COMP211_Topic5_Network
... each packet carries VC identifier (not destination host address) every router on source-dest path maintains “state” for ...
... each packet carries VC identifier (not destination host address) every router on source-dest path maintains “state” for ...
Building a high-performance key
... Exposing the low level packet data to user space directly, ...
... Exposing the low level packet data to user space directly, ...
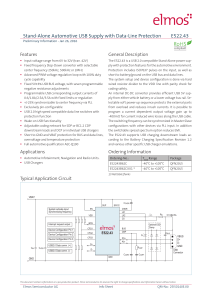
Stand-Alone Automotive USB Supply with Data
... The E522.43 is a USB 2.0 compatible Stand-Alone power supply with protection features for the automotive environment. Protection includes ISO7637 pulses on the input, as well as short to battery/ground on the USB bus and data lines. The system setup and device configuration is done via hard wired re ...
... The E522.43 is a USB 2.0 compatible Stand-Alone power supply with protection features for the automotive environment. Protection includes ISO7637 pulses on the input, as well as short to battery/ground on the USB bus and data lines. The system setup and device configuration is done via hard wired re ...
Waspmote 802.15.4
... 9.2. Searching specific nodes......................................................................................................................................................... 27 9.3. Node discovery to a specific node ........................................................................... ...
... 9.2. Searching specific nodes......................................................................................................................................................... 27 9.3. Node discovery to a specific node ........................................................................... ...
files.aas.org
... The reason for TCP’s sensitivity to packet loss is that the slow-start and congestion avoidance algorithms that were added to TCP to prevent congestion collapse of the Internet – Packet loss is seen by TCP’s congestion control algorithms as evidence of congestion, so they activate to slow down and p ...
... The reason for TCP’s sensitivity to packet loss is that the slow-start and congestion avoidance algorithms that were added to TCP to prevent congestion collapse of the Internet – Packet loss is seen by TCP’s congestion control algorithms as evidence of congestion, so they activate to slow down and p ...
bca501 : core – 18 : computer networks
... hooked onto the next outgoing data frame is called a) piggybacking b) cyclic redundancy check c) fletcher’s checksum d) none of the mentioned Answer: a. 34. Transport layer aggregates data from different applications into a single stream before passing it to a) network layer b) data link layer c) ap ...
... hooked onto the next outgoing data frame is called a) piggybacking b) cyclic redundancy check c) fletcher’s checksum d) none of the mentioned Answer: a. 34. Transport layer aggregates data from different applications into a single stream before passing it to a) network layer b) data link layer c) ap ...
Analysing the performance of the OpenFlow
... (host-to-host) communication. (4): Application layer offers the users with the interface to communication and gives a way for applications to have access to networked services. SDN architecture was defined in three layers. The application layer links business needs to a control layer, which maintain ...
... (host-to-host) communication. (4): Application layer offers the users with the interface to communication and gives a way for applications to have access to networked services. SDN architecture was defined in three layers. The application layer links business needs to a control layer, which maintain ...
RSE-CH4g - wmmhicks.com
... Routers may have different types of interfaces (Ethernet, serial, ATM, etc.) while multilayer switches will only have Ethernet interfaces. While routers can be used to segment LAN devices, their major use is as WAN devices. Each devices does have its own advantages. Routers are: The backbo ...
... Routers may have different types of interfaces (Ethernet, serial, ATM, etc.) while multilayer switches will only have Ethernet interfaces. While routers can be used to segment LAN devices, their major use is as WAN devices. Each devices does have its own advantages. Routers are: The backbo ...
IEEE 802.11
... • Wireless link characteristics: media is error prone and the bit error rate (BER) is very high compared to the BER of wired networks. • Carrier Sensing/collision detection is difficult in wireless networks because a station is incapable of listening to its own transmissions in order to detect a ...
... • Wireless link characteristics: media is error prone and the bit error rate (BER) is very high compared to the BER of wired networks. • Carrier Sensing/collision detection is difficult in wireless networks because a station is incapable of listening to its own transmissions in order to detect a ...
IEEE 802.11 WLAN
... The AP will send a Beacon to notify the station that it has buffered frames to that station. The station don’t have to wakeup every Beacon (in the IBSS the station MUST wakeup in Beacon receive) When the station wakes up it sends power save poll frame to the AP. The AP than will send to the station ...
... The AP will send a Beacon to notify the station that it has buffered frames to that station. The station don’t have to wakeup every Beacon (in the IBSS the station MUST wakeup in Beacon receive) When the station wakes up it sends power save poll frame to the AP. The AP than will send to the station ...
Document
... Constructs a layered structure (Onion) and sends it through the network to establish the Virtual Circuit (same as ATM Virtual Circuit Establishment with VPI/VCI). Onion passes through the entire path to the responder proxy => all involved ORs are initialized with relevant information to encrypt/ dec ...
... Constructs a layered structure (Onion) and sends it through the network to establish the Virtual Circuit (same as ATM Virtual Circuit Establishment with VPI/VCI). Onion passes through the entire path to the responder proxy => all involved ORs are initialized with relevant information to encrypt/ dec ...
a destination IP address
... The figure shown is an example of a layer 3 network. The components that make up the layer 3 network are shown. The source host computer has an installed network interface card (NIC), an assigned IP address and subnet mask. The subnet mask is used to determine if the data is to stay in the LAN or i ...
... The figure shown is an example of a layer 3 network. The components that make up the layer 3 network are shown. The source host computer has an installed network interface card (NIC), an assigned IP address and subnet mask. The subnet mask is used to determine if the data is to stay in the LAN or i ...
PowerPoint-Präsentation
... Both companies work very close together and ASML appreciates support provided by Mechanical Engineering in the development of new products, for example its process engineering input ...
... Both companies work very close together and ASML appreciates support provided by Mechanical Engineering in the development of new products, for example its process engineering input ...
jxta15
... group is a collection of peers that have agreed upon a common set of rules to publish, share and access their data, and ...
... group is a collection of peers that have agreed upon a common set of rules to publish, share and access their data, and ...
Document
... – Synchronization: Because this is a transition at the middle of each bit period. – Error Detection: The absence of the expected transition can be used to detect errors. Disadvantages of Manchester and Differential Manchester Encoding: – High Signaling Rate: At least one transition per bit time is n ...
... – Synchronization: Because this is a transition at the middle of each bit period. – Error Detection: The absence of the expected transition can be used to detect errors. Disadvantages of Manchester and Differential Manchester Encoding: – High Signaling Rate: At least one transition per bit time is n ...
Chapter 5: The Data Link Layer
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
Chapter 1 - Introduction
... • An even parity mechanism can only handle errors where an odd number of bits are changed – If one of the nine bits (including the parity bit) is changed during transmission, the receiver will declare that the incoming byte is invalid – However, if a burst error occurs in which two, four, six, or ei ...
... • An even parity mechanism can only handle errors where an odd number of bits are changed – If one of the nine bits (including the parity bit) is changed during transmission, the receiver will declare that the incoming byte is invalid – However, if a burst error occurs in which two, four, six, or ei ...