njit-etd2005-146 - New Jersey Institute of Technology
... could have moved given its known speed. A request zone is created which encloses S and the expected region in which the route request is sent. When D receives the request, it replies to S with the route reply. Ko and Vaidya [11] have provided various shapes for the request zone, to optimize the numb ...
... could have moved given its known speed. A request zone is created which encloses S and the expected region in which the route request is sent. When D receives the request, it replies to S with the route reply. Ko and Vaidya [11] have provided various shapes for the request zone, to optimize the numb ...
router`s
... Routers construct link-state packets that contain lists of network links and their associated costs. Link-state packets are transmitted to all routers in a network. All router therefore have an identical list of links in a network and construct identical list of links in a network and can cons ...
... Routers construct link-state packets that contain lists of network links and their associated costs. Link-state packets are transmitted to all routers in a network. All router therefore have an identical list of links in a network and construct identical list of links in a network and can cons ...
Contrail Architecture
... Juniper Networks® Contrail is an open-source software-defined networking (SDN) solution that automates and orchestrates the creation of highly scalable virtual networks. These virtual networks let you harness the power of the cloud—for applications and network services, increased business agility, a ...
... Juniper Networks® Contrail is an open-source software-defined networking (SDN) solution that automates and orchestrates the creation of highly scalable virtual networks. These virtual networks let you harness the power of the cloud—for applications and network services, increased business agility, a ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... to destination. In order to perform this task, the source and destination IP addresses are identified by unique fixed length addresses. In IPv4, a 32 bit numeric identifier was deemed sufficient when the Internet was created. However, as the Internet growth has been exponential it is clear that ther ...
... to destination. In order to perform this task, the source and destination IP addresses are identified by unique fixed length addresses. In IPv4, a 32 bit numeric identifier was deemed sufficient when the Internet was created. However, as the Internet growth has been exponential it is clear that ther ...
Node 1 `s Topology Table
... unicast NOT multicast • Multicast update packets sent when topology changes MUT ...
... unicast NOT multicast • Multicast update packets sent when topology changes MUT ...
(Subnet) Addresses - JNNCE ECE Manjunath
... Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific. ...
... Four levels of addresses are used in an internet employing the TCP/IP protocols: physical, logical, port, and specific. ...
Network+ (N10-005) Cram Notes
... APIP (Automatic Private IP Addressing) APIPA (Short for Automatic Private IP Addressing), is a feature that allows DHCP clients to automatically self-configure an IP address and subnet mask when a DHCP server isn't available. When a DHCP client boots up, it first looks for a DHCP server in order to ...
... APIP (Automatic Private IP Addressing) APIPA (Short for Automatic Private IP Addressing), is a feature that allows DHCP clients to automatically self-configure an IP address and subnet mask when a DHCP server isn't available. When a DHCP client boots up, it first looks for a DHCP server in order to ...
NetAdmin-10
... Link-state routers know more about the internetwork than any distance vector routing protocol. OSPF is an IP routing protocol that is completely link state. Link-state protocols send updates containing the state of their own links to all other routers on the network. ...
... Link-state routers know more about the internetwork than any distance vector routing protocol. OSPF is an IP routing protocol that is completely link state. Link-state protocols send updates containing the state of their own links to all other routers on the network. ...
EVVBU Marketing Strategy Development Session
... • EAP Cisco Wireless EAP (LEAP)—802.1X EAP authentication type developed by Cisco to provide dynamic per-user, persession WEP encryption keys. • PEAP—802.1X EAP authentication type that takes advantage of server-side EAP-TLS and supports a variety of different authentication methods, including logon ...
... • EAP Cisco Wireless EAP (LEAP)—802.1X EAP authentication type developed by Cisco to provide dynamic per-user, persession WEP encryption keys. • PEAP—802.1X EAP authentication type that takes advantage of server-side EAP-TLS and supports a variety of different authentication methods, including logon ...
Configuring the WT-4 for ftp (Infrastructure Mode)
... • Encryption: If you selected open system or shared key authentication, choose 64- or 128-bit WEP. If you selected WPA-PSK or WPA2-PSK authentication, choose TKIP or AES. The network in this example uses TKIP. • Encryption key: If you selected 64-bit WEP encryption, enter a 5-character ASCII or 10-d ...
... • Encryption: If you selected open system or shared key authentication, choose 64- or 128-bit WEP. If you selected WPA-PSK or WPA2-PSK authentication, choose TKIP or AES. The network in this example uses TKIP. • Encryption key: If you selected 64-bit WEP encryption, enter a 5-character ASCII or 10-d ...
