Windows 2000 Advanced Server
... workloads and high-priority processes. Server Clusters provide high availability for applications using failover. Multiple nodes use Network Load Balancing. NLB balances the load of IP traffic across a set of up to 32 identical servers. Note: With .Net server, users can set up clusters at different ...
... workloads and high-priority processes. Server Clusters provide high availability for applications using failover. Multiple nodes use Network Load Balancing. NLB balances the load of IP traffic across a set of up to 32 identical servers. Note: With .Net server, users can set up clusters at different ...
Methodology to Design Network Music Player iPhone
... their client. The clients initiate the communication session with server, which waits for incoming request. Client and server exchange messages in a request-response messaging pattern: The client sends a request and server returns a response. A server may receive request from many clients simultaneo ...
... their client. The clients initiate the communication session with server, which waits for incoming request. Client and server exchange messages in a request-response messaging pattern: The client sends a request and server returns a response. A server may receive request from many clients simultaneo ...
Communication - Computer Science Division
... If it does not, it needs to ask for another lease If client reboots after T sec all orphans are gone Problem: what is a good value of T? ...
... If it does not, it needs to ask for another lease If client reboots after T sec all orphans are gone Problem: what is a good value of T? ...
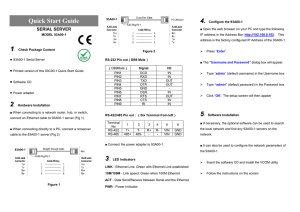
ATC-2000 TCP/IP TO RS
... connect an Ethernet cable to 93A00-1 server (Fig 1) ■ When connecting directly to a PC, connect a crossover cable to the 93A00-1 server (Fig 2) ...
... connect an Ethernet cable to 93A00-1 server (Fig 1) ■ When connecting directly to a PC, connect a crossover cable to the 93A00-1 server (Fig 2) ...
Network Installation Procedure - Chartwell
... and Server Installation when installing) - Register and activate the software (See ‟Guide for license registration and software activation”). - If Cabri II Plus is to be run from client workstations without having to install the software on each computer, ensure that the installation folder is visib ...
... and Server Installation when installing) - Register and activate the software (See ‟Guide for license registration and software activation”). - If Cabri II Plus is to be run from client workstations without having to install the software on each computer, ensure that the installation folder is visib ...
Bilkent University - Networking and Systems Research Group
... IP address to each of the connected computers. Then we get the IP address of each computer and run our programs, we did not come up any problems. In this mode our server program could send the images to 5 different computers without any problem. We have decided to use an architecture, which is used ...
... IP address to each of the connected computers. Then we get the IP address of each computer and run our programs, we did not come up any problems. In this mode our server program could send the images to 5 different computers without any problem. We have decided to use an architecture, which is used ...
LogiKal Installation Manual - Building Envelope Software
... Every time iUpdate is lauched, the zebedee.exe application establishes a secure connection over port 11965 to ORGADATA’s Firebird database. The technical specifications of the web server are: www.orgadata.com / IP:80.154.33.61. Available updates are requested depending on the dongle (dongle number / ...
... Every time iUpdate is lauched, the zebedee.exe application establishes a secure connection over port 11965 to ORGADATA’s Firebird database. The technical specifications of the web server are: www.orgadata.com / IP:80.154.33.61. Available updates are requested depending on the dongle (dongle number / ...
Example Concept
... Different clients may mount the servers in different places. Different clients have different views of the file systems ...
... Different clients may mount the servers in different places. Different clients have different views of the file systems ...
Computer Vision I: Introduction
... • Handles communications between networks including the Internet ...
... • Handles communications between networks including the Internet ...
Security for (Wireless) LANs
... rest of the network • Client software needed • Proprietary (unless IPsec or PPPoE) • Hard to scale • VPN-concentrators are expensive • Guest use hard (sometimes VPN in VPN) • All traffic encrypted ...
... rest of the network • Client software needed • Proprietary (unless IPsec or PPPoE) • Hard to scale • VPN-concentrators are expensive • Guest use hard (sometimes VPN in VPN) • All traffic encrypted ...
Computer Networks - Texas State Department of Computer Science
... Each computer has its own network address. A LAN is a private network and owned an operated by the company or institution. Ethernet (1970’s- Xerox PARC) operates at 10, 100, or 1000 Mbps (million bits per second, 1Gbps). Shared cable with transceivers and bridges Hubs to which every comput ...
... Each computer has its own network address. A LAN is a private network and owned an operated by the company or institution. Ethernet (1970’s- Xerox PARC) operates at 10, 100, or 1000 Mbps (million bits per second, 1Gbps). Shared cable with transceivers and bridges Hubs to which every comput ...
DRS5000 Configuration
... Log into the Webmin portion of the DRS5000 In the left menu click on Servers to open list Click on PostgreSQL Database Server On the right, click on Allowed Hosts At the bottom of the allowed hosts list, click on Create a new allowed host Click on the radio button to fill next to Network (the lower ...
