Chapter 5
... – All frames have size L bits – Time is divided into slots of duration L/R seconds (= time to transmit one frame) – Nodes only transmit at the start of a slot – Nodes all know when the slots start – If a collision occurs, the nodes know that before the end of the slot occurs – There is a probability ...
... – All frames have size L bits – Time is divided into slots of duration L/R seconds (= time to transmit one frame) – Nodes only transmit at the start of a slot – Nodes all know when the slots start – If a collision occurs, the nodes know that before the end of the slot occurs – There is a probability ...
I/O Router Placement and Fine-Grained Routing
... each node. Ideally, the LNET routers would exist on the same module as less bandwidth-intensive nodes (such as a login nodes) to dedicate more bandwidth to routing. This is unfortunately impractical due to the sheer number of routers required to achieve sufficient bandwidth. Spider II has 36 InfiniB ...
... each node. Ideally, the LNET routers would exist on the same module as less bandwidth-intensive nodes (such as a login nodes) to dedicate more bandwidth to routing. This is unfortunately impractical due to the sheer number of routers required to achieve sufficient bandwidth. Spider II has 36 InfiniB ...
An Extended AODV Protocol for VoIP HuiYao Zhang Marek E. Bialkowski
... adverse properties of the wireless channel, dynamic topology and the lack of central administration. Because of these limitations, there is a challenge to meet the Quality of Service (QoS) of VoIP in terms of packet delivery ratio (PDR) and end-to-end (E2E) delay that has to be within an acceptable ...
... adverse properties of the wireless channel, dynamic topology and the lack of central administration. Because of these limitations, there is a challenge to meet the Quality of Service (QoS) of VoIP in terms of packet delivery ratio (PDR) and end-to-end (E2E) delay that has to be within an acceptable ...
Network Protocols
... Link layer addresses are tricky: A MN may not use ARP if it is using a FA COA. It needs to use the address of the FA as the destination address. If it is using a collocated COA, then it uses ARP to locate the default router using its COA as source. Note that if the ‘R’ bit is set is uses the FA addr ...
... Link layer addresses are tricky: A MN may not use ARP if it is using a FA COA. It needs to use the address of the FA as the destination address. If it is using a collocated COA, then it uses ARP to locate the default router using its COA as source. Note that if the ‘R’ bit is set is uses the FA addr ...
152-background - University of California, Santa Cruz
... Internet-to-go; deeply networked systems IP voice, IP devices Content routing: ISPs start to be CDNs, allow clients to obtain content based on its name from the best location ...
... Internet-to-go; deeply networked systems IP voice, IP devices Content routing: ISPs start to be CDNs, allow clients to obtain content based on its name from the best location ...
Network Simulator ns-2
... set cbr_(0) [new Application/Traffic/CBR] $cbr_(0) set packetSize_ 1000 $cbr_(0) set interval_ 4.0 $cbr_(0) set random_ 1 $cbr_(0) set maxpkts_ 10000 ...
... set cbr_(0) [new Application/Traffic/CBR] $cbr_(0) set packetSize_ 1000 $cbr_(0) set interval_ 4.0 $cbr_(0) set random_ 1 $cbr_(0) set maxpkts_ 10000 ...
other transport layer protocols for ad hoc wireless networks
... enhanced if it takes into account the nature of the network environment in which it is applied. Discusses the transport layer protocols that were designed specifically for ad hoc wireless networks. Even though interworking with TCP is very important, there exist several application scenarios suc ...
... enhanced if it takes into account the nature of the network environment in which it is applied. Discusses the transport layer protocols that were designed specifically for ad hoc wireless networks. Even though interworking with TCP is very important, there exist several application scenarios suc ...
OSPF - Computing Sciences
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
OSPF - Computing Sciences
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
... • An AS can be a collection of routers running a single IGP, or it can be a collection of routers running different protocols all belonging to one organization. • In either case, the outside world views the entire Autonomous System as a single entity. ...
Ethernet
... –Another capability emerges when only two nodes are connected. –In a network that uses twisted-pair cabling, one pair is used to carry the transmitted signal. A separate pair is used for the return or received signal. It is possible for signals to pass through both pairs simultaneously. –The capabil ...
... –Another capability emerges when only two nodes are connected. –In a network that uses twisted-pair cabling, one pair is used to carry the transmitted signal. A separate pair is used for the return or received signal. It is possible for signals to pass through both pairs simultaneously. –The capabil ...
Sockets
... name The address to assign to the socket. Often, you bound your listening socket to the special IP address INADDR_ANY. This allows your program to work without knowing the IP address of the machine it was running on, or, in the case of a machine with multiple network interfaces, it allows your serve ...
... name The address to assign to the socket. Often, you bound your listening socket to the special IP address INADDR_ANY. This allows your program to work without knowing the IP address of the machine it was running on, or, in the case of a machine with multiple network interfaces, it allows your serve ...
