Data Structures and Algorithms for Data
... First, it is challenging to construct a collection in parallel by multiple processors. Traditionally, collections are backed by data structures with thread-safe variants of their update operations. Such data structures are called concurrent data structures. Their update operations require interproce ...
... First, it is challenging to construct a collection in parallel by multiple processors. Traditionally, collections are backed by data structures with thread-safe variants of their update operations. Such data structures are called concurrent data structures. Their update operations require interproce ...
Amortized Analysis and Union-Find - Algorithms for Massive Data Sets
... • Lemma. The amortized cost of Union(A,B) is O(α(n)). • Assume B made parent of A. • Real cost 1. Show increase in potential at most α(n). • Only A’s, B’s and the children of B’s potential can change. • potential of B’s children can only decrease. • A: decreases due to property 4 (before operation i ...
... • Lemma. The amortized cost of Union(A,B) is O(α(n)). • Assume B made parent of A. • Real cost 1. Show increase in potential at most α(n). • Only A’s, B’s and the children of B’s potential can change. • potential of B’s children can only decrease. • A: decreases due to property 4 (before operation i ...
Problem Solving with Algorithms and Data Structures
... Consider the automobile that you may have driven to school or work today. As a driver, a user of the car, you have certain interactions that take place in order to utilize the car for its intended purpose. You get in, insert the key, start the car, shift, brake, accelerate, and steer in order to dri ...
... Consider the automobile that you may have driven to school or work today. As a driver, a user of the car, you have certain interactions that take place in order to utilize the car for its intended purpose. You get in, insert the key, start the car, shift, brake, accelerate, and steer in order to dri ...
2009: Changqing Chen
... indexing technique designed for supporting box queries in an NDDS. Both our theoretical analysis and experimental results demonstrate that the new heuristics proposed for the BoND-tree improve the performance of box queries in an NDDS significantly. The Hybrid Data Space (HDS) is a multidimensional ...
... indexing technique designed for supporting box queries in an NDDS. Both our theoretical analysis and experimental results demonstrate that the new heuristics proposed for the BoND-tree improve the performance of box queries in an NDDS significantly. The Hybrid Data Space (HDS) is a multidimensional ...
Dynamic Fractional Cascading` ••
... block is &lready i n S or not. To do this we scan the neighbor block until its identifying bridge ( x',~') is reacbed and ched tbe in_S-flag x'.in_S. But if (x',~') i. not reached within b steps we can stop this scanning procedure. Then we know that the neighbor block is Ia.rger than b and therefore ...
... block is &lready i n S or not. To do this we scan the neighbor block until its identifying bridge ( x',~') is reacbed and ched tbe in_S-flag x'.in_S. But if (x',~') i. not reached within b steps we can stop this scanning procedure. Then we know that the neighbor block is Ia.rger than b and therefore ...
Chapter 11: Indexing and Hashing
... we cannot guarantee that K1 < K2 < K3 < . . . < Kn–1 but can guarantee K1 ≤ K2 ≤ K3 ≤ . . . ≤ Kn–1 Search-keys in the subtree to which Pi points are ≤ Ki,, but not necessarily < Ki, To see why, suppose same search key value V is present in two leaf node Li and Li+1. Then in parent node Ki mu ...
... we cannot guarantee that K1 < K2 < K3 < . . . < Kn–1 but can guarantee K1 ≤ K2 ≤ K3 ≤ . . . ≤ Kn–1 Search-keys in the subtree to which Pi points are ≤ Ki,, but not necessarily < Ki, To see why, suppose same search key value V is present in two leaf node Li and Li+1. Then in parent node Ki mu ...
Introduction to Data Structures Using the Standard Template Library
... of them as belonging to the family of linear data structures, because their components can be arranged in a straight sequence from one end to the other. The array is sequenced by its index values, and the list is sequenced by the logical relationship between each node and the nodes that immediately ...
... of them as belonging to the family of linear data structures, because their components can be arranged in a straight sequence from one end to the other. The array is sequenced by its index values, and the list is sequenced by the logical relationship between each node and the nodes that immediately ...
Testing and Quantifying Phylogenetic Signals
... An alternative to these methods of subdividing shape into separate characters is to treat shape as just one character, albeit a complex one that is inherently multidimensional (another option is to drop the notion of characters altogether and to focus on evolutionary change as shifts in phenotypic s ...
... An alternative to these methods of subdividing shape into separate characters is to treat shape as just one character, albeit a complex one that is inherently multidimensional (another option is to drop the notion of characters altogether and to focus on evolutionary change as shifts in phenotypic s ...
Course 3:Linked List - 天府学院数据结构精品课程
... In an ordered list, the data dare arranged according to a key,which is one or more fields used to identify the data or control their use. In a restricted list, data ,can be added or deleted at the end of the structure and processing is restricted to the operations on the data at the ends of the lis ...
... In an ordered list, the data dare arranged according to a key,which is one or more fields used to identify the data or control their use. In a restricted list, data ,can be added or deleted at the end of the structure and processing is restricted to the operations on the data at the ends of the lis ...
