here - FTP Directory Listing
... The BASH vulnerability ShellShock can be leveraged to remotely execute commands or run code on a vulnerable Linux or Mac OSX system ...
... The BASH vulnerability ShellShock can be leveraged to remotely execute commands or run code on a vulnerable Linux or Mac OSX system ...
CN2-Unit-1-Packet-switching-networks-by-Deepa
... node 3.Node 2 finds its shortest path is still trough node 4 but the cost has increased to 6.Node 3 finds its shortest path is still through node 4 but the cost has increased to 7.Node 4 and Node 5 finds the shortest path is not changed. Node 2 transmits its updates to node1,node4 and node 5 and tra ...
... node 3.Node 2 finds its shortest path is still trough node 4 but the cost has increased to 6.Node 3 finds its shortest path is still through node 4 but the cost has increased to 7.Node 4 and Node 5 finds the shortest path is not changed. Node 2 transmits its updates to node1,node4 and node 5 and tra ...
Virtual Private Networks (VPN`s)
... You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through. ...
... You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through. ...
Pi: A Practical Incentive Protocol for Delay Tolerant
... the TA and obtain its personal credit account (PCA) and personal reputation account (PRA) in the initialization phase. Later, when a DTN node has an available fast connection to the TA, it can report to the TA for credit and/or reputation clearance [20]. For example, in the vehicular DTN, a vehicle ...
... the TA and obtain its personal credit account (PCA) and personal reputation account (PRA) in the initialization phase. Later, when a DTN node has an available fast connection to the TA, it can report to the TA for credit and/or reputation clearance [20]. For example, in the vehicular DTN, a vehicle ...
Exam : 070-291 Title : Implementing, Managing, and
... You discover that Certkiller 6 cannot communicate with any of the other servers. You test network connectivity on Certkiller 6 by using the ping command. When you attempt to ping Certkiller 1, you receive the following error message: "Destination host unreachable". You verify that all other servers ...
... You discover that Certkiller 6 cannot communicate with any of the other servers. You test network connectivity on Certkiller 6 by using the ping command. When you attempt to ping Certkiller 1, you receive the following error message: "Destination host unreachable". You verify that all other servers ...
IP Datagram - La Salle University
... The creators of IP(v6) wanted to address some of the quality of service (QoS) issues. Packets can be identified as belonging to a particular "flow" so that packets that are part of a multimedia presentation that needs to arrive in "real time" can be provided a higher quality-ofservice relative to ot ...
... The creators of IP(v6) wanted to address some of the quality of service (QoS) issues. Packets can be identified as belonging to a particular "flow" so that packets that are part of a multimedia presentation that needs to arrive in "real time" can be provided a higher quality-ofservice relative to ot ...
Multicasting
... whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,].
• A sender simply sends data packets as they are available.
• Each router uses the network topology, the group
membership table, and the multicast gro ...
... whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,
The Network Layer
... Real-time traffic and mobile users are also becoming more common – IPv4 cannot support various QoS requirements ...
... Real-time traffic and mobile users are also becoming more common – IPv4 cannot support various QoS requirements ...
chap_19_1
... whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,].
• A sender simply sends data packets as they are available.
• Each router uses the network topology, the group
membership table, and the multicast gro ...
... whole network in the form (G, R). • Every router in the network maintains a group membership table with each entry being a tuple [S, G,
A Reference Implementation Architecture for Deploying a Highly
... In link aggregation mode, workload is balanced across all aggregated ports, providing a higherbandwidth “fat pipe” for network traffic. Should one port fail, traffic simply flows over the surviving ports. This mode typically does require some additional configuration of the external switch to which ...
... In link aggregation mode, workload is balanced across all aggregated ports, providing a higherbandwidth “fat pipe” for network traffic. Should one port fail, traffic simply flows over the surviving ports. This mode typically does require some additional configuration of the external switch to which ...
NAT: Network Address Translation
... In this scenario, there are more inside IP hosts than NAT pool-allocated addresses. The PAT feature of NAT is able to handle this situation using socket (socket = address: port) mappings. To ensure that multiple applications can use the same IP address from the limited IP pool, the "overload" featur ...
... In this scenario, there are more inside IP hosts than NAT pool-allocated addresses. The PAT feature of NAT is able to handle this situation using socket (socket = address: port) mappings. To ensure that multiple applications can use the same IP address from the limited IP pool, the "overload" featur ...
Measurement and Analysis of TCP Throughput Collapse in Cluster-based Storage Systems
... An analysis of the TCP traces obtained from simulation reveals that TCP retransmission timeouts are the primary cause of Incast (Figure 5).5 When goodput degrades, most servers still send their SRU quickly, but one or more other servers experience a timeout due to packet losses. The servers that fini ...
... An analysis of the TCP traces obtained from simulation reveals that TCP retransmission timeouts are the primary cause of Incast (Figure 5).5 When goodput degrades, most servers still send their SRU quickly, but one or more other servers experience a timeout due to packet losses. The servers that fini ...
Kyocera KR1 Mobile Router
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates uses and can radiate ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates uses and can radiate ...
Document
... – Gateway gets its 48-bit prefix from upstream – 2001:d0be:7922:1:fc2d:aeb2:99d2:e2b4 – Network prefix is 2001:dObe:7922:1 /64 – ISP’s network prefix 2001:D0BE /32 – ISP adds 16-bit subnet: 2001:d0be:7922/48 – At your gateway, tech adds 160bit subnet – Result: 2001:d0be:7922:1 /64 ...
