Solution
... In the following, use either a direct proof (by giving values for c and n0 in the definition of big-Oh notation) or cite one of the rules given in the book or in the lecture slides. (a) Show that if f(n) is O(g(n)) and d(n) is O(h(n)), then f(n)+d(n) is O(g(n)+ h(n)). Solution Recall the de_nition o ...
... In the following, use either a direct proof (by giving values for c and n0 in the definition of big-Oh notation) or cite one of the rules given in the book or in the lecture slides. (a) Show that if f(n) is O(g(n)) and d(n) is O(h(n)), then f(n)+d(n) is O(g(n)+ h(n)). Solution Recall the de_nition o ...
Sept 2 - Joshua Stough
... • After-hour access into Adams for non-CMC students Need to activate your card for the card reader - do the following: fill out the list being circulated. • When the paper work is done, you will be asked to go to Story House (building immediately south of Collins Dining Hall) to get your card activa ...
... • After-hour access into Adams for non-CMC students Need to activate your card for the card reader - do the following: fill out the list being circulated. • When the paper work is done, you will be asked to go to Story House (building immediately south of Collins Dining Hall) to get your card activa ...
Document
... • Input: list L of n numbers • Problem: Sort list L • Algorithm MergeSort(L): If L has at most two elements then sort them by comparison and exit; Else: – Split L into two lists prefix and suffix, each of size n/2 – Sort, by merging, the prefix and the suffix separately: MergeSort(prefix) and MergeS ...
... • Input: list L of n numbers • Problem: Sort list L • Algorithm MergeSort(L): If L has at most two elements then sort them by comparison and exit; Else: – Split L into two lists prefix and suffix, each of size n/2 – Sort, by merging, the prefix and the suffix separately: MergeSort(prefix) and MergeS ...
PDF - 4up
... that stores other objects, referred to as data or elements. So some people refer a data structure as a container object or a collection object. To define a data structure is essentially to declare a class. The class for a data structure should use data fields to store data and provide methods to sup ...
... that stores other objects, referred to as data or elements. So some people refer a data structure as a container object or a collection object. To define a data structure is essentially to declare a class. The class for a data structure should use data fields to store data and provide methods to sup ...
LEC01 - aiub study guide
... Best case: elements already sorted, tj=1, running time = n-1, i.e., linear time. Worst case: elements are sorted in inverse order, tj=j-1, running time = (n2-n)/2, i.e., quadratic time. Average case: tj=j/2, running time = (n2+n-2)/4, i.e., quadratic time. ...
... Best case: elements already sorted, tj=1, running time = n-1, i.e., linear time. Worst case: elements are sorted in inverse order, tj=j-1, running time = (n2-n)/2, i.e., quadratic time. Average case: tj=j/2, running time = (n2+n-2)/4, i.e., quadratic time. ...
Answers Exercises week 2
... The best case is when the vector is sorted and the swap never executes. We then have T (n) = N c1 + Si c2 + Sj c3 . but unfortunately the complexity remains quadratic, for the same reason as before. T (n) executes in the best case also in Θ(n2 ). (ii) The algorithm is Ω(n2 ) and O(n2 ) which is acco ...
... The best case is when the vector is sorted and the swap never executes. We then have T (n) = N c1 + Si c2 + Sj c3 . but unfortunately the complexity remains quadratic, for the same reason as before. T (n) executes in the best case also in Θ(n2 ). (ii) The algorithm is Ω(n2 ) and O(n2 ) which is acco ...
Blame Trees - Edward Z. Yang
... modifications to old versions of document, a confluently persistent structure additionally supports a merge operation. Any two documents can be merged, which means that the version dependencies can form a directed acyclic graph (DAG). Our paper presents an implementation of this data structure which ...
... modifications to old versions of document, a confluently persistent structure additionally supports a merge operation. Any two documents can be merged, which means that the version dependencies can form a directed acyclic graph (DAG). Our paper presents an implementation of this data structure which ...
CS440 - Assignment 3
... the case where each tuple of R joins with a few tuples of S and the case in which each tuple of R joins with many tuples of S. (1 point) The memory requirement in sort-merge join with two-pass multi-way merge sort is B(R) ≤ M 2 and B(S) ≤ M 2 . On the other hand, the memory requirement in sort-merge ...
