ppt
... transport protocol for “best effort” service, UDP segments may be: lost delivered out-of-order connectionless: no sender-receiver handshaking each UDP segment handled independently ...
... transport protocol for “best effort” service, UDP segments may be: lost delivered out-of-order connectionless: no sender-receiver handshaking each UDP segment handled independently ...
D-Link DXS-3600 Series Sales Guide
... OSPF is more popular than IS-IS, OSPF is more suitable for mid-to-large size network DXS-3600 series is not intend to get MEF 9/14 For projects required, please contact local PM or RM DXS-3600 series already supported IPv6 ACL/QoS from R1.00 ...
... OSPF is more popular than IS-IS, OSPF is more suitable for mid-to-large size network DXS-3600 series is not intend to get MEF 9/14 For projects required, please contact local PM or RM DXS-3600 series already supported IPv6 ACL/QoS from R1.00 ...
Intro_part2
... Data Transfer Through the Network 4/6 •Packet-Switching Data sent through network in discrete chunks Each end-to-end data stream divided into packets Users’ packets share network resources Each packet uses full link bandwidth Resource contention ...
... Data Transfer Through the Network 4/6 •Packet-Switching Data sent through network in discrete chunks Each end-to-end data stream divided into packets Users’ packets share network resources Each packet uses full link bandwidth Resource contention ...
Lecture 03
... different machines are called peer processes. A process on one machine interacts with a process on another machine across a peer interface (HTTP on client and server are peer processes) Layer-n peer processes communicate by ...
... different machines are called peer processes. A process on one machine interacts with a process on another machine across a peer interface (HTTP on client and server are peer processes) Layer-n peer processes communicate by ...
`Performance control of high-capacity IP networks for
... close to 100% and the delay kept at an acceptable level. Simulation Of The Network In Figure 2 With Traffic Controls The traffic controls as proposed in section Proposed traffic control and encoding were implemented in hosts and routers. The SourceHost1 queue rejects new packet arrivals when there a ...
... close to 100% and the delay kept at an acceptable level. Simulation Of The Network In Figure 2 With Traffic Controls The traffic controls as proposed in section Proposed traffic control and encoding were implemented in hosts and routers. The SourceHost1 queue rejects new packet arrivals when there a ...
PH3135-90S Radar Pulsed Power Transistor M/A-COM Products
... is considering for development. Performance is based on target specifications, simulated results, • Europe Tel: 44.1908.574.200 / Fax: 44.1908.574.300 and/or prototype measurements. Commitment to develop is not guaranteed. • Asia/Pacific Tel: 81.44.844.8296 / Fax: 81.44.844.8298 PRELIMINARY: Data Sh ...
... is considering for development. Performance is based on target specifications, simulated results, • Europe Tel: 44.1908.574.200 / Fax: 44.1908.574.300 and/or prototype measurements. Commitment to develop is not guaranteed. • Asia/Pacific Tel: 81.44.844.8296 / Fax: 81.44.844.8298 PRELIMINARY: Data Sh ...
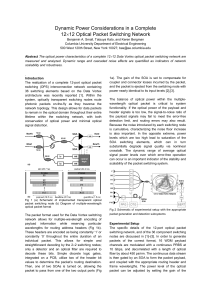
Dynamic Power Considerations in a Complete 12×12 Optical Packet
... A series of experiments to investigate the optical power levels within the 12-port switching network are performed. First, the injected packets’ optical power spectrum was compared to that of the ejected packets, in order to confirm the almost perfect transparency of the implemented OPS architecture ...
... A series of experiments to investigate the optical power levels within the 12-port switching network are performed. First, the injected packets’ optical power spectrum was compared to that of the ejected packets, in order to confirm the almost perfect transparency of the implemented OPS architecture ...
IEEE 802.11 architecture
... Integrated; A single Access-Point in a standalone network Wired; Using cable to interconnect the Access-Points Wireless; Using wireless to interconnect the Access-Points ...
