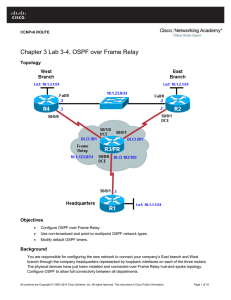
Chapter 3 Lab 3-4, OSPF over Frame Relay
... Use non-broadcast and point-to-multipoint OSPF network types. ...
... Use non-broadcast and point-to-multipoint OSPF network types. ...
Chapter 5
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
Chapter 5 outline
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
L347176
... because of overdone bandwidth used by some companies hence making the use of MPLS much more alluring. One more similarity would be that between ATM (also referred to as Asynchronous Transfer Mode) MPLS when comparing the two have many differences both offer connection oriented service to allow for t ...
... because of overdone bandwidth used by some companies hence making the use of MPLS much more alluring. One more similarity would be that between ATM (also referred to as Asynchronous Transfer Mode) MPLS when comparing the two have many differences both offer connection oriented service to allow for t ...
Network Primer - CS 4474
... •Many operating systems impose limits on how many simultaneous TCP/IP connections they can support. •Operating system does not need to keep UDP connection information for every peer host, UDP/IP is more appropriate for large-scale distributed systems where each host communicates with many destinatio ...
... •Many operating systems impose limits on how many simultaneous TCP/IP connections they can support. •Operating system does not need to keep UDP connection information for every peer host, UDP/IP is more appropriate for large-scale distributed systems where each host communicates with many destinatio ...
Model Answers Mid-Semester Test 2010
... d. Subnet 500: Note that the subnet 500 is not the last possible subnet, it is the last subnet used by the organization. To find the first address in subnet 500, we need to add 16,351,232 (499 x 32678) in base 256 (0. 249.128.0) to the first address in subnet 1. We have 16.0.0.0 + 0.249.128.0 = 16.2 ...
... d. Subnet 500: Note that the subnet 500 is not the last possible subnet, it is the last subnet used by the organization. To find the first address in subnet 500, we need to add 16,351,232 (499 x 32678) in base 256 (0. 249.128.0) to the first address in subnet 1. We have 16.0.0.0 + 0.249.128.0 = 16.2 ...
iCAMView - SuperDroid Robots
... surveillance. It can be accessed from anywhere in the world via a standard browser by entering the IP, account and password. Each system can simultaneously support any two combinations of USB PC cameras be it regular, infrared or pan-tilt. With its built-in web-server, iCAMView can stream video imag ...
... surveillance. It can be accessed from anywhere in the world via a standard browser by entering the IP, account and password. Each system can simultaneously support any two combinations of USB PC cameras be it regular, infrared or pan-tilt. With its built-in web-server, iCAMView can stream video imag ...
Understanding Firewall Basics
... contains the source and final destination IP addresses, as well as a fragment position number, but only a small part of the original TCP information. Two aspects of fragments are important: _ To speed up things after crossing the network link that allows only a smaller size, the IP fragments are no ...
... contains the source and final destination IP addresses, as well as a fragment position number, but only a small part of the original TCP information. Two aspects of fragments are important: _ To speed up things after crossing the network link that allows only a smaller size, the IP fragments are no ...
WWW Server Load Balancing Technique Employing Passive Measurement of Server Performance Satoru Ohta
... TCP SYN messages is used to detect SYN flood Denial of Services (DoS) attack. However, the abovementioned characteristics of TCP SYN and SYN ACK messages have not been investigated from the viewpoint of server load balancing. The technique reported in Reference [13] utilizes TCP SYN/SYN ACK messages ...
... TCP SYN messages is used to detect SYN flood Denial of Services (DoS) attack. However, the abovementioned characteristics of TCP SYN and SYN ACK messages have not been investigated from the viewpoint of server load balancing. The technique reported in Reference [13] utilizes TCP SYN/SYN ACK messages ...
