Novell IPX - Austin Community College
... As hosts come online, they contact the DHCP server and request address information. The DHCP server selects an address and allocates it to that host. The address is only "leased" to the host, so the host periodically contacts the DHCP server to extend the lease. This lease mechanism ensures that hos ...
... As hosts come online, they contact the DHCP server and request address information. The DHCP server selects an address and allocates it to that host. The address is only "leased" to the host, so the host periodically contacts the DHCP server to extend the lease. This lease mechanism ensures that hos ...
Use the following IP address
... • The VPN is often managed by client/server software • Windows can be used to create a VPN connection instead of third-party software • VPN connection is a virtual connection – Setting up a tunnel over an existing connection A+ Guide to IT Technical Support, 9th Edition ...
... • The VPN is often managed by client/server software • Windows can be used to create a VPN connection instead of third-party software • VPN connection is a virtual connection – Setting up a tunnel over an existing connection A+ Guide to IT Technical Support, 9th Edition ...
BF-450(M)/BF-430/431
... using Windows 98/2000/XP and later operating systems. Note: Connect a computer to BF-450(M)/BF-430/431 Ethernet port directly should be with crossover Ethernet cable, if both connect to hub/switch should be with straight-through Ethernet cable. ...
... using Windows 98/2000/XP and later operating systems. Note: Connect a computer to BF-450(M)/BF-430/431 Ethernet port directly should be with crossover Ethernet cable, if both connect to hub/switch should be with straight-through Ethernet cable. ...
P2P-NAT - Universität Freiburg
... Summer 2008address as BBryan does. Applications must therefore authen- points (10.1.1.3:4321, 155.99.25.11:62000) on B’s priChristian Schindelhauer ticate all messages in some way to filter out such stray vate network, and by the endpoints (138.76.29.7:31000, traffic robustly. The messages might inc ...
... Summer 2008address as BBryan does. Applications must therefore authen- points (10.1.1.3:4321, 155.99.25.11:62000) on B’s priChristian Schindelhauer ticate all messages in some way to filter out such stray vate network, and by the endpoints (138.76.29.7:31000, traffic robustly. The messages might inc ...
IP Networks
... - wires, optical fibers or free space - common link speed - 14.4 kb/s - 2.4 Gb/s - end-to-end delays - micro sec in LAN - milliseconds on multiple hop paths. CIS 585 IP Networks ...
... - wires, optical fibers or free space - common link speed - 14.4 kb/s - 2.4 Gb/s - end-to-end delays - micro sec in LAN - milliseconds on multiple hop paths. CIS 585 IP Networks ...
Computer Networks and Internets
... computer to join multicast group at any time Arbitrary member to leave multicast group at any time Arbitrary computer to send message to a group (even if not a member) Internet Group Multicast Protocol (IGMP) Used ...
... computer to join multicast group at any time Arbitrary member to leave multicast group at any time Arbitrary computer to send message to a group (even if not a member) Internet Group Multicast Protocol (IGMP) Used ...
IP
Addressing
and
Forwarding
... Longest Prefix Match Forwarding • How to resolve mulPple matches? – Router idenPfies most specific prefix: longest prefix match (LPM) – Cute algorithmic problem to achieve fast lookups forwarding table ...
... Longest Prefix Match Forwarding • How to resolve mulPple matches? – Router idenPfies most specific prefix: longest prefix match (LPM) – Cute algorithmic problem to achieve fast lookups forwarding table ...
Chapter 25
... computer to join multicast group at any time Arbitrary member to leave multicast group at any time Arbitrary computer to send message to a group (even if not a member) Internet Group Multicast Protocol (IGMP) Used ...
... computer to join multicast group at any time Arbitrary member to leave multicast group at any time Arbitrary computer to send message to a group (even if not a member) Internet Group Multicast Protocol (IGMP) Used ...
Application Layer
... – Internet Corporation for Assigned Names and Numbers – Manages the assignment of both IP and application layer name space (domain names) • Both assigned at the same time and in groups • Manages some domains directly (e.g., .com, .org, .net) and • Authorizes private companies to become domain name r ...
... – Internet Corporation for Assigned Names and Numbers – Manages the assignment of both IP and application layer name space (domain names) • Both assigned at the same time and in groups • Manages some domains directly (e.g., .com, .org, .net) and • Authorizes private companies to become domain name r ...
More on the IP
... • IP is unreliable (does not catch errors) – But this is not bad – First, errors are caught--at the next-higher layer (transport) if TCP is used – Second, avoiding error checking at each hop between routers lowers router costs ...
... • IP is unreliable (does not catch errors) – But this is not bad – First, errors are caught--at the next-higher layer (transport) if TCP is used – Second, avoiding error checking at each hop between routers lowers router costs ...
Link Layer
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
DHCP for Wireless Ad
... Make every node in the network run the DHCP relay once configured Include the DHCP server IP address in AP beacons Unicast messages towards DHCP server rather than broadcasting ...