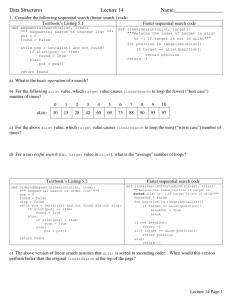
Data Structures Lecture 14 Name:__________________
... a) Assuming open-address with linear probing where would Paul Gray and then Kevin O’Kane be placed? Common rehashing strategies include the following. ...
... a) Assuming open-address with linear probing where would Paul Gray and then Kevin O’Kane be placed? Common rehashing strategies include the following. ...
On the Suitability of Suffix Arrays for Lempel
... The well-known LZ77 and LZSS encoding algorithms use a sliding window over the sequence of symbols, which has two sub-windows: the dictionary (holding the symbols already encoded) and the look-ahead-buffer (LAB), containing the symbols still to be encoded [10, 16]. As a string of symbols in the LAB ...
... The well-known LZ77 and LZSS encoding algorithms use a sliding window over the sequence of symbols, which has two sub-windows: the dictionary (holding the symbols already encoded) and the look-ahead-buffer (LAB), containing the symbols still to be encoded [10, 16]. As a string of symbols in the LAB ...
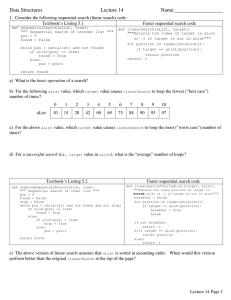
Data Structures Lecture 14 Name:__________________
... b) Similarly, binary search of a sorted array (or AVL tree) always uses a fixed search strategy for any given target value. For example, binary search always compares the target value with the middle element of the remaining portion of the array needing to be searched. If n is the number of items be ...
... b) Similarly, binary search of a sorted array (or AVL tree) always uses a fixed search strategy for any given target value. For example, binary search always compares the target value with the middle element of the remaining portion of the array needing to be searched. If n is the number of items be ...
Chapter 25 Java Data Structures
... To design and implement a dynamic list using a linked structure (§24.4). To design and implement a stack using an array list (§24.5). To design and implement a queue using a linked list (§24.6). ...
... To design and implement a dynamic list using a linked structure (§24.4). To design and implement a stack using an array list (§24.5). To design and implement a queue using a linked list (§24.6). ...
Nested Parallelism in Transactional Memory Kunal Agrawal Jeremy T. Fineman Jim Sukha
... and therefore must happen atomically. Note that all of X’s descendants must complete before X can attempt a commit. Since a worker may signal an abort of a transaction running on a (possibly different) worker whose descendants have not yet completed, the XCilk protocol for a transaction abort is mo ...
... and therefore must happen atomically. Note that all of X’s descendants must complete before X can attempt a commit. Since a worker may signal an abort of a transaction running on a (possibly different) worker whose descendants have not yet completed, the XCilk protocol for a transaction abort is mo ...
Diffracting Trees
... for testing in message-passing architectures. We found that, in sharedmemory systems, diffracting trees substantially outperform both combining trees and counting networks, currently the most effective known methods for shared counting. They scale better, giving higher throughput over a large number ...
... for testing in message-passing architectures. We found that, in sharedmemory systems, diffracting trees substantially outperform both combining trees and counting networks, currently the most effective known methods for shared counting. They scale better, giving higher throughput over a large number ...
A Practical Introduction to Data Structures and Algorithm
... 2. Related to costs and benefits is the notion of tradeoffs. For example, it is quite common to reduce time requirements at the expense of an increase in space requirements, or vice versa. Programmers face tradeoff issues regularly in all phases of software design and implementation, so the concept ...
... 2. Related to costs and benefits is the notion of tradeoffs. For example, it is quite common to reduce time requirements at the expense of an increase in space requirements, or vice versa. Programmers face tradeoff issues regularly in all phases of software design and implementation, so the concept ...
Introduction to Query Processing and Optimization
... perform natural joins and equi-joins and requires that each relation (r and s) be sorted by the common attributes between them (R ∩ S) [12]. The details for how this algorithm works can be found in [5] and [12] and will not be presented here. However, it is notable to point out that each record in r ...
... perform natural joins and equi-joins and requires that each relation (r and s) be sorted by the common attributes between them (R ∩ S) [12]. The details for how this algorithm works can be found in [5] and [12] and will not be presented here. However, it is notable to point out that each record in r ...
Binary search tree
In computer science, binary search trees (BST), sometimes called ordered or sorted binary trees, are a particular type of containers: data structures that store ""items"" (such as numbers, names and etc.) in memory. They allow fast lookup, addition and removal of items, and can be used to implement either dynamic sets of items, or lookup tables that allow finding an item by its key (e.g., finding the phone number of a person by name).Binary search trees keep their keys in sorted order, so that lookup and other operations can use the principle of binary search: when looking for a key in a tree (or a place to insert a new key), they traverse the tree from root to leaf, making comparisons to keys stored in the nodes of the tree and deciding, based on the comparison, to continue searching in the left or right subtrees. On average, this means that each comparison allows the operations to skip about half of the tree, so that each lookup, insertion or deletion takes time proportional to the logarithm of the number of items stored in the tree. This is much better than the linear time required to find items by key in an (unsorted) array, but slower than the corresponding operations on hash tables.They are a special case of the more general B-tree with order equal to two.