... the case where each tuple of R joins with a few tuples of S and the case in which each tuple of R joins with many tuples of S. (1 point) The memory requirement in sort-merge join with two-pass multi-way merge sort is B(R) ≤ M 2 and B(S) ≤ M 2 . On the other hand, the memory requirement in sort-merge ...
Slides - Computer Science, Columbia University
... How do we add a node to the end of the list? Follow pointers to last node, allocate new node, set last node’s next to new node. How do we add in the middle of the list? Set previous node’s next to new node, set new node’s next to next node. How do we delete a node? ...
... How do we add a node to the end of the list? Follow pointers to last node, allocate new node, set last node’s next to new node. How do we add in the middle of the list? Set previous node’s next to new node, set new node’s next to next node. How do we delete a node? ...
Split-Ordered Lists: Lock-Free Extensible Hash Tables
... The key to success lies in the correct ordering of the list items. To simplify, the authors assume a modulo 2i hash function and a hash table size of 2i . For example, given a table of size 4, this means that key 13 will be in bucket 13 modulo 4 = 1. Note that this is equivalent to saying that the i ...
... The key to success lies in the correct ordering of the list items. To simplify, the authors assume a modulo 2i hash function and a hash table size of 2i . For example, given a table of size 4, this means that key 13 will be in bucket 13 modulo 4 = 1. Note that this is equivalent to saying that the i ...
Recursive Splitting Problem Consider the problem where an
... as possible. Patterns like Agent & Repository or Mutual Exclusion can help in resolving such conflicts. ...
... as possible. Patterns like Agent & Repository or Mutual Exclusion can help in resolving such conflicts. ...
Problem Set 2 Solutions - Massachusetts Institute of Technology
... because of other elements being missorted. Similarly, some elements may appear entirely out of place, but be good because of other misplaced elements. A key element of the proof is showing that a badly sorted list has a lot of bad elements. Lemma 5 If the list A is not 90% sorted, then at least 10% ...
... because of other elements being missorted. Similarly, some elements may appear entirely out of place, but be good because of other misplaced elements. A key element of the proof is showing that a badly sorted list has a lot of bad elements. Lemma 5 If the list A is not 90% sorted, then at least 10% ...
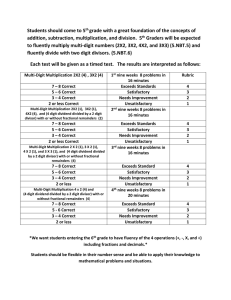
Students should come to 5
... Students should come to 5th grade with a great foundation of the concepts of addition, subtraction, multiplication, and division. 5th Graders will be expected to fluently multiply multi-digit numbers (2X2, 3X2, 4X2, and 3X3) (5.NBT.5) and fluently divide with two digit divisors. (5.NBT.6) Each test ...
... Students should come to 5th grade with a great foundation of the concepts of addition, subtraction, multiplication, and division. 5th Graders will be expected to fluently multiply multi-digit numbers (2X2, 3X2, 4X2, and 3X3) (5.NBT.5) and fluently divide with two digit divisors. (5.NBT.6) Each test ...
2-04-2005
... Application of Searching to 3n+1 Write a function that takes a positive integer as an input and returns the number of steps it takes to get to 1. If it doesn’t go to 1 (!), the function will never return. Then create an array of one million random integers, and a parallel array of the number of ste ...
... Application of Searching to 3n+1 Write a function that takes a positive integer as an input and returns the number of steps it takes to get to 1. If it doesn’t go to 1 (!), the function will never return. Then create an array of one million random integers, and a parallel array of the number of ste ...
Program revision 2
... • An array is an ordered collection, or numbered list, of values. All of the values in an array must be of the same type. The type of the array is the type of the values it holds, followed by the characters []. An index is used to refer to individual values in the array. If we have N values, we thin ...
