MPLS networking at PSP Co Multi
... • Needed a single infrastructure that supports multitude of applications in a secure manner • Provide a highly scalable mechanism that was topology driven rather than flow driven • Load balance traffic to utilize network bandwidth efficiently • Allow core routers/networking devices to switch packets ...
... • Needed a single infrastructure that supports multitude of applications in a secure manner • Provide a highly scalable mechanism that was topology driven rather than flow driven • Load balance traffic to utilize network bandwidth efficiently • Allow core routers/networking devices to switch packets ...
Mobility in the Internet
... • Survivability is the capability of a network to maintain existing services in the face of failures • Dynamic routing restores the traffic (upon a failure) based on the convergence time of the protocol • For a packet network carrying mission critical or high priority data (like MPLS network), we ma ...
... • Survivability is the capability of a network to maintain existing services in the face of failures • Dynamic routing restores the traffic (upon a failure) based on the convergence time of the protocol • For a packet network carrying mission critical or high priority data (like MPLS network), we ma ...
Click
... – If not refreshed every 30 seconds, the soft state ages out and is deleted. – This allows RSVP to adjust and alter the path between RSVP end systems to recover from route changes – If also prevents router resources from being tied up due to receivers that quietly vanish. – This solves the problem i ...
... – If not refreshed every 30 seconds, the soft state ages out and is deleted. – This allows RSVP to adjust and alter the path between RSVP end systems to recover from route changes – If also prevents router resources from being tied up due to receivers that quietly vanish. – This solves the problem i ...
Error analysis for the interpolation of monthly rainfall used in the
... Normalisation parameters have been computed for monthly rainfall. The steps required to compute these values are as follows: 1. The normalisation power is computed for each station using Maximum Likelihood. An individual value is computed for each month. (January, February etc). A station must have ...
... Normalisation parameters have been computed for monthly rainfall. The steps required to compute these values are as follows: 1. The normalisation power is computed for each station using Maximum Likelihood. An individual value is computed for each month. (January, February etc). A station must have ...
Lecture 2
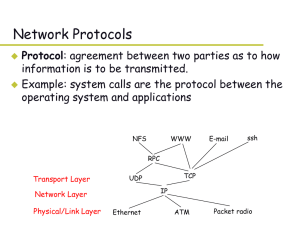
... • Congestion Control: The server should send data as fast as possible, but not too fast • TCP provides these features (services), while UDP does not 3. Network layer (could be called the routing layer, but it isn’t) • The packets must find their way through the network. • Each packet has the IP addr ...
... • Congestion Control: The server should send data as fast as possible, but not too fast • TCP provides these features (services), while UDP does not 3. Network layer (could be called the routing layer, but it isn’t) • The packets must find their way through the network. • Each packet has the IP addr ...
Bridging
... To improve performance on overburdened shared media LANs, several proven design strategies can be followed: Segmentation : Fewer workstations per segment results in less contention for the shared bandwidth. Some type of internetworking device (e.g. bridge or router) is required to link the LAN s ...
... To improve performance on overburdened shared media LANs, several proven design strategies can be followed: Segmentation : Fewer workstations per segment results in less contention for the shared bandwidth. Some type of internetworking device (e.g. bridge or router) is required to link the LAN s ...
Chapter 5
... hub, then the independent collision domains become one collision domain. If depts use different Ethernet technologies, may not be able to interconnect them Each Ethernet technology has restrictions on ...
... hub, then the independent collision domains become one collision domain. If depts use different Ethernet technologies, may not be able to interconnect them Each Ethernet technology has restrictions on ...
Vnet/IP REAL-TIME PLANT
... processing is executed according to the priority order. This priority assignment is applicable to network devices such as switching hubs. In order to recover quickly from transient communication errors, the UDP/IP stack is adopted. Because the UDP/IP stack has a protocol for quick error response and ...
... processing is executed according to the priority order. This priority assignment is applicable to network devices such as switching hubs. In order to recover quickly from transient communication errors, the UDP/IP stack is adopted. Because the UDP/IP stack has a protocol for quick error response and ...
Transport Protocols
... checksum segments if so configured by application connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... checksum segments if so configured by application connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
DVoIP: DYNAMIC VOICE-OVER-IP TRANSFORMATIONS FOR QUALITY OF SERVICE IN
... library is necessary for two reasons. First, it is important to be able to decode audio in the format used by a VoIP application, and second, we need a collection of low-bitrate codecs to be able to transmit audio over the constrained link. To transcode a VoIP packet, first we decode all the audio i ...
