtual-circuit networks; Computer networks that ___________________ are called datagram networks. 5、There are 4 components in router’ ...
... 3 、 _______________________________________ is called transportlayer multiplexing and demultiplexing. 4 、 Computer networks that__________________________ are called virtual-circuit networks; Computer networks that ___________________ are called datagram networks. 5、There are 4 components in router’ ...
IF3614251429
... IP addresses, they end up blacklisting the entire Anonymzing network resulting in loss of service to genuine users thus effecting entire Anonymzing network services. Previously to counter these issues Nymble System was proposed and implemented which is essentially a combination of Anonymization Netw ...
... IP addresses, they end up blacklisting the entire Anonymzing network resulting in loss of service to genuine users thus effecting entire Anonymzing network services. Previously to counter these issues Nymble System was proposed and implemented which is essentially a combination of Anonymization Netw ...
Convergence of Voice, Video, and Data
... Identify terminology used to describe applications and other aspects of converged networks Describe several different applications available on converged networks Outline possible VoIP implementations and examine the costs and benefits of VoIP Explain methods for encoding analog voice or video signa ...
... Identify terminology used to describe applications and other aspects of converged networks Describe several different applications available on converged networks Outline possible VoIP implementations and examine the costs and benefits of VoIP Explain methods for encoding analog voice or video signa ...
Internetworking - National Tsing Hua University
... every datagram contains destination’s address if connected to destination network, then forward to host if not directly connected, then forward to some router forwarding table maps network number into next hop each host has a default router each router maintains a forwarding table ...
... every datagram contains destination’s address if connected to destination network, then forward to host if not directly connected, then forward to some router forwarding table maps network number into next hop each host has a default router each router maintains a forwarding table ...
1 Scope
... plane only) averaged during a predefined time span. This metric is one possible measure for the quality of experience (QoE) level a user experiences for the service applied. However, the data rate of the service application itself is lower than the experienced user throughput as additional protocol ...
... plane only) averaged during a predefined time span. This metric is one possible measure for the quality of experience (QoE) level a user experiences for the service applied. However, the data rate of the service application itself is lower than the experienced user throughput as additional protocol ...
No Slide Title
... When packets are sent from source to destination, a transmission time is taken which is the transmission delay. Transmission delay, T is the time period between the time that the first bit of the message enters to the fiber and the time the last bit of message exits from the other end. Transmi ...
... When packets are sent from source to destination, a transmission time is taken which is the transmission delay. Transmission delay, T is the time period between the time that the first bit of the message enters to the fiber and the time the last bit of message exits from the other end. Transmi ...
MIDCOM-1
... the T1 to the Internet. Place the jaws of the firewall across the T1 line lead, and bear down firmly. When your Internet service provider's network operations center calls to inform you that they have lost connectivity to your site, the firewall is correctly installed. (© Marcus Ranum) ...
... the T1 to the Internet. Place the jaws of the firewall across the T1 line lead, and bear down firmly. When your Internet service provider's network operations center calls to inform you that they have lost connectivity to your site, the firewall is correctly installed. (© Marcus Ranum) ...
6. Next Generation Networks A. Transition to NGN B. Key
... SIP - Session Initiation Protocol, IETF •SIP – client-server protocol, Rq from clients, Rs from servers. Participants are identified by SIP URLs. Requests can be sent through any transport protocol, such as UDP, or TCP. •SIP defines the end system to be used for the session, the communication media ...
... SIP - Session Initiation Protocol, IETF •SIP – client-server protocol, Rq from clients, Rs from servers. Participants are identified by SIP URLs. Requests can be sent through any transport protocol, such as UDP, or TCP. •SIP defines the end system to be used for the session, the communication media ...
l02network2
... numbers, and and sends each packet in turn Sends to a particular IP address and port Flow control — doesn’t send more packets than receiver is prepared to receive On receive side, receives packets, reassembles them into messages Computes a checksum for each packet and compares it to checksum ...
... numbers, and and sends each packet in turn Sends to a particular IP address and port Flow control — doesn’t send more packets than receiver is prepared to receive On receive side, receives packets, reassembles them into messages Computes a checksum for each packet and compares it to checksum ...
An Examination of Remote Access Help Desk Cases
... – Indicates a possibly new authentication step – Puts the user in a new application and access rights context – Potentially grants the user new privileges – Can be modeled as a service description ...
... – Indicates a possibly new authentication step – Puts the user in a new application and access rights context – Potentially grants the user new privileges – Can be modeled as a service description ...
The Promise of IMS: Will it Deliver
... Mobile networks WLAN/WiMax Hotspots UMA Access Fixed Access ...
... Mobile networks WLAN/WiMax Hotspots UMA Access Fixed Access ...
al najah national university faculty of engineering computer
... The Application An Application in IIS is and ASP is the whole ASP files in a virtual directory and its subdirectories. The application starts when the first user requests an .asp file from the application after the server has been turned on, this triggers an event handler written in the global.asa ...
... The Application An Application in IIS is and ASP is the whole ASP files in a virtual directory and its subdirectories. The application starts when the first user requests an .asp file from the application after the server has been turned on, this triggers an event handler written in the global.asa ...