Ethernet - College of DuPage
... –Another capability emerges when only two nodes are connected. –In a network that uses twisted-pair cabling, one pair is used to carry the transmitted signal. A separate pair is used for the return or received signal. It is possible for signals to pass through both pairs simultaneously. –The capabil ...
... –Another capability emerges when only two nodes are connected. –In a network that uses twisted-pair cabling, one pair is used to carry the transmitted signal. A separate pair is used for the return or received signal. It is possible for signals to pass through both pairs simultaneously. –The capabil ...
The Internet and Its Uses
... In the course labs, you may be using Cisco routers with one of two types of physical serial cables. –The first cable type has a male DB-60 connector on the Cisco end. –The second type is a more compact version and has a Smart Serial connector on the Cisco device end. •Both cables use a large Winch ...
... In the course labs, you may be using Cisco routers with one of two types of physical serial cables. –The first cable type has a male DB-60 connector on the Cisco end. –The second type is a more compact version and has a Smart Serial connector on the Cisco device end. •Both cables use a large Winch ...
Lecture 5 - Lyle School of Engineering
... destinations and distances to its neighbors every 30 sec ("vector-distance" refers to these vectors of distances) Each router updates its routing table after receiving updates from its neighbors ...
... destinations and distances to its neighbors every 30 sec ("vector-distance" refers to these vectors of distances) Each router updates its routing table after receiving updates from its neighbors ...
IPv6 - DePaul University
... Unspecified address When a host does not know its own address. So it uses 128 0s. ...
... Unspecified address When a host does not know its own address. So it uses 128 0s. ...
Chapter 7: EIGRP
... best path: bandwidth and delay of the line • EIGRP can load balance across six unequal cost paths to a remote network (4 by default) ...
... best path: bandwidth and delay of the line • EIGRP can load balance across six unequal cost paths to a remote network (4 by default) ...
show ip route eigrp - Armstrong State University
... best path: bandwidth and delay of the line • EIGRP can load balance across six unequal cost paths to a remote network (4 by default) ...
... best path: bandwidth and delay of the line • EIGRP can load balance across six unequal cost paths to a remote network (4 by default) ...
K1297-G20 Protocol Tester
... mobile radio network infrastructure were the driving factors for the definition of IMA. The standard was defined in the late 1990s by the ATM Forum and describes how to use links with lower bandwidth (such as E1 and DS1) to form a “virtual” link with higher bandwidth. In order to save costs during t ...
... mobile radio network infrastructure were the driving factors for the definition of IMA. The standard was defined in the late 1990s by the ATM Forum and describes how to use links with lower bandwidth (such as E1 and DS1) to form a “virtual” link with higher bandwidth. In order to save costs during t ...
TCP/IP Transmission Control Protocol / Internet Protocol
... Handles high-level protocols, issues of representation, encoding, and dialog control. The TCP/IP combines all application-related issues into one layer, and assures this data is properly packaged for the next layer. ...
... Handles high-level protocols, issues of representation, encoding, and dialog control. The TCP/IP combines all application-related issues into one layer, and assures this data is properly packaged for the next layer. ...
No Slide Title
... Skype & Network Management -Bootstrapping It was with one of these IP address and port entries a SC established a TCP connection when a user used that SC to log onto the Skype network for the first time after installation. We call these IP address and port pairs bootstrap super nodes. After install ...
... Skype & Network Management -Bootstrapping It was with one of these IP address and port entries a SC established a TCP connection when a user used that SC to log onto the Skype network for the first time after installation. We call these IP address and port pairs bootstrap super nodes. After install ...
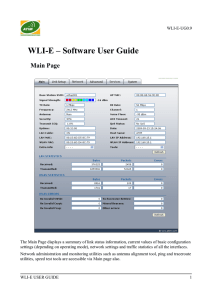
WLI-E – Software User Guide
... WLAN-OS powered device and PPPoE server through the PPP tunnel either way. As long as there is some network traffic being passed through the PPP tunnel, Received and Transmitted Bytes, Packets and Errors (if any) value will go on increasing. Refer to the Network section for more information aboutPPP ...
... WLAN-OS powered device and PPPoE server through the PPP tunnel either way. As long as there is some network traffic being passed through the PPP tunnel, Received and Transmitted Bytes, Packets and Errors (if any) value will go on increasing. Refer to the Network section for more information aboutPPP ...
Name servers
... permanent circuit. One example might be a telephone in the lobby of a public building, which is programmed to ring only the number of a telephone dispatcher. "Nailing down" a switched connection saves the cost of running a physical circuit between the two points. The resources in such a connection c ...
... permanent circuit. One example might be a telephone in the lobby of a public building, which is programmed to ring only the number of a telephone dispatcher. "Nailing down" a switched connection saves the cost of running a physical circuit between the two points. The resources in such a connection c ...