Unit 7 Powerpoint Presentation
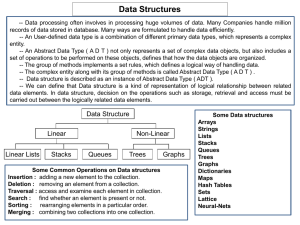
... -- Data structure is described as an instance of Abstract Data Type ( ADT ). -- We can define that Data structure is a kind of representation of logical relationship between related data elements. In data structure, decision on the operations such as storage, retrieval and access must be carried out ...
... -- Data structure is described as an instance of Abstract Data Type ( ADT ). -- We can define that Data structure is a kind of representation of logical relationship between related data elements. In data structure, decision on the operations such as storage, retrieval and access must be carried out ...
Balloon: A Forward-Secure Append-Only Persistent Authenticated
... logging system, similar to the history tree system by Crosby and Wallach [6]. Another closely related application is as an extension to Certificate Transparency (CT) [12], where Balloon can be used to provide efficient non-membership proofs, which are highly relevant in relation to certificate revoc ...
... logging system, similar to the history tree system by Crosby and Wallach [6]. Another closely related application is as an extension to Certificate Transparency (CT) [12], where Balloon can be used to provide efficient non-membership proofs, which are highly relevant in relation to certificate revoc ...
LCM ver.3: Collaboration of Array, Bitmap and Pre x Tree for
... store them. A vertex of the tree has an alphabet, thus a path of the tree gives a string. Each string is represented as the path from a representative vertex to the root. A vertex has no two children having the same alphabet, thus the position of the representative vertex of any string is unique. Fo ...
... store them. A vertex of the tree has an alphabet, thus a path of the tree gives a string. Each string is represented as the path from a representative vertex to the root. A vertex has no two children having the same alphabet, thus the position of the representative vertex of any string is unique. Fo ...
odd semester (2014 – 2015)
... 6. Define Data Structures? (Nov 2011) Data Structures is a way of organizing data that considers the data to stored and their relationship with each other. It is representation of the logical relationship between individual elements of data. DEPT OF IT ...
... 6. Define Data Structures? (Nov 2011) Data Structures is a way of organizing data that considers the data to stored and their relationship with each other. It is representation of the logical relationship between individual elements of data. DEPT OF IT ...
SnapQueue: Lock-Free Queue with Constant Time Snapshots
... WRITE and CAS operations differ from standard Scala syntax, which relies on the Unsafe class. These operations retain the standard Java volatile semantics, and are used to access volatile object fields. Second, volatile arrays are represented with a non-existent VolatileArray class. Finally, generic ...
... WRITE and CAS operations differ from standard Scala syntax, which relies on the Unsafe class. These operations retain the standard Java volatile semantics, and are used to access volatile object fields. Second, volatile arrays are represented with a non-existent VolatileArray class. Finally, generic ...
38 POINT LOCATION
... through q. We then compare against the separating chain and recursively search the left or right subtree. Thus, this separating chain method [LP77] inspects O(log n) tree nodes at a cost of O(log n) each, giving O(log2 n) query time. To reduce the query time, we can use fractional cascading [CG86, E ...
... through q. We then compare against the separating chain and recursively search the left or right subtree. Thus, this separating chain method [LP77] inspects O(log n) tree nodes at a cost of O(log n) each, giving O(log2 n) query time. To reduce the query time, we can use fractional cascading [CG86, E ...
CS163_Topic6
... of data items and look at each item in sequence. • This is called a sequential or linear search. • The sequential search quits as soon as it finds a copy of the search key in the array. If we are very lucky, the very first key examined may be the one we are looking for. This is the best possible cas ...
... of data items and look at each item in sequence. • This is called a sequential or linear search. • The sequential search quits as soon as it finds a copy of the search key in the array. If we are very lucky, the very first key examined may be the one we are looking for. This is the best possible cas ...
Package `data.tree`
... acme’s tree representation is accessed through its root, acme. Usage data(acme) Format A data.tree root Node Details • cost, only available for leaf nodes. Cost of the project. • p probability that a project will be undertaken. ...
... acme’s tree representation is accessed through its root, acme. Usage data(acme) Format A data.tree root Node Details • cost, only available for leaf nodes. Cost of the project. • p probability that a project will be undertaken. ...
Dynamic Data Structures: Orthogonal Range Queries and Update
... than previous worst-case efficient structures, under the assumption that the x-coordinates of the points are drawn from a smooth probabilistic distribution, and the y-coordinates are drawn from a class of probabilistic distributions that exhibit unbounded density. In Section 2.4 we waive the assumpt ...