... Integrated; A single Access-Point in a standalone network Wired; Using cable to interconnect the Access-Points Wireless; Using wireless to interconnect the Access-Points ...
SIS-DTN_Green Book v0.6-v0.7 changes
... Custom forwarding (application-layer forwarding) CCSDS Space Packets as an internetworking packet format CCSDS File Delivery Protocol (CFDP) Internet Protocol (IP) The Bundle Protocol from Delay / Disruption Tolerant Networking (DTN) Custom forwarding, while sometimes expedient, is not a g ...
... Custom forwarding (application-layer forwarding) CCSDS Space Packets as an internetworking packet format CCSDS File Delivery Protocol (CFDP) Internet Protocol (IP) The Bundle Protocol from Delay / Disruption Tolerant Networking (DTN) Custom forwarding, while sometimes expedient, is not a g ...
ICN lecture6_ Digital-Digital & Analog
... significant factor here is to remove any DC bias because coupling will severely attenuate this component of the signal. ...
... significant factor here is to remove any DC bias because coupling will severely attenuate this component of the signal. ...
Appendix B - Roaming
... lan cable to your office switch. The server wants to send a stream of data to a wireless client (let's say a laptop) which is wirelessly connected to an access point also connected to this same switch. The transmission of data from server to client would go something like this: Server wants to send ...
... lan cable to your office switch. The server wants to send a stream of data to a wireless client (let's say a laptop) which is wirelessly connected to an access point also connected to this same switch. The transmission of data from server to client would go something like this: Server wants to send ...
Commonly used techniques to “solve” reliability
... as perceived by a user. Terms, such as “better”, “worse”, “high”, “medium”, “low”, “good”, “fair”, “poor”, are typically used, but these are subjective and cannot therefore be translated precisely into network level parameters that can subsequently be designed for by network planners. • The end effe ...
... as perceived by a user. Terms, such as “better”, “worse”, “high”, “medium”, “low”, “good”, “fair”, “poor”, are typically used, but these are subjective and cannot therefore be translated precisely into network level parameters that can subsequently be designed for by network planners. • The end effe ...
The Internet Underwater: An IP-compatible Protocol Stack for Commercial Undersea Modems
... network (WSN) and very long propagation delays of delaytolerant networks (DTN) [3]. The main challenges from a protocol perspective lie in the following aspects: • The long propagation delays of underwater networks [1] require protocols to be delay-tolerant. However, TCP/IP is not designed to be suc ...
... network (WSN) and very long propagation delays of delaytolerant networks (DTN) [3]. The main challenges from a protocol perspective lie in the following aspects: • The long propagation delays of underwater networks [1] require protocols to be delay-tolerant. However, TCP/IP is not designed to be suc ...
Wireless Communications and Networks
... Channel Capacity – the maximum rate at which data can be transmitted over a given communication path, or channel, under ...
... Channel Capacity – the maximum rate at which data can be transmitted over a given communication path, or channel, under ...
UNIT 3.ppt - E
... Remember, the network layer must be able to operate on top of any data-link layer technology (Ethernet, Fast Ethernet, ATM etc.). All these technologies can handle a different packet length. The network layer must be able to fragment transport layer PDUs into smaller units so that they can be transf ...
... Remember, the network layer must be able to operate on top of any data-link layer technology (Ethernet, Fast Ethernet, ATM etc.). All these technologies can handle a different packet length. The network layer must be able to fragment transport layer PDUs into smaller units so that they can be transf ...
PPT - web.iiit.ac.in
... frame based on MAC dest address – When frame is to be forwarded on segment, uses CSMA/CD to access segment • Transparent – Hosts are unaware of presence of switches • Plug-and-play, self-learning – Switches do not need to be configured • Filter data frames – Create separate collision domains • Provi ...
... frame based on MAC dest address – When frame is to be forwarded on segment, uses CSMA/CD to access segment • Transparent – Hosts are unaware of presence of switches • Plug-and-play, self-learning – Switches do not need to be configured • Filter data frames – Create separate collision domains • Provi ...
Part I: Introduction
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...