... library is necessary for two reasons. First, it is important to be able to decode audio in the format used by a VoIP application, and second, we need a collection of low-bitrate codecs to be able to transmit audio over the constrained link. To transcode a VoIP packet, first we decode all the audio i ...
Institutionen för systemteknik
... A previous thesis written at the department had shown the feasibility of implementing such a router with an on-chip network (SoCBUS) in a custom ASIC. It was however obvious from the start that limitations (e.g. speed and available on-chip memory) in the hardware used in this project would result in ...
... A previous thesis written at the department had shown the feasibility of implementing such a router with an on-chip network (SoCBUS) in a custom ASIC. It was however obvious from the start that limitations (e.g. speed and available on-chip memory) in the hardware used in this project would result in ...
A Phase Interpolator CDR with Low-Voltage CML Circuits ..........Li
... The latch has two levels, Vin_n and Vin_p as the first level, and CLK+ and CLK- as the second level, as shown in Fig. 9. The track and latch modes are determined by CLK+ and CLK- to a second differential pair, M2 and M3. When CLK+ is high and CLK- is low, Ibias flows through M4 and M5. If Vin_n and ...
... The latch has two levels, Vin_n and Vin_p as the first level, and CLK+ and CLK- as the second level, as shown in Fig. 9. The track and latch modes are determined by CLK+ and CLK- to a second differential pair, M2 and M3. When CLK+ is high and CLK- is low, Ibias flows through M4 and M5. If Vin_n and ...
SCADA in electrical power delivery
... ◦ Substation control centre communication (IEC 60870-5101/104) ◦ Communication with protection equipment (IEC 60870-5-103) ◦ IEC 62351 intends to implement security (end-to-end encryption; vendors reluctant to implement due to complexity) ...
... ◦ Substation control centre communication (IEC 60870-5101/104) ◦ Communication with protection equipment (IEC 60870-5-103) ◦ IEC 62351 intends to implement security (end-to-end encryption; vendors reluctant to implement due to complexity) ...
What Goes Into a Data Center?
... • Given a switch ASIC, build a switch with more ports by combing ASICs – Silicon fabrication costs drive ASIC price – Market size drives packaged switch price • General rule of thumb: cost of a link, from least to greatest: ...
... • Given a switch ASIC, build a switch with more ports by combing ASICs – Silicon fabrication costs drive ASIC price – Market size drives packaged switch price • General rule of thumb: cost of a link, from least to greatest: ...
An Introduction to TCP/IP - Oakton Community College
... The Internet Protocol (IP) is responsible for ensuring that data is transferred between two addresses without being corrupted. For manageability, the data is usually split into multiple pieces or packets each with its own error detection bytes in the control section or header of the packet. The remo ...
... The Internet Protocol (IP) is responsible for ensuring that data is transferred between two addresses without being corrupted. For manageability, the data is usually split into multiple pieces or packets each with its own error detection bytes in the control section or header of the packet. The remo ...
Investigating Two Different Approaches for Encrypted Traffic
... packet analyzer that uses the entire packet with the payload to label the traffic. To label SSH traffic, the tool searches for the handshake for SSH connection where the protocol version and the cryptographic techniques used are exchanged in plaintext. Moreover, for both systems, flow is defined as ...
... packet analyzer that uses the entire packet with the payload to label the traffic. To label SSH traffic, the tool searches for the handshake for SSH connection where the protocol version and the cryptographic techniques used are exchanged in plaintext. Moreover, for both systems, flow is defined as ...
3rd Edition: Chapter 3
... segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
SDN security 2 - FSU Computer Science
... • Find the shortest path passing through R4 – Shortest path between S and R4 – Shortest path between R4 and E ...
... • Find the shortest path passing through R4 – Shortest path between S and R4 – Shortest path between R4 and E ...
Selling an Idea or a Product
... Epoch # – uniquely identifies which set of sequence numbers are being used. ...
... Epoch # – uniquely identifies which set of sequence numbers are being used. ...
AD53500 英文数据手册DataSheet 下载
... part nonfunctional. Finally, the AD53500 may appear to function normally for small output steps (less than 3 V or so) if one or both of these caps is absent, but it may exhibit excessive rise or fall times for steps of larger amplitude. The AD53500 does not require special power-supply sequencing. H ...
... part nonfunctional. Finally, the AD53500 may appear to function normally for small output steps (less than 3 V or so) if one or both of these caps is absent, but it may exhibit excessive rise or fall times for steps of larger amplitude. The AD53500 does not require special power-supply sequencing. H ...
of the packet
... • Unreliable means simply that IP does not have the capability to manage, and recover from, undelivered or corrupt packets. ...
... • Unreliable means simply that IP does not have the capability to manage, and recover from, undelivered or corrupt packets. ...