... – Gateway gets its 48-bit prefix from upstream – 2001:d0be:7922:1:fc2d:aeb2:99d2:e2b4 – Network prefix is 2001:dObe:7922:1 /64 – ISP’s network prefix 2001:D0BE /32 – ISP adds 16-bit subnet: 2001:d0be:7922/48 – At your gateway, tech adds 160bit subnet – Result: 2001:d0be:7922:1 /64 ...
QFX10002 Fixed Ethernet Switches Product Description Data Sheet
... Architecture, which provides a simple, open, and smart approach to building data center networks. Additionally, the QFX10000 switches support Data Center Interconnect (DCI), critical to workload mobility and application availability. For networks evolving to SDN, the QFX10000 switches can integrate ...
... Architecture, which provides a simple, open, and smart approach to building data center networks. Additionally, the QFX10000 switches support Data Center Interconnect (DCI), critical to workload mobility and application availability. For networks evolving to SDN, the QFX10000 switches can integrate ...
ch4_1040106update
... A collision domain refers to a network segment An n-port bridge could separate one collision domain into n collision domains All these collision domains are still under the same broadcast domain unless VLANs are created All nodes can communicate with each other by broadcast at the link layer An n -p ...
... A collision domain refers to a network segment An n-port bridge could separate one collision domain into n collision domains All these collision domains are still under the same broadcast domain unless VLANs are created All nodes can communicate with each other by broadcast at the link layer An n -p ...
Evolution of P2P file sharing
... Gnutella v0.4: performance issues TR-2001-26: ”Peer-to-peer architecture case study: Gnutella network” Gnutella traffic (in bytes) by message types, November 2000: Query messages (i.e., user-generated traffic) ≈ 35% Ping/Pong messages (i.e., overhead traffic) ≈ 55% ...
... Gnutella v0.4: performance issues TR-2001-26: ”Peer-to-peer architecture case study: Gnutella network” Gnutella traffic (in bytes) by message types, November 2000: Query messages (i.e., user-generated traffic) ≈ 35% Ping/Pong messages (i.e., overhead traffic) ≈ 55% ...
Introduction Chapter 1
... To support large bulk-data transfers from applications such as web accesses , file trans fers and electronic mail, a network will have to accommodate high-bandwidth (higher than DSO) on-demand circuits between any two nodes of the network. Considering that the high speed circuit-switched network, ...
... To support large bulk-data transfers from applications such as web accesses , file trans fers and electronic mail, a network will have to accommodate high-bandwidth (higher than DSO) on-demand circuits between any two nodes of the network. Considering that the high speed circuit-switched network, ...
Basics of network lab - PolyU
... able to observe name resolution occurrences using DNS servers. Introduction An IP address is a unique network layer numbering system that end systems use in order to identify and communicate with each other. It is a dotted decimal notation with four numbers ranging from 0 to 255 separated by periods ...
... able to observe name resolution occurrences using DNS servers. Introduction An IP address is a unique network layer numbering system that end systems use in order to identify and communicate with each other. It is a dotted decimal notation with four numbers ranging from 0 to 255 separated by periods ...
ICN`12 ~ Coexist: A Hybrid Approach for Content Oriented Publish
... a hash based forwarding (in a sense similar to IP’s forwarding) engine significantly mitigates this forwarding performance penalty. We therefore explore the advantages of performing content centric forwarding at key points in combination with hash based forwarding (similar to IP forwarding) on the o ...
... a hash based forwarding (in a sense similar to IP’s forwarding) engine significantly mitigates this forwarding performance penalty. We therefore explore the advantages of performing content centric forwarding at key points in combination with hash based forwarding (similar to IP forwarding) on the o ...
SpeedStream Router
... freight collect. The end user shall include a return address, daytime telephone number and/or fax. The RMA number must be clearly marked on the outside of the package. C. Returned Products will be tested upon receipt by SSN. Products that pass all functional tests will be returned to the end user. D ...
... freight collect. The end user shall include a return address, daytime telephone number and/or fax. The RMA number must be clearly marked on the outside of the package. C. Returned Products will be tested upon receipt by SSN. Products that pass all functional tests will be returned to the end user. D ...
PDF
... node latency measurements on the Internet to determine a corresponding single point in a d-dimensional space for each node. The resulting embedded address, a virtual coordinate, can be used to select nodes. While the network embedding approach is applicable for a wide range of applications, it is ne ...
... node latency measurements on the Internet to determine a corresponding single point in a d-dimensional space for each node. The resulting embedded address, a virtual coordinate, can be used to select nodes. While the network embedding approach is applicable for a wide range of applications, it is ne ...
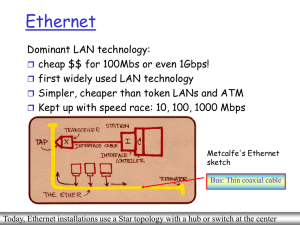
Ethernet Switches
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
Detecting and Preventing Rogue Devices on the Network
... In this paper MAC address and SSID are checked. Vendor type, media type and channel are not used to detect rogue APʼs. Detection components may be implemented through the use of a scanning feature that searches periodically for unauthorized devices or dedicated scanning ...
... In this paper MAC address and SSID are checked. Vendor type, media type and channel are not used to detect rogue APʼs. Detection components may be implemented through the use of a scanning feature that searches periodically for unauthorized devices or dedicated scanning ...
paper
... Figure 2—A simple scenario showing how network coding improves throughput. All links have a capacity of one message per unit of time. By sending the XOR of ai and bi on the middle link, we can deliver two messages per unit of time to both receivers. ...
... Figure 2—A simple scenario showing how network coding improves throughput. All links have a capacity of one message per unit of time. By sending the XOR of ai and bi on the middle link, we can deliver two messages per unit of time to both receivers. ...