Point-to-Point Protocol (PPP)
... interfaces on a Cisco router. Cisco's HDLC is not necessarily compatible with other vendors' HDLC implementations. PPP implementations follow open standards and are almost always compatible. Thus, PPP is the protocol of choice when configuring serial links in a multivendor environment. ...
... interfaces on a Cisco router. Cisco's HDLC is not necessarily compatible with other vendors' HDLC implementations. PPP implementations follow open standards and are almost always compatible. Thus, PPP is the protocol of choice when configuring serial links in a multivendor environment. ...
Chapter 7 outline
... Payload Type (7 bits): Indicates type of encoding currently being used. If sender changes encoding in middle of conference, sender ...
... Payload Type (7 bits): Indicates type of encoding currently being used. If sender changes encoding in middle of conference, sender ...
檔案下載 - TWBBS.org 自由網域
... RFC 1771 Intelligent route selection based on most specific prefix and shortest Autonomous System (AS) path BGP version 4 is the current de facto exterior routing protocol in the Internet BGP- 4 is required for CIDR ...
... RFC 1771 Intelligent route selection based on most specific prefix and shortest Autonomous System (AS) path BGP version 4 is the current de facto exterior routing protocol in the Internet BGP- 4 is required for CIDR ...
DHCP - Personal Web Pages
... to network configuration and an IP address on a network it should otherwise not be allowed to use By flooding the DHCP server with requests for IP addresses o it is possible for an attacker to exhaust the pool of available IP addresses o disrupting normal network activity (a denial of service atta ...
... to network configuration and an IP address on a network it should otherwise not be allowed to use By flooding the DHCP server with requests for IP addresses o it is possible for an attacker to exhaust the pool of available IP addresses o disrupting normal network activity (a denial of service atta ...
Multi-Protocol Label Switching (MPLS)
... • MPLS is currently in use in IP-only networks and is standardized by the IETF in RFC 3031. It is deployed to connect as few as two facilities to very large deployments. For example, in the retail sector, it is not uncommon to see deployments of 2000 to 5000 locations to communicate transaction data ...
... • MPLS is currently in use in IP-only networks and is standardized by the IETF in RFC 3031. It is deployed to connect as few as two facilities to very large deployments. For example, in the retail sector, it is not uncommon to see deployments of 2000 to 5000 locations to communicate transaction data ...
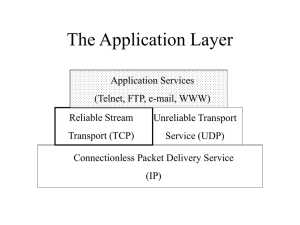
Link Layer
... Addresses: 6 bytes, frame is received by all adapters on a LAN and dropped if address does not match Type: indicates the higher layer protocol, mostly IP but others may be supported (such as Novell IPX and AppleTalk) CRC: checked at receiver, if error is detected, the frame is simply dropped 5: Data ...
... Addresses: 6 bytes, frame is received by all adapters on a LAN and dropped if address does not match Type: indicates the higher layer protocol, mostly IP but others may be supported (such as Novell IPX and AppleTalk) CRC: checked at receiver, if error is detected, the frame is simply dropped 5: Data ...
Note
... On the i80x86 the host byte order is Least Significant Byte first, whereas the network byte order, as used on the Internet, is Most Significant Byte first. From http://linux.die.net/man/7/ip There are several special addresses: INADDR_LOOPBACK (127.0.0.1) always refers to the local host via the loop ...
... On the i80x86 the host byte order is Least Significant Byte first, whereas the network byte order, as used on the Internet, is Most Significant Byte first. From http://linux.die.net/man/7/ip There are several special addresses: INADDR_LOOPBACK (127.0.0.1) always refers to the local host via the loop ...
Transitioning to IPv6
... > Advertisement messages are also sent when there are changes in link-layer addressing of a node on a local link ...
... > Advertisement messages are also sent when there are changes in link-layer addressing of a node on a local link ...
client-side buffering and playout delay
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
EIGRP and OSPF Comparison
... up) constrains the number of neighbors that a router can support and the number of neighbors that can be in an area. When the network is stable, link-state protocols minimize bandwidth usage by sending updates only when a change occurs. A hello mechanism ascertains reachability of neighbors. When a ...
... up) constrains the number of neighbors that a router can support and the number of neighbors that can be in an area. When the network is stable, link-state protocols minimize bandwidth usage by sending updates only when a change occurs. A hello mechanism ascertains reachability of neighbors. When a ...
Network Address Translation (NAT) Virtual Private Networks (VPN)
... • Need multicast routing if there are multiple internal networks • NAT gateway cannot advertise routes to Internet • NAT gateway must appear only as a host to external ...
... • Need multicast routing if there are multiple internal networks • NAT gateway cannot advertise routes to Internet • NAT gateway must appear only as a host to external ...
Chapter 7
... 86. Can a device obtain its IPv6 global unicast address dynamically and also be configured with multiple static IPv6 addresses on the same interface? ...
... 86. Can a device obtain its IPv6 global unicast address dynamically and also be configured with multiple static IPv6 addresses on the same interface? ...
ECx Ethernet Control Guide
... ECx Capabilities and Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 ECx Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... ECx Capabilities and Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 ECx Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
document
... • A process can use select to communicate over more than one socket at a time • Typically each socket provides a distinct service ...
