History of the Internet
... • Variety of Hardware transmits the data between various networks. Five most important pieces of hardware are: – Hubs usesd to link groups of computers to one another and lets computers communicate with each other. – Bridges Links one LAN with another LAN – Gateways like Bridges but allow communicat ...
... • Variety of Hardware transmits the data between various networks. Five most important pieces of hardware are: – Hubs usesd to link groups of computers to one another and lets computers communicate with each other. – Bridges Links one LAN with another LAN – Gateways like Bridges but allow communicat ...
例外(exception)とは何か
... Allows sender to transmit multiple packets before receiving an acknowledgment Number of packets that can be sent is defined by the protocol and called the window Window size is determined by the empty buffer in receiver Receiver tells how many packets can be sent Sender transmits a number of packets ...
... Allows sender to transmit multiple packets before receiving an acknowledgment Number of packets that can be sent is defined by the protocol and called the window Window size is determined by the empty buffer in receiver Receiver tells how many packets can be sent Sender transmits a number of packets ...
Document
... Responsible for transmission of packets between nodes that are directly connected by a physical link. In a WAN transmission is between pairs of routers or between routers and hosts. In a LAN it is between any pair of hosts. The circuits and hardware that drive the network. It transmits sequences of ...
... Responsible for transmission of packets between nodes that are directly connected by a physical link. In a WAN transmission is between pairs of routers or between routers and hosts. In a LAN it is between any pair of hosts. The circuits and hardware that drive the network. It transmits sequences of ...
protocol port
... Packet may be lost or it is not following the sequence No intermediary– receive data from application and immediately send it Used when no error control needed. For process such as : DNS [53], echo [7], tftp [69], ...
... Packet may be lost or it is not following the sequence No intermediary– receive data from application and immediately send it Used when no error control needed. For process such as : DNS [53], echo [7], tftp [69], ...
Multimedia Streaming over the Internet
... experience and carries the power of multimedia into the classroom. Despite these promising aspects, multimedia streaming, is still quite a long way from providing a satisfactory viewing experience. The low-data transmission rates limit the quality of multimedia content transmitted to the recipient. ...
... experience and carries the power of multimedia into the classroom. Despite these promising aspects, multimedia streaming, is still quite a long way from providing a satisfactory viewing experience. The low-data transmission rates limit the quality of multimedia content transmitted to the recipient. ...
Part I: Introduction - University of Pittsburgh
... bit vs. two-dimentional bit parity Odd/even parity Internet checksum – IP/TCP layer Why is error checking needed in the upper layer? Cyclic Redunancy Check (CRC) CRC32 is widely used (e.g., Ethernet) ...
... bit vs. two-dimentional bit parity Odd/even parity Internet checksum – IP/TCP layer Why is error checking needed in the upper layer? Cyclic Redunancy Check (CRC) CRC32 is widely used (e.g., Ethernet) ...
Chapter06
... • Why two distinct layers? – Network layer is part of communication subnet and is run by the carrier (for WAN’s). – What if network layer is unreliable, loses packets or crashes? – Users have no control over subnet and cannot poor service problems – Need to put a layer on top of network layer that i ...
... • Why two distinct layers? – Network layer is part of communication subnet and is run by the carrier (for WAN’s). – What if network layer is unreliable, loses packets or crashes? – Users have no control over subnet and cannot poor service problems – Need to put a layer on top of network layer that i ...
Network Security
... X tries to find the MAC address of Victim V Hacker H responds to ARP request pretending to be V. All communication for V is captured by H. ...
... X tries to find the MAC address of Victim V Hacker H responds to ARP request pretending to be V. All communication for V is captured by H. ...
Network Applications
... Process: program running within a host. • within same host, two processes communicate using interinter-process communication (defined by OS). • processes in different hosts communicate by exchanging messages Client process: process that initiates communication Server process: process that waits to b ...
... Process: program running within a host. • within same host, two processes communicate using interinter-process communication (defined by OS). • processes in different hosts communicate by exchanging messages Client process: process that initiates communication Server process: process that waits to b ...
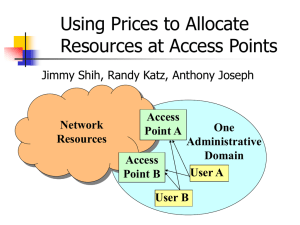
Design Review of Using Prices to Allocate Resources at a H
... Lots of people in a local area network trying to send and receive IP packets through a bottleneck link router. E.g. 500 students in a dorm sharing an access router. The bottleneck resource is connectionless. Users can adjust their bandwidth and duration usage. Only need to modify the access router a ...
