Ubee DDW36C Advanced Wireless Gateway
... not be reproduced, distributed, or altered in any fashion by any entity (either internal or external to Ubee), except in accordance with applicable agreements, contracts, or licensing, without the express written consent of Ubee and the business management owner of the material. Ubee Interactive con ...
... not be reproduced, distributed, or altered in any fashion by any entity (either internal or external to Ubee), except in accordance with applicable agreements, contracts, or licensing, without the express written consent of Ubee and the business management owner of the material. Ubee Interactive con ...
245U-E (English)
... personnel with adequate knowledge of safety design considerations. ELPRO radio products are used on unprotected license-free radio bands with radio noise and interference. The products are designed to operate in the presence of noise and interference. However, in an extreme cases radio noise and int ...
... personnel with adequate knowledge of safety design considerations. ELPRO radio products are used on unprotected license-free radio bands with radio noise and interference. The products are designed to operate in the presence of noise and interference. However, in an extreme cases radio noise and int ...
VLANs
... Intelligent Switches • For most switches there is not enough capacity in the switching fabric / backplane to support all ports if they become active so the switch forms groups of connections and assigns capacity using time division multiplexing. • This means that the switch no longer guarantees sim ...
... Intelligent Switches • For most switches there is not enough capacity in the switching fabric / backplane to support all ports if they become active so the switch forms groups of connections and assigns capacity using time division multiplexing. • This means that the switch no longer guarantees sim ...
ATM LAN Emulation
... Resolve the ATM address corresponding to a given destination MAC address. Client generates an ARP request and send to LES via Control Direct VCC. BUS forwards unicast frames to all clients before the Data Direct VCC is established. Proxy LECs response ARP requests for known MAC addresses on their se ...
... Resolve the ATM address corresponding to a given destination MAC address. Client generates an ARP request and send to LES via Control Direct VCC. BUS forwards unicast frames to all clients before the Data Direct VCC is established. Proxy LECs response ARP requests for known MAC addresses on their se ...
eigrp
... the following major categories: –Compatibility mode – IGRP and EIGRP are compatible with each other. –Metric calculation – EIGRP scales the metric of IGRP by a factor of 256. That is because EIGRP uses a metric that is 32 bits long, and IGRP uses a 24-bit metric. –Hop count – IGRP has a maximum hop ...
... the following major categories: –Compatibility mode – IGRP and EIGRP are compatible with each other. –Metric calculation – EIGRP scales the metric of IGRP by a factor of 256. That is because EIGRP uses a metric that is 32 bits long, and IGRP uses a 24-bit metric. –Hop count – IGRP has a maximum hop ...
6.5.2 Subnetting – Dividing Networks into Right Sizes
... Authentication and privacy capabilities - to integrate security ...
... Authentication and privacy capabilities - to integrate security ...
A Model for Naming, Addressing, and Routing
... We also know that in Ethernet, Xerox has introduced the concept of factory set addresses [2]. These addresses are 48-bit numbers, and no two controllers in the world may have the same number. Since controllers have their addresses fixed before they are installed on some Ethernet LAN, it is obvious t ...
... We also know that in Ethernet, Xerox has introduced the concept of factory set addresses [2]. These addresses are 48-bit numbers, and no two controllers in the world may have the same number. Since controllers have their addresses fixed before they are installed on some Ethernet LAN, it is obvious t ...
FiOS Gateway USER GUIDE - Frontier Communications
... 2.0b/ STEP 2 - CONNECT YOUR DEVICE TO YOUR GATEWAY If connecting a device using wired Ethernet (preferred for initial setup): • Plug one end of the supplied yellow Ethernet cable into one of the four yellow Ethernet ports in the back of your Gateway. Alternatively, you can use your own Ethernet cabl ...
