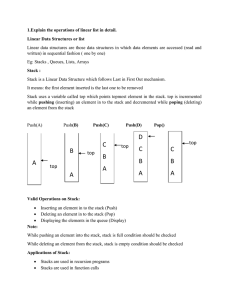
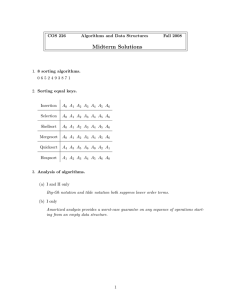
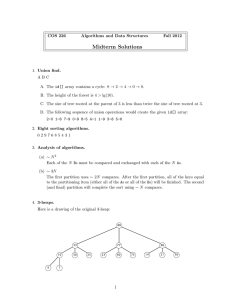
presentation
... Hash Objects enables you to handle data using dynamic keys within temporary datasets. ...
... Hash Objects enables you to handle data using dynamic keys within temporary datasets. ...
Data Structures Part 2
... ● Hash tables (hashmaps) an efficient data structure for storing dynamic data. ● Hash tables are good for doing a quick search on things. ● commonly implemented as an array of linked lists (hash tables with chaining). ● Each data item is associated with a key that determines its location. ...
... ● Hash tables (hashmaps) an efficient data structure for storing dynamic data. ● Hash tables are good for doing a quick search on things. ● commonly implemented as an array of linked lists (hash tables with chaining). ● Each data item is associated with a key that determines its location. ...
Solutions
... a. What is a hash function? A function to generate a number from a key b. What is a desirable property of hash functions? Numbers generated from keys are spread out uniformly in a range c. What is a perfect hash function? Every key is assigned a unique number d. What is a collision? Identical numbe ...
... a. What is a hash function? A function to generate a number from a key b. What is a desirable property of hash functions? Numbers generated from keys are spread out uniformly in a range c. What is a perfect hash function? Every key is assigned a unique number d. What is a collision? Identical numbe ...
previous-qns-and-answers
... •More evenly distributed digit positions are extracted and used for hashing purposes. ...
... •More evenly distributed digit positions are extracted and used for hashing purposes. ...
Priority Queues and Hashing
... this leaves a hole that needs to be refilled. To do that, find a leaf to be dropped, put its key value into the root node, and delete the leaf. The new value in the root may violate the heap property. Use the technique from the algorithm “heapify” to correct such violations. Describe your implementa ...
... this leaves a hole that needs to be refilled. To do that, find a leaf to be dropped, put its key value into the root node, and delete the leaf. The new value in the root may violate the heap property. Use the technique from the algorithm “heapify” to correct such violations. Describe your implementa ...
Using Hash Components
... • Generally, Key order should follow data hierarchy • Within a program, keys should follow function › The fewer the better › Save listing order until last ...
... • Generally, Key order should follow data hierarchy • Within a program, keys should follow function › The fewer the better › Save listing order until last ...
Midterm Solutions
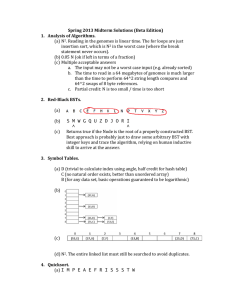
... (b) To determine whether the ith line is involved in an intersection with 3 (or more) lines: • Create a symbol table with key = point, value = list (say, a queue) of lines. • For each line j 6= i in order: – Compute the intersection point p between line i and line j. – If they don’t intersect, conti ...
... (b) To determine whether the ith line is involved in an intersection with 3 (or more) lines: • Create a symbol table with key = point, value = list (say, a queue) of lines. • For each line j 6= i in order: – Compute the intersection point p between line i and line j. – If they don’t intersect, conti ...
Table Lookup
... Theoretically, looking up an item by searching a list of N items and making key comparisons will, on average, require O(log N) work. ...
... Theoretically, looking up an item by searching a list of N items and making key comparisons will, on average, require O(log N) work. ...
Hill, Thomas M
... Theoretically, looking up an item by searching a list of N items and making key comparisons will, on average, require O(log N) work. As with sorting, we can “cheat” this result by organizing the data so that the search may be carried out with no (or very few) key comparisons. ...
... Theoretically, looking up an item by searching a list of N items and making key comparisons will, on average, require O(log N) work. As with sorting, we can “cheat” this result by organizing the data so that the search may be carried out with no (or very few) key comparisons. ...