... • An array is an ordered collection, or numbered list, of values. All of the values in an array must be of the same type. The type of the array is the type of the values it holds, followed by the characters []. An index is used to refer to individual values in the array. If we have N values, we thin ...
ppt - Dave Reed
... a more interesting recursive algorithm is credited to Euclid (3rd cent., BC) to find the Greatest Common Divisor (GCD) of numbers a and b (a ≥ b) • if a % b == 0, the GCD = b • otherwise, GCD of a & b = GCD of b and (a % b) note: defines GCD of two numbers in terms of GCD of smaller numbers int GCD( ...
... a more interesting recursive algorithm is credited to Euclid (3rd cent., BC) to find the Greatest Common Divisor (GCD) of numbers a and b (a ≥ b) • if a % b == 0, the GCD = b • otherwise, GCD of a & b = GCD of b and (a % b) note: defines GCD of two numbers in terms of GCD of smaller numbers int GCD( ...
1 Divide and Conquer with Reduce
... car in mind. Then, the mock-up can be used to help build the actual final car, which probably involve a number of refining iterations that add in more and more details. One could even imagine building multiple mock-ups each smaller and simpler than the previous to help build the final car. The contr ...
... car in mind. Then, the mock-up can be used to help build the actual final car, which probably involve a number of refining iterations that add in more and more details. One could even imagine building multiple mock-ups each smaller and simpler than the previous to help build the final car. The contr ...
Day_2_prob
... Let’s write a program MAXSORT to sort an array A of size strings. MAXSORT works by finding the index of the maximum element in the array from A[0] through A[size-1] and swapping it with the current last location. The current last location starts at size - 1 and size is decremented at each iteration ...
... Let’s write a program MAXSORT to sort an array A of size strings. MAXSORT works by finding the index of the maximum element in the array from A[0] through A[size-1] and swapping it with the current last location. The current last location starts at size - 1 and size is decremented at each iteration ...
Heap Sort
... a dictionary, if it can be arranged such that the key is also the index to the array that stores the entries, searching and inserting items would be very fast ► Example: empdata[1000] index = employee ID number ► Search ...
... a dictionary, if it can be arranged such that the key is also the index to the array that stores the entries, searching and inserting items would be very fast ► Example: empdata[1000] index = employee ID number ► Search ...
Dictionary ADT Dictionary ADTs
... in which usual operations may be used and there exists an order relationship between keys Useful implementation for few insertions / removals, but many searches ...
... in which usual operations may be used and there exists an order relationship between keys Useful implementation for few insertions / removals, but many searches ...
Introduction to Algorithms November 4, 2005
... different form, primarily to help see the connection between the two data structures. The data structure consists of a set of linked lists, just as a typical skip list. The lists all begin with . The SEARCH algorithm remains exactly as in the regular skip-list data structure. Each node in a linked l ...
... different form, primarily to help see the connection between the two data structures. The data structure consists of a set of linked lists, just as a typical skip list. The lists all begin with . The SEARCH algorithm remains exactly as in the regular skip-list data structure. Each node in a linked l ...
CS173: Discrete Math
... Time complexity of binary search • For simplicity, assume n=2k,k=log2n • At each iteration, 2 comparisons are used • For example, 2 comparisons are used when the list has 2k-1 elements, 2 comparisons are used when the list has 2k-2, …, 2 comparisons are used when the list has 21 elements • 1 compar ...
... Time complexity of binary search • For simplicity, assume n=2k,k=log2n • At each iteration, 2 comparisons are used • For example, 2 comparisons are used when the list has 2k-1 elements, 2 comparisons are used when the list has 2k-2, …, 2 comparisons are used when the list has 21 elements • 1 compar ...
slides - faculty.ucmerced.edu
... Time complexity of binary search • For simplicity, assume n=2k,k=log2n • At each iteration, 2 comparisons are used • For example, 2 comparisons are used when the list has 2k-1 elements, 2 comparisons are used when the list has 2k-2, …, 2 comparisons are used when the list has 21 elements • 1 compar ...
... Time complexity of binary search • For simplicity, assume n=2k,k=log2n • At each iteration, 2 comparisons are used • For example, 2 comparisons are used when the list has 2k-1 elements, 2 comparisons are used when the list has 2k-2, …, 2 comparisons are used when the list has 21 elements • 1 compar ...