... 2.0b/ STEP 2 - CONNECT YOUR DEVICE TO YOUR GATEWAY If connecting a device using wired Ethernet (preferred for initial setup): • Plug one end of the supplied yellow Ethernet cable into one of the four yellow Ethernet ports in the back of your Gateway. Alternatively, you can use your own Ethernet cabl ...
Cisco SRW224 24 Port 10/100 + 2
... and up to 7 trunking groups. Or if you prefer, you can use the integrated console port to configure the switch. The non-blocking, wire-speed switching forwards packets as fast as your network can deliver them. All ports have automatic MDI/MDI-X crossover detection. Each port independently and automa ...
... and up to 7 trunking groups. Or if you prefer, you can use the integrated console port to configure the switch. The non-blocking, wire-speed switching forwards packets as fast as your network can deliver them. All ports have automatic MDI/MDI-X crossover detection. Each port independently and automa ...
Chapter5 (IPv4 Address)
... separation of private addresses in a network from the global addresses used in the Internet. A translation table can translate the private addresses, selected from the blocks allocated for this purpose, to global addresses. The translation table also translates the IP addresses as well as the port n ...
... separation of private addresses in a network from the global addresses used in the Internet. A translation table can translate the private addresses, selected from the blocks allocated for this purpose, to global addresses. The translation table also translates the IP addresses as well as the port n ...
IPv6 based NGN
... packet-based network able to provide Telecommunication Services to users and able to make use of multiple broadband, QoS-enabled transport technologies and in which service-related functions are independent of the underlying transportrelated technologies. ...
... packet-based network able to provide Telecommunication Services to users and able to make use of multiple broadband, QoS-enabled transport technologies and in which service-related functions are independent of the underlying transportrelated technologies. ...
CISSP Common Body of Knowledge
... “The Telecommunications and Network Security domain encompasses the structures, techniques, transport protocols, and security measures used to provide integrity, availability, confidentiality, and authentication for transmissions over private and public communication networks.” “The candidate is exp ...
... “The Telecommunications and Network Security domain encompasses the structures, techniques, transport protocols, and security measures used to provide integrity, availability, confidentiality, and authentication for transmissions over private and public communication networks.” “The candidate is exp ...
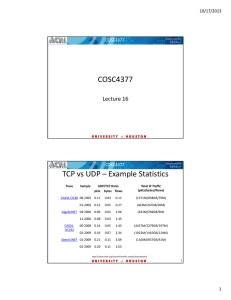
COSC4377 TCP vs UDP – Example Statistics
... – 1) Content availability. More of our customers are opting in to have their sites, content, and applications permanently available "dual‐stacked" (i.e., available over both IPv6 and IPv4). – 2) Availability of IPv6 from access network providers. Over the past year, some of the largest growth ia ...
... – 1) Content availability. More of our customers are opting in to have their sites, content, and applications permanently available "dual‐stacked" (i.e., available over both IPv6 and IPv4). – 2) Availability of IPv6 from access network providers. Over the past year, some of the largest growth ia ...
VPN et IPSec
... Let’s start by examining the word “network” This is perhaps the least difficult term for us to define and understand, since the commonly accepted definition is fairly uncontroversial and generally accepted throughout the industry. A network consists of any number of devices which can communicate thr ...
... Let’s start by examining the word “network” This is perhaps the least difficult term for us to define and understand, since the commonly accepted definition is fairly uncontroversial and generally accepted throughout the industry. A network consists of any number of devices which can communicate thr ...
Repeaters, Switches and Routers
... Routers are most likely to have the most flexibility with regard to interface. They will have multiple LANs and WANs Switches often have configurations that provide for a higher speed uplink port. ...
... Routers are most likely to have the most flexibility with regard to interface. They will have multiple LANs and WANs Switches often have configurations that provide for a higher speed uplink port. ...
Workware Technical Manual
... A Windows or Mac based application installation package can be downloaded from the module. This package can also be configured to automatically connect to the module form which it is downloaded. Once the desired options are selected, press the “Download Client” button to retrieve the installation fi ...