... • A process can use select to communicate over more than one socket at a time • Typically each socket provides a distinct service ...
Routing Protocol vs. Routed Protocol
... For example, when there is a change in the topology, only those routers in the affected area receive the LSP and run the SPF algorithm. This can help isolate an unstable link to a specific area in the routing domain. ...
... For example, when there is a change in the topology, only those routers in the affected area receive the LSP and run the SPF algorithm. This can help isolate an unstable link to a specific area in the routing domain. ...
Routing Protocols - Cisco Networking Academy
... Not Scalable: Allows a maximum of 15 hops, so it can only be used for networks that connect no more than 16 routers in a series. Uses a lot of Bandwidth: Periodically sends complete copies of the entire routing table to directly connected neighbors. In a large network, this can cause a significant a ...
... Not Scalable: Allows a maximum of 15 hops, so it can only be used for networks that connect no more than 16 routers in a series. Uses a lot of Bandwidth: Periodically sends complete copies of the entire routing table to directly connected neighbors. In a large network, this can cause a significant a ...
Survey of Routing Protocols for Mobile Ad-hoc - dl.edi
... required to update them also grows[6]. This overhead is considered as the main weakness of DSDV. DSDV also pose a period of convergence before which routes will not be known and packets will be dropped [6]. This could also limit the number of nodes that can connect to the network since the overhead ...
... required to update them also grows[6]. This overhead is considered as the main weakness of DSDV. DSDV also pose a period of convergence before which routes will not be known and packets will be dropped [6]. This could also limit the number of nodes that can connect to the network since the overhead ...
socks for proxy - Linux Magazine
... ask the Socks proxy to open a port for the incoming data connection. The proxy sends two replies in response. The first contains the port and address at which the Socks server will listen for the incoming connection. The proxy does not send the second reply until the target server opens a connection ...
... ask the Socks proxy to open a port for the incoming data connection. The proxy sends two replies in response. The first contains the port and address at which the Socks server will listen for the incoming connection. The proxy does not send the second reply until the target server opens a connection ...
Cooperation between stations in wireless networks
... Select random IP address starting from the router’s IP address (first in the pool). MN sends 10 ARP requests in parallel starting from the random IP selected before. Same than scenario 1 except that we start to send ARP requests to 10 IP addresses in parallel, starting from the IP we last used in th ...
... Select random IP address starting from the router’s IP address (first in the pool). MN sends 10 ARP requests in parallel starting from the random IP selected before. Same than scenario 1 except that we start to send ARP requests to 10 IP addresses in parallel, starting from the IP we last used in th ...
CCNA (Cisco Certified Network Associate) Certification Exam
... The presentation layer provides a variety of coding and conversion functions that are applied to application layer data. These functions ensure that information sent from the application of one system will be readable by the application of another system. Some examples of presentation-layer coding a ...
... The presentation layer provides a variety of coding and conversion functions that are applied to application layer data. These functions ensure that information sent from the application of one system will be readable by the application of another system. Some examples of presentation-layer coding a ...
A New Location Layer for the TCP/IP Protocol Stack
... The IP addressing paradigm assumes that public addresses have the same interpretation (identify the same host) everywhere. On the contrary, private IP addresses have a local interpretation and can be bound to different hosts belonging to different domains (or private networks). With the location hea ...
... The IP addressing paradigm assumes that public addresses have the same interpretation (identify the same host) everywhere. On the contrary, private IP addresses have a local interpretation and can be bound to different hosts belonging to different domains (or private networks). With the location hea ...
Layer 3 Multiprotocol Label Switching Vir-
... PPP, POS and Ethernet, in the same manner as these Layer 2 technologies can run on MPLS network /4/. MPLS is normally used by Service Providers, however large scale corporations also build their own private MPLS network. The popularity of this technology is attracting customers as a result of its lo ...
... PPP, POS and Ethernet, in the same manner as these Layer 2 technologies can run on MPLS network /4/. MPLS is normally used by Service Providers, however large scale corporations also build their own private MPLS network. The popularity of this technology is attracting customers as a result of its lo ...
Computer Networking Tutorial - ECE, Rutgers
... - Autonomy: Different parts of the Internet are controlled by independent organizations. Even a sub-network controlled by the same multinational organization, such as IBM or Coca Cola, may cross many state borders. These independent organizations are generally in competition with each other and do n ...
... - Autonomy: Different parts of the Internet are controlled by independent organizations. Even a sub-network controlled by the same multinational organization, such as IBM or Coca Cola, may cross many state borders. These independent organizations are generally in competition with each other and do n ...
plug and play server load balancing and global server load
... What makes our anycast ARP unique is that the client request includes not only the anycast IP address, but also the requested application protocol (e.g., HTTP or DNS), transport protocol port numbers (e.g., 80, 8080, 53) , as well as the transport protocol type (e.g., either TCP or UDP). In lieu of ...
... What makes our anycast ARP unique is that the client request includes not only the anycast IP address, but also the requested application protocol (e.g., HTTP or DNS), transport protocol port numbers (e.g., 80, 8080, 53) , as well as the transport protocol type (e.g., either TCP or UDP). In lieu of ...