... Make every node in the network run the DHCP relay once configured Include the DHCP server IP address in AP beacons Unicast messages towards DHCP server rather than broadcasting ...
BlackDiamond® 10808 - Smart Technologies
... of a switching solution. The moment a single additional port is needed above and beyond what is available with any single switch hierarchical switching is required. As soon as more than one switch is needed for an application, up to half of each switch’s bandwidth may need to be dedicated just for s ...
... of a switching solution. The moment a single additional port is needed above and beyond what is available with any single switch hierarchical switching is required. As soon as more than one switch is needed for an application, up to half of each switch’s bandwidth may need to be dedicated just for s ...
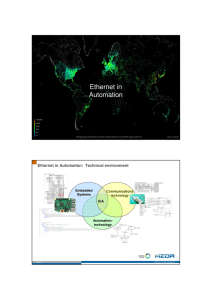
Ethernet in Automation
... conventional wiring All signals are wired to the central control • any information actual & centrally available • high wiring costs • bad shielding of sensitive signals • no signal check • large steps in extension effort ...
... conventional wiring All signals are wired to the central control • any information actual & centrally available • high wiring costs • bad shielding of sensitive signals • no signal check • large steps in extension effort ...
Client / Server Programming with TCP/IP Sockets
... The current version for IP supported by many modern networks is version 4, the next generation of IP is version 6 (IPv6) which is not widely supported as of this writting. IP is both a network addressing protocol and a network transport protocol. IP is a connection-less protocol that provides unreli ...
... The current version for IP supported by many modern networks is version 4, the next generation of IP is version 6 (IPv6) which is not widely supported as of this writting. IP is both a network addressing protocol and a network transport protocol. IP is a connection-less protocol that provides unreli ...
Lecture 6: Vector - Computer Science Division
... – Packet discarding: If packet arrives at switch and no room in buffer, packet is discarded (e.g., UDP) – Flow control: between pairs of receivers and senders; use feedback to tell sender when allowed to send next packet » Back-pressure: separate wires to tell to stop » Window: give original sender ...
... – Packet discarding: If packet arrives at switch and no room in buffer, packet is discarded (e.g., UDP) – Flow control: between pairs of receivers and senders; use feedback to tell sender when allowed to send next packet » Back-pressure: separate wires to tell to stop » Window: give original sender ...
Nikolaos-VMeshPresentationRNP
... The 1st usable address of the subnet is assigned to the router LAN interface. The remaining are assigned to user terminals using DHCP. One our network (e.g.): 10.152.0.0/27 RNP Workshop, 2005, Brazil Nikolaos Tsarmpopoulos, University of Thessaly ...
... The 1st usable address of the subnet is assigned to the router LAN interface. The remaining are assigned to user terminals using DHCP. One our network (e.g.): 10.152.0.0/27 RNP Workshop, 2005, Brazil Nikolaos Tsarmpopoulos, University of Thessaly ...
Networks and Networking
... Source – device that sends the message Destination – device that receives the message Handshaking – router establishes the connection between the source and the destination ...
... Source – device that sends the message Destination – device that receives the message Handshaking – router establishes the connection between the source and the destination ...
Module 4 – Switching Concepts
... Ethernet networks used to be built using repeaters. When the performance of these networks began to suffer because too many devices shared the same segment, network engineers added bridges to create multiple collision domains. As networks grew in size and complexity, the bridge evolved into the mode ...
... Ethernet networks used to be built using repeaters. When the performance of these networks began to suffer because too many devices shared the same segment, network engineers added bridges to create multiple collision domains. As networks grew in size and complexity, the bridge evolved into the mode ...
Chapter 5
... – Application server – File server – Print server Networks that include one or more servers can operate in client/server mode ...
... – Application server – File server – Print server Networks that include one or more servers can operate in client/server mode ...
Product Presentation - Orion Telecom Networks Inc., Voice
... LCAS feature supported to adjust the bandwidth automatically according the availability of E1 links without disturbing the current running services. ...
... LCAS feature supported to adjust the bandwidth automatically according the availability of E1 links without disturbing the current running services. ...
Chapter 3: Internetworking - ¡Bienvenido a paloalto.unileon.es!
... A switch or link failure might not have any serious effect on communication if it is possible to find an alternate route ...
... A switch or link failure might not have any serious effect on communication if it is possible to find an alternate route ...
Geographical Routing in Intermittently Connected Ad
... message until a forwarder becomes available due to node mobility. The nodes that are eligible to forward a packet are determined by a forwarding area related to the node performing the broadcast. In [2] Heissenbüttel et al. recommended a circle as the best forwarding area (see Figure 1a). Our simula ...
... message until a forwarder becomes available due to node mobility. The nodes that are eligible to forward a packet are determined by a forwarding area related to the node performing the broadcast. In [2] Heissenbüttel et al. recommended a circle as the best forwarding area (see Figure 1a). Our simula ...