... A Windows or Mac based application installation package can be downloaded from the module. This package can also be configured to automatically connect to the module form which it is downloaded. Once the desired options are selected, press the “Download Client” button to retrieve the installation fi ...
00197r3P802-15_TG3-LCW-HRWPAN-PHY-MAC
... • Basic MAC protocol remains DCF, or CSMA/CA with “Enhanced ACK” (EACK) and retransmission using “Enhanced ARQ” (EARQ) • EARQ provides for retransmission of only those RS blocks received with uncorrectable errors • EACK indicates the specific RS blocks to be retransmitted. • Optional PCF protocol us ...
... • Basic MAC protocol remains DCF, or CSMA/CA with “Enhanced ACK” (EACK) and retransmission using “Enhanced ARQ” (EARQ) • EARQ provides for retransmission of only those RS blocks received with uncorrectable errors • EACK indicates the specific RS blocks to be retransmitted. • Optional PCF protocol us ...
Asynchronous Transfer Mode (ATM)
... • AAL Type 1 supports constant bit rate (CBR), synchronous, connection oriented traffic. Examples include T1 (DS1), E1, and x64 kbit/s emulation. • AAL Type 2 supports time-dependent Variable Bit Rate (VBR-RT) of connection-oriented, synchronous traffic. Examples include Voice over ATM. AAL2 is also ...
... • AAL Type 1 supports constant bit rate (CBR), synchronous, connection oriented traffic. Examples include T1 (DS1), E1, and x64 kbit/s emulation. • AAL Type 2 supports time-dependent Variable Bit Rate (VBR-RT) of connection-oriented, synchronous traffic. Examples include Voice over ATM. AAL2 is also ...
ComCom04-1 - Raouf Boutaba
... queuing elements [1]. Combining these elements into higher-level blocks creates a Traffic Condition Block (TCB), which can be configured through PBN. This involves the use of administratively prescribed policies that specify what actions should be executed in response to predefined events. Some of t ...
... queuing elements [1]. Combining these elements into higher-level blocks creates a Traffic Condition Block (TCB), which can be configured through PBN. This involves the use of administratively prescribed policies that specify what actions should be executed in response to predefined events. Some of t ...
SK-NET FDDI
... imply that SK intends to make these available in all countries in which SK operates. Any reference to an SK product, program, or service is not intended to state or imply that only SK's product, program, or service may be used. Any functionally equivalent product, program, or service that does not i ...
... imply that SK intends to make these available in all countries in which SK operates. Any reference to an SK product, program, or service is not intended to state or imply that only SK's product, program, or service may be used. Any functionally equivalent product, program, or service that does not i ...
Link-State Routing Protocols
... – Routers 1ST learn of directly connected networks – Routers then say “hello” to neighbors – Routers then build link state packets – Routers then flood LSPs to all neighbors – Routers use LSP database to build a network topology map & calculate the best path to each destination ...
... – Routers 1ST learn of directly connected networks – Routers then say “hello” to neighbors – Routers then build link state packets – Routers then flood LSPs to all neighbors – Routers use LSP database to build a network topology map & calculate the best path to each destination ...
3rd Edition, Chapter 5
... 7 bytes with pattern 10101010 followed by one byte with pattern 10101011 used to synchronize receiver, sender clock rates ...
... 7 bytes with pattern 10101010 followed by one byte with pattern 10101011 used to synchronize receiver, sender clock rates ...
Express Cube Topologies for On
... A recently proposed topology called the flattened butterfly maps a richly connected butterfly network onto a twodimensional substrate using a two-level hierarchical organization [10]. In the 64 node network, shown in Figure 1(b), the first level employs 4-way concentration to connect the processing ...
... A recently proposed topology called the flattened butterfly maps a richly connected butterfly network onto a twodimensional substrate using a two-level hierarchical organization [10]. In the 64 node network, shown in Figure 1(b), the first level employs 4-way concentration to connect the processing ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.