Midterm Solutions
... I. Design a priority queue implementation that performs insert, max, and delete-max in ∼ 31 lg N compares per operation, where N is the number of comparable keys in the data structure. This would violate the ∼ N lg N lower bound for sorting because you can sort an array by inserting N keys into a ma ...
... I. Design a priority queue implementation that performs insert, max, and delete-max in ∼ 31 lg N compares per operation, where N is the number of comparable keys in the data structure. This would violate the ∼ N lg N lower bound for sorting because you can sort an array by inserting N keys into a ma ...
Exercise
... Adding an element: Simple extension of the algorithm for finding an object • Compute the hash code to locate the bucket in which the element should be inserted • Try finding the object in that bucket • If it is already present, do nothing; otherwise, insert it Removing an element is equally simple • ...
... Adding an element: Simple extension of the algorithm for finding an object • Compute the hash code to locate the bucket in which the element should be inserted • Try finding the object in that bucket • If it is already present, do nothing; otherwise, insert it Removing an element is equally simple • ...
Midterm Solutions
... To insert a node in a binary heap, we place it in the next available leaf node and swim it up. Thus, 19, 26, 32, 35, and 38 are the only keys that might move. But, the last inserted key could not have been 38, because, then, 35 would have been the old root (which would violate heap order because the ...
... To insert a node in a binary heap, we place it in the next available leaf node and swim it up. Thus, 19, 26, 32, 35, and 38 are the only keys that might move. But, the last inserted key could not have been 38, because, then, 35 would have been the old root (which would violate heap order because the ...
pptx - Chair of Software Engineering
... Regardless of the number of elements in the linked list it takes a constant time to insert an item at cursor position. force of ARRAY: O (count) At worst the time for this operation grows proportionally to the number of elements in the array. ...
... Regardless of the number of elements in the linked list it takes a constant time to insert an item at cursor position. force of ARRAY: O (count) At worst the time for this operation grows proportionally to the number of elements in the array. ...
Cryptographic hashing - comp
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
Lecture No. 41 - Taleem-E
... 20n or 30n memory locations. If we combine all these the value will be 15n to 20n. Therefore the proportionality constant will be around 15 or 20 but it cant be n2 or n3. If this is the case then to store 100 items we do need 1002 or 1003 memory locations. There are some algorithms in which we requi ...
... 20n or 30n memory locations. If we combine all these the value will be 15n to 20n. Therefore the proportionality constant will be around 15 or 20 but it cant be n2 or n3. If this is the case then to store 100 items we do need 1002 or 1003 memory locations. There are some algorithms in which we requi ...
The Mathematics Behind the Birthday Attack
... I have presented to you how message integrity is maintained in a nutshell (actually the above is a very basic model and there is more but delving too deep into different types of Message Authentication Codes would be a digression). An important concept here is that when a tag is generated, it involve ...
... I have presented to you how message integrity is maintained in a nutshell (actually the above is a very basic model and there is more but delving too deep into different types of Message Authentication Codes would be a digression). An important concept here is that when a tag is generated, it involve ...
$doc.title
... the remaining data points. P. One can simply use an ordered array (or equivalently, use a trivial hash function which simply returns the key as its own hash). Since there are only 65,536 different ...
... the remaining data points. P. One can simply use an ordered array (or equivalently, use a trivial hash function which simply returns the key as its own hash). Since there are only 65,536 different ...
Hash table
In computing, a hash table (hash map) is a data structure used to implement an associative array, a structure that can map keys to values. A hash table uses a hash function to compute an index into an array of buckets or slots, from which the desired value can be found.Ideally, the hash function will assign each key to a unique bucket, but it is possible that two keys will generate an identical hash causing both keys to point to the same bucket. Instead, most hash table designs assume that hash collisions—different keys that are assigned by the hash function to the same bucket—will occur and must be accommodated in some way.In a well-dimensioned hash table, the average cost (number of instructions) for each lookup is independent of the number of elements stored in the table. Many hash table designs also allow arbitrary insertions and deletions of key-value pairs, at (amortized) constant average cost per operation.In many situations, hash tables turn out to be more efficient than search trees or any other table lookup structure. For this reason, they are widely used in many kinds of computer software, particularly for associative arrays, database indexing, caches, and sets.