Session 6
... and we are required to have the breadth first search of the graph. Here we will require the starting vertex from which this search will begin. First that vertex will be printed, then all the vertices, which are adjacent to it, are printed and so on. If we have a matrix and there are n vertices. Let ...
... and we are required to have the breadth first search of the graph. Here we will require the starting vertex from which this search will begin. First that vertex will be printed, then all the vertices, which are adjacent to it, are printed and so on. If we have a matrix and there are n vertices. Let ...
Burst Tries: A Fast, Efficient Data Structure for
... for example, if the documents to be indexed are in a variety of languages), the behaviour of a BST can be extremely poor. In the absence of a rebalancing technique to prevent sticks from occurring or to move common nodes towards the root, a BST is of limited use in practice for vocabulary accumulati ...
... for example, if the documents to be indexed are in a variety of languages), the behaviour of a BST can be extremely poor. In the absence of a rebalancing technique to prevent sticks from occurring or to move common nodes towards the root, a BST is of limited use in practice for vocabulary accumulati ...
CST4_Lesson 22_IsoTriangles
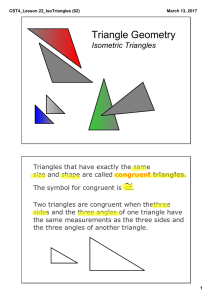
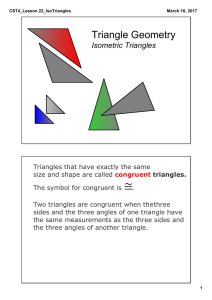
... Take the same two green "sticks" and angle and form a triangle with them that is different from the black one, if possible ...
... Take the same two green "sticks" and angle and form a triangle with them that is different from the black one, if possible ...
Summarizing Large Query Logs in Ettu
... the task of analyzing such a query log. She might first attempt to identify some aggregate properties about the log. For example, she might count how many times each table is accessed or the frequency with which different classes of join predicates occur. Unfortunately, such fine-grained properties ...
... the task of analyzing such a query log. She might first attempt to identify some aggregate properties about the log. For example, she might count how many times each table is accessed or the frequency with which different classes of join predicates occur. Unfortunately, such fine-grained properties ...
Efficient External-Memory Data Structures and Applications
... of the internal computation time and ignored the time spent on Input/Output (I/O). Theoretically one of the most commonly used machine models when designing algorithms is the Random Access Machine (RAM) (see e.g. [6, 125]). One main feature of the RAM model is that its memory consists of an (infinit ...
... of the internal computation time and ignored the time spent on Input/Output (I/O). Theoretically one of the most commonly used machine models when designing algorithms is the Random Access Machine (RAM) (see e.g. [6, 125]). One main feature of the RAM model is that its memory consists of an (infinit ...
Triangle Geometry - Math with Von Eschen
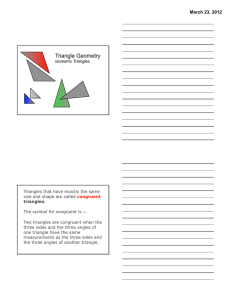
... 1. Theorem of Congruence SAS: Two triangles with corresponding congruent angle contained between two congruent corresponding sides are isometric. 2. Theorem of Congruence ASA: Two triangles with corresponding congruent side contained between two congruent corresponding angles are isometric. 3. Theor ...
... 1. Theorem of Congruence SAS: Two triangles with corresponding congruent angle contained between two congruent corresponding sides are isometric. 2. Theorem of Congruence ASA: Two triangles with corresponding congruent side contained between two congruent corresponding angles are isometric. 3. Theor ...
Master of Computer Applications DATA STRUCTURE
... Unit - 3 deals with one of the most important linear data structure linked list. Representation of linked list, their types, operations associated with linked list like searching, insertion and deletion of element in a linked are described in this unit. Unit - 4 focuses on stack data structure. In t ...
... Unit - 3 deals with one of the most important linear data structure linked list. Representation of linked list, their types, operations associated with linked list like searching, insertion and deletion of element in a linked are described in this unit. Unit - 4 focuses on stack data structure. In t ...
Amortized Bounds for Dynamic Orthogonal Range
... In solving the problem encapsulated by dynamic axes, we will end up with some form of reduction of coordinates to a smaller set of integers (though not to the set of ranks as in rank space reduction). A static axis of size u has coordinates from [u] and accommodates at most u points with distinct co ...
... In solving the problem encapsulated by dynamic axes, we will end up with some form of reduction of coordinates to a smaller set of integers (though not to the set of ranks as in rank space reduction). A static axis of size u has coordinates from [u] and accommodates at most u points with distinct co ...
Fundamental Data Structures
... "imperative" operations, these functions have no side effects. Therefore, the order in which they are evaluated is immaterial, and the same operation applied to the same arguments (including the same input states) will always return the same results (and output states). In the functional view, in pa ...
... "imperative" operations, these functions have no side effects. Therefore, the order in which they are evaluated is immaterial, and the same operation applied to the same arguments (including the same input states) will always return the same results (and output states). In the functional view, in pa ...
Linked Lists, Stacks, and Queues
... Write the definition of a structure and the definition of a class that can be used to create a node with this information in its data part. 4. Write the definition of a class that can be used to create nodes with the data part the data members of the class Date that you defined in exercise O7. 5. Wr ...
... Write the definition of a structure and the definition of a class that can be used to create a node with this information in its data part. 4. Write the definition of a class that can be used to create nodes with the data part the data members of the class Date that you defined in exercise O7. 5. Wr ...
Worst Case Efficient Data Structures
... We present two new comparison based priority queue implementations, with the following properties. The first implementation supports the operations FindMin, Insert and Meld in worst case constant time and Delete and DeleteMin in worst case time O(log n). The priority queues can be implemented on the ...
... We present two new comparison based priority queue implementations, with the following properties. The first implementation supports the operations FindMin, Insert and Meld in worst case constant time and Delete and DeleteMin in worst case time O(log n). The priority queues can be implemented on the ...
Visual Exploration of Web Spaces V´ıctor Pascual Cid
... have been incredibly lucky to count on the support of a lot of people who I would like to mention hereafter. First of all, I would like to offer my most sincere thanks to my supervisors: to Juan Carlos Dürsteler for introducing me into the field of Information Visualisation, for being the first to h ...
... have been incredibly lucky to count on the support of a lot of people who I would like to mention hereafter. First of all, I would like to offer my most sincere thanks to my supervisors: to Juan Carlos Dürsteler for introducing me into the field of Information Visualisation, for being the first to h ...
Quadtree
A quadtree is a tree data structure in which each internal node has exactly four children. Quadtrees are most often used to partition a two-dimensional space by recursively subdividing it into four quadrants or regions. The regions may be square or rectangular, or may have arbitrary shapes. This data structure was named a quadtree by Raphael Finkel and J.L. Bentley in 1974. A similar partitioning is also known as a Q-tree. All forms of quadtrees share some common features: They decompose space into adaptable cells Each cell (or bucket) has a maximum capacity. When maximum capacity is reached, the bucket splits The tree directory follows the spatial decomposition of the quadtree.