Implementing OpenLISP with LISP+ALT
... There have been several protocols suggested in the Routing Research Group that provide a locator id split; the Locator ID Separation Protocol [1] (LISP) is one of them. The locator ID Separation protocol is a mapping and encapsulation implementation of the locator id split. To realise a locator id s ...
... There have been several protocols suggested in the Routing Research Group that provide a locator id split; the Locator ID Separation Protocol [1] (LISP) is one of them. The locator ID Separation protocol is a mapping and encapsulation implementation of the locator id split. To realise a locator id s ...
power-point presentation - UNT College of Engineering
... Simple Message Transfer Protocol (SMTP): E-Mail ...
... Simple Message Transfer Protocol (SMTP): E-Mail ...
VLANs Virtual LANs
... floor would sometimes mean moving them into a new broadcast domain, which wasn’t always desirable. • To address this need, multiple broadcast domains had to be available in the same wiring closet. ...
... floor would sometimes mean moving them into a new broadcast domain, which wasn’t always desirable. • To address this need, multiple broadcast domains had to be available in the same wiring closet. ...
Internet Control Message Protocol
... To identify the next hop, traceroute sends a UDP packet with a TTL value of 2. The first router decrements the TTL field by 1 and sends the datagram to the next router. The second router sees a TTL value of 1, discards the datagram, and returns the Time-Exceeded message to the source. This process ...
... To identify the next hop, traceroute sends a UDP packet with a TTL value of 2. The first router decrements the TTL field by 1 and sends the datagram to the next router. The second router sees a TTL value of 1, discards the datagram, and returns the Time-Exceeded message to the source. This process ...
This chapter covers the following key topics: • Overview of routers
... and are considered to be more-complex routing protocols. Link-state protocols work on the basis that routers exchange information elements, called link states, which carry information about links and nodes in the routing domain. This means that routers running link-state protocols do not exchange ro ...
... and are considered to be more-complex routing protocols. Link-state protocols work on the basis that routers exchange information elements, called link states, which carry information about links and nodes in the routing domain. This means that routers running link-state protocols do not exchange ro ...
EdgeRouter Lite User Guide
... • Name Server • Domain Name • NTP 2. Configure the interfaces on the Dashboard tab; see “Interfaces” on page 11 for more information. 3. Configure OSPF settings on the Routing > OSPF tab; see “OSPF” on page 16 for more information. Ubiquiti Networks, Inc. ...
... • Name Server • Domain Name • NTP 2. Configure the interfaces on the Dashboard tab; see “Interfaces” on page 11 for more information. 3. Configure OSPF settings on the Routing > OSPF tab; see “OSPF” on page 16 for more information. Ubiquiti Networks, Inc. ...
ATCP: TCP for Mobile Ad Hoc Networks
... TCP periodically generates probe packets while in persist mode. When, eventually, the receiver is connected to the sender, it responds to these probe packets with a duplicate ACK (or a data packet). This removes TCP from persist mode and moves ATCP back into normal state. Benefits of ATCP How does t ...
... TCP periodically generates probe packets while in persist mode. When, eventually, the receiver is connected to the sender, it responds to these probe packets with a duplicate ACK (or a data packet). This removes TCP from persist mode and moves ATCP back into normal state. Benefits of ATCP How does t ...
“Eth” Layer
... implementing the UNI-C processing functions to the port in Service Provider’s Edge Device, implementing the UNI-N processing functions. Or … – The link between the ports of the Provider’s Edge Devices in two different Service Providers implementing the E-NNI processing function ...
... implementing the UNI-C processing functions to the port in Service Provider’s Edge Device, implementing the UNI-N processing functions. Or … – The link between the ports of the Provider’s Edge Devices in two different Service Providers implementing the E-NNI processing function ...
CISSP Guide to Security Essentials, Ch4
... – Early packet-switched technology that used to transmit data between locations at a lower cost than dedicated DS-1 circuits – Switched Virtual Circuits (SVCs) and Permanent ...
... – Early packet-switched technology that used to transmit data between locations at a lower cost than dedicated DS-1 circuits – Switched Virtual Circuits (SVCs) and Permanent ...