... Lots of people in a local area network trying to send and receive IP packets through a bottleneck link router. E.g. 500 students in a dorm sharing an access router. The bottleneck resource is connectionless. Users can adjust their bandwidth and duration usage. Only need to modify the access router a ...
paper
... sender receives the ACKs, it updates its window size. Assume that ai packets are acknowledged in round i. Then, Wi+1 ← Wi + ai /Wi . TCP reduces the window size for congestion control using the following two methods. 1)Triple-duplicate (TD): When the sender receives four ACKs with the same sequence ...
... sender receives the ACKs, it updates its window size. Assume that ai packets are acknowledged in round i. Then, Wi+1 ← Wi + ai /Wi . TCP reduces the window size for congestion control using the following two methods. 1)Triple-duplicate (TD): When the sender receives four ACKs with the same sequence ...
Application Layer - Teknik Elektro UGM
... Code bits – Control functions, such as setup and termination of a session Window – Number of octets that the sender will accept Checksum – Calculated checksum of the header and data fields Urgent pointer – Indicates the end of the urgent data Option – One option currently defined, maximum TCP segmen ...
... Code bits – Control functions, such as setup and termination of a session Window – Number of octets that the sender will accept Checksum – Calculated checksum of the header and data fields Urgent pointer – Indicates the end of the urgent data Option – One option currently defined, maximum TCP segmen ...
What is TCP Connection Forwarding? Why should I perform TCP
... Why should I perform TCP Connection Forwarding in my network? TCP Connection Forwarding is designed to address common deployment scenarios: --> Transparent deployments where asymmetric routing conditions exist. An asymmetric route is where the path from client to server is different than the return ...
... Why should I perform TCP Connection Forwarding in my network? TCP Connection Forwarding is designed to address common deployment scenarios: --> Transparent deployments where asymmetric routing conditions exist. An asymmetric route is where the path from client to server is different than the return ...
An End-to-End Mobility Architecture for the NGI
... • Cerf’s comment from DoD Internet paper: “If a host were to move, its network (and host) addresses would change and this would affect the connection identifiers used by the TCP. This is rather like a problem called "dynamic reconnection" which has plagued network designers since the inception of th ...
... • Cerf’s comment from DoD Internet paper: “If a host were to move, its network (and host) addresses would change and this would affect the connection identifiers used by the TCP. This is rather like a problem called "dynamic reconnection" which has plagued network designers since the inception of th ...
Ch 2: Exploring Control Types and Methods
... NAT allows many clients to share a single public IP address – By also performing PAT (Port Address ...
... NAT allows many clients to share a single public IP address – By also performing PAT (Port Address ...
CS335 Sample Questions for Exam #2
... 5.) If a datagram is fragmented on the first hop on route to its destination, will the destination host necessarily know that the packet was fragmented? Answer: Yes, because the packet will remain fragmented until it arrives at the final destination. 6.) Is there a maximum number of routers that a p ...
... 5.) If a datagram is fragmented on the first hop on route to its destination, will the destination host necessarily know that the packet was fragmented? Answer: Yes, because the packet will remain fragmented until it arrives at the final destination. 6.) Is there a maximum number of routers that a p ...
ppt - Carnegie Mellon School of Computer Science
... » Solve the problem at the transport layer » Could fix TCP so it works well with multiple simultaneous connections – More difficult to deploy ...
... » Solve the problem at the transport layer » Could fix TCP so it works well with multiple simultaneous connections – More difficult to deploy ...
Chapter3transport
... ACK: segment received (a good thing!), network not congested, so increase sending rate lost segment: assume loss due to congested network, so decrease sending rate ...
... ACK: segment received (a good thing!), network not congested, so increase sending rate lost segment: assume loss due to congested network, so decrease sending rate ...
answers - Princeton CS
... is limited by the RWIN/RTT, where RTT is the round-trip time between the host and the Web server. The home user can improve performance by changing the maximum TCP receiver window (e.g., from 16 KB to 64 KB). Also, most Web transfers are short (e.g., fewer than 10 packets long). For these transfers, ...
... is limited by the RWIN/RTT, where RTT is the round-trip time between the host and the Web server. The home user can improve performance by changing the maximum TCP receiver window (e.g., from 16 KB to 64 KB). Also, most Web transfers are short (e.g., fewer than 10 packets long). For these transfers, ...