... Log into the Webmin portion of the DRS5000 In the left menu click on Servers to open list Click on PostgreSQL Database Server On the right, click on Allowed Hosts At the bottom of the allowed hosts list, click on Create a new allowed host Click on the radio button to fill next to Network (the lower ...
Computer Networks - Texas State Department of Computer Science
... A LAN connects computers that are geographically close- (same building, campus). Each computer has its own network address. A LAN is a private network and owned an operated by the company or institution. Ethernet (1970’s- Xerox PARC) operates at 10, 100, or 1000 Mbps (million bits per second ...
... A LAN connects computers that are geographically close- (same building, campus). Each computer has its own network address. A LAN is a private network and owned an operated by the company or institution. Ethernet (1970’s- Xerox PARC) operates at 10, 100, or 1000 Mbps (million bits per second ...
acknowledgement
... application. For now, it can be used only a small network area. It cannot be used in places where a lot of computers are interconnected. The graphics can be made even more attractive. It lacks client to client communication. It doesn’t provide users the facility of sending pictures, emoticons or vid ...
... application. For now, it can be used only a small network area. It cannot be used in places where a lot of computers are interconnected. The graphics can be made even more attractive. It lacks client to client communication. It doesn’t provide users the facility of sending pictures, emoticons or vid ...
slides - CSE Home
... social interaction Perform other services -- printing, Web,... UW’s networks move more than trillion bytes per day ...
... social interaction Perform other services -- printing, Web,... UW’s networks move more than trillion bytes per day ...
AUROREAN™ POLICY SERVER 7000 AND 3000 SERIES Data Sheet
... system-wide VPN parameters. Policies are checked and updated during every VPN session, then locked down and enforced in the VPN client. Aurorean Policy Server can be securely administered from anywhere on the virtual network. Web-based configuration and SNMP monitoring agents allow for centralized m ...
... system-wide VPN parameters. Policies are checked and updated during every VPN session, then locked down and enforced in the VPN client. Aurorean Policy Server can be securely administered from anywhere on the virtual network. Web-based configuration and SNMP monitoring agents allow for centralized m ...
Ralph`s DHCP #2a
... Server selection option will include server identification on which client can base selection See “The Server Selection Option for DHCP,” by Stump and Gupta (draft-ietf-dhc-sso-00.txt) ...
... Server selection option will include server identification on which client can base selection See “The Server Selection Option for DHCP,” by Stump and Gupta (draft-ietf-dhc-sso-00.txt) ...
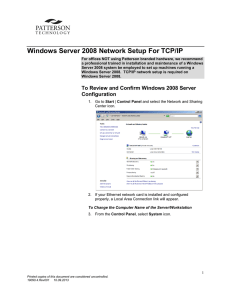
Windows Server 2008 Network Setup For TCP/IP
... 8. Select OK. You will be prompted to restart your computer. 9. Once you have restarted your computer, you can check your network connection by going to Network and Sharing Center and opening up the network. Any and all other computers in the same workgroup will be listed. ...
... 8. Select OK. You will be prompted to restart your computer. 9. Once you have restarted your computer, you can check your network connection by going to Network and Sharing Center and opening up the network. Any and all other computers in the same workgroup will be listed. ...
Network Applications
... • Note: applications with P2P architectures have client processes & server processes • Peers in P2P architectures have both client and server functionalities ...
... • Note: applications with P2P architectures have client processes & server processes • Peers in P2P architectures have both client and server functionalities ...
Basic Networking
... Client/Server Networks • Server: central computer used to facilitate communication and resource sharing between other computers on the network (called clients) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a comput ...
... Client/Server Networks • Server: central computer used to facilitate communication and resource sharing between other computers on the network (called clients) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a comput ...
Understanding the Transaction Breakdown Reports
... since the server typically sends data over multiple connections, and therefore is usually working while data is being transmitted over the network. For more details, see Understanding Download Time. ...
... since the server typically sends data over multiple connections, and therefore is usually working while data is being transmitted over the network. For more details, see Understanding Download Time. ...
Lag
In online gaming, lag is a noticeable delay between the action of players and the reaction of the server. Although lag may be caused by high latency, it may also occur due to insufficient processing power in the client(Screen-lag). Screen-Lag can also happened in single player games as well.The tolerance for lag depends heavily on the type of game. For instance, a strategy game or a turn-based game with a low pace may have a high threshold or even be mostly unaffected by high delays, whereas a twitch gameplay game such as a first-person shooter with a considerably higher pace may require significantly lower delay to be able to provide satisfying gameplay. But, the specific characteristics of the game matter. For example, fast chess is a turn-based game that is fast action and may not tolerate high lag. And, some twitch games can be designed such that only events that don't impact the outcome of the game introduce lag, allowing for fast local response most of the time.