... than previous worst-case efficient structures, under the assumption that the x-coordinates of the points are drawn from a smooth probabilistic distribution, and the y-coordinates are drawn from a class of probabilistic distributions that exhibit unbounded density. In Section 2.4 we waive the assumpt ...
Rank and select for succinct data structures
... bit 1 appears before the subsequence of size dlog ne2 containing the position i. The same happens in the second level of the directory structure. The final result is obtained using table lookups. The bits of the subsequence of size dlog ne containing the position i that could not be processed with t ...
... bit 1 appears before the subsequence of size dlog ne2 containing the position i. The same happens in the second level of the directory structure. The final result is obtained using table lookups. The bits of the subsequence of size dlog ne containing the position i that could not be processed with t ...
• Data Structures and Data Types
... last.next = new Node(); last = last.next;; last.item = StdIn.readString(); ...
... last.next = new Node(); last = last.next;; last.item = StdIn.readString(); ...
Circularly-linked list
... Sometimes, linked lists are used to implement associative arrays, and are in this context called association lists. There is very little good to be said about this use of linked lists; they are easily outperformed by other data structures such as self-balancing binary search trees even on small data ...
... Sometimes, linked lists are used to implement associative arrays, and are in this context called association lists. There is very little good to be said about this use of linked lists; they are easily outperformed by other data structures such as self-balancing binary search trees even on small data ...
A Comparison of Adaptive Radix Trees and Hash Tables
... the fan-out of the nodes because for each node there is exactly one branch for each possible partial key. For example, let us assume a radix tree that maps 32-bit integer keys to values of the same type. If we chose each level to represent a partial key of one byte, this results in a 4-level radix t ...
... the fan-out of the nodes because for each node there is exactly one branch for each possible partial key. For example, let us assume a radix tree that maps 32-bit integer keys to values of the same type. If we chose each level to represent a partial key of one byte, this results in a 4-level radix t ...
ps - Carnegie Mellon School of Computer Science
... reduce access time to large dataset even further in order to support interactive applications? Our approach is to use a small application-aware cache to speed up access to large datasets in interactive applications. The main idea is to set aside a relatively small portion of the system caches memory ...
... reduce access time to large dataset even further in order to support interactive applications? Our approach is to use a small application-aware cache to speed up access to large datasets in interactive applications. The main idea is to set aside a relatively small portion of the system caches memory ...
The following paper was originally published in the
... performing the requested operations. An error occurs when a value returned by the data structure does not agree with the corresponding value entered into the data structure. Blum et al. showed how to construct an online checker for RAMs using a variant of Merkle's hash-tree authentication scheme for ...
... performing the requested operations. An error occurs when a value returned by the data structure does not agree with the corresponding value entered into the data structure. Blum et al. showed how to construct an online checker for RAMs using a variant of Merkle's hash-tree authentication scheme for ...
Part III Data Structures
... 2. All leaf nodes are black. 3. For each node, all paths to descendant leaves contain the same number of black nodes. 4. If a node is red then both its children are black. The null-pointers in a binary search tree are replaced by pointers to special null-vertices, that do not carry any object-data. ...
... 2. All leaf nodes are black. 3. For each node, all paths to descendant leaves contain the same number of black nodes. 4. If a node is red then both its children are black. The null-pointers in a binary search tree are replaced by pointers to special null-vertices, that do not carry any object-data. ...
Binary search tree
In computer science, binary search trees (BST), sometimes called ordered or sorted binary trees, are a particular type of containers: data structures that store ""items"" (such as numbers, names and etc.) in memory. They allow fast lookup, addition and removal of items, and can be used to implement either dynamic sets of items, or lookup tables that allow finding an item by its key (e.g., finding the phone number of a person by name).Binary search trees keep their keys in sorted order, so that lookup and other operations can use the principle of binary search: when looking for a key in a tree (or a place to insert a new key), they traverse the tree from root to leaf, making comparisons to keys stored in the nodes of the tree and deciding, based on the comparison, to continue searching in the left or right subtrees. On average, this means that each comparison allows the operations to skip about half of the tree, so that each lookup, insertion or deletion takes time proportional to the logarithm of the number of items stored in the tree. This is much better than the linear time required to find items by key in an (unsorted) array, but slower than the corresponding operations on hash tables.They are a special case of the more general B-tree with order equal to two.