IP LAB: Current Architecture
... Implementation and Evaluation of a Performance Enhancing Proxy for Wireless TCP ...
... Implementation and Evaluation of a Performance Enhancing Proxy for Wireless TCP ...
Arctic networking properties
... • The monitor should be used to verify the "end-to-end" operation of GPRS or Tunnel connection. This is achieved by periodically pinging the defined IP address. – In Tunnel mode pinging the private Tunnel IP of M2M GW – In plaing GPRS mode pinging suitable public IP address. ...
... • The monitor should be used to verify the "end-to-end" operation of GPRS or Tunnel connection. This is achieved by periodically pinging the defined IP address. – In Tunnel mode pinging the private Tunnel IP of M2M GW – In plaing GPRS mode pinging suitable public IP address. ...
Peer-to-peer networking with BitTorrent - UCLA
... donations from satisfied and kind BitTorrent users. [20] BitTorrent is completely free and open-source. This is doubtless an accomplice reason for the big success. But the way BitTorrent works also differs considerable from the other peer-topeer protocols out there. The problem with many “traditiona ...
... donations from satisfied and kind BitTorrent users. [20] BitTorrent is completely free and open-source. This is doubtless an accomplice reason for the big success. But the way BitTorrent works also differs considerable from the other peer-topeer protocols out there. The problem with many “traditiona ...
Improving Gnutella - Distributed Computing Group
... would tell you, through simple empirical observation alone, that the application was an incredible burden on modern networks and would probably never scale. I myself was just stupefied at the gross abuse of my limited bandwidth, Jordan Ritter - Why Gnutella Can't Scale. No, Really. ...
... would tell you, through simple empirical observation alone, that the application was an incredible burden on modern networks and would probably never scale. I myself was just stupefied at the gross abuse of my limited bandwidth, Jordan Ritter - Why Gnutella Can't Scale. No, Really. ...
4 Measuring Network Delay
... To Live. Originally, this data field in an IP packet header was supposed to contain a value representing the actual amount of time a packet could be flying around the Internet before a router would simply discard it. This is used to reduce the possibility of birth of endlessly looping packets around ...
... To Live. Originally, this data field in an IP packet header was supposed to contain a value representing the actual amount of time a packet could be flying around the Internet before a router would simply discard it. This is used to reduce the possibility of birth of endlessly looping packets around ...
OSI Network Layer OSI Layer 3 Network Fundamentals – Chapter 5 ١
... Next, the Network layer must provide services to “direct” these packets to their destination host. The source and destination hosts are not always connected to the same network. In fact, the packet might have to travel through many different networks. Along the way, each packet must be guided throug ...
... Next, the Network layer must provide services to “direct” these packets to their destination host. The source and destination hosts are not always connected to the same network. In fact, the packet might have to travel through many different networks. Along the way, each packet must be guided throug ...
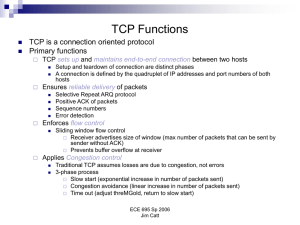
Factors that influence TCP performance
... Selective Repeat ARQ protocol Positive ACK of packets Sequence numbers ...
... Selective Repeat ARQ protocol Positive ACK of packets Sequence numbers ...
Three Challenges in Reliable Data Transport over
... • Guided by the End-to-End Argument • Fully conforms to the IP service model Cross-layer protocol design & optimizations Transport Network ...
... • Guided by the End-to-End Argument • Fully conforms to the IP service model Cross-layer protocol design & optimizations Transport Network ...
ppt
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
RARP / BOOTP / DHCP
... and broadcast (possibility to send a frame to all hosts on the network) the following protocols have evolved over time for the dynamic assignment of IP addresses. 1. RARP (Reverse ARP): RARP (defined in RFC903) is an early protocol for dynamic IP address assignment in Ethernet networks. RARP is seve ...
... and broadcast (possibility to send a frame to all hosts on the network) the following protocols have evolved over time for the dynamic assignment of IP addresses. 1. RARP (Reverse ARP): RARP (defined in RFC903) is an early protocol for dynamic IP address assignment in Ethernet networks. RARP is seve ...
Routing
... Shortest paths are precomputed offline by a special computer running the routing algorithm Resulted information is entered manually by the administrator into the routing tables Can not update automatically if there is a change in the network or failure Used in small networks Each router or host lear ...
... Shortest paths are precomputed offline by a special computer running the routing algorithm Resulted information is entered manually by the administrator into the routing tables Can not update automatically if there is a change in the network or failure Used in small networks Each router or host lear ...