Telecommunications and Networking
... – "a group of interconnected computers, workstations, or computer devices (such as printers and data storage systems).” ...
... – "a group of interconnected computers, workstations, or computer devices (such as printers and data storage systems).” ...
TEHAMA COUNTY DEPARTMENT OF EDUCATION JOB
... Prioritize projects and services to minimize user interruptions and down time. Identify probable causes of networking problems as they arise. Install and configure network equipment. Employ a customer service approach and present information about technical issues clearly, both verbally and ...
... Prioritize projects and services to minimize user interruptions and down time. Identify probable causes of networking problems as they arise. Install and configure network equipment. Employ a customer service approach and present information about technical issues clearly, both verbally and ...
S3C2 – LAN Switching
... • Both bridges and switches connect LAN segments, use a table of MAC addresses to determine the segment on which a datagram needs to be transmitted, and reduce traffic. • Switches are more functional in today’s networks than bridges because they operate at much higher speeds than bridges and can sup ...
... • Both bridges and switches connect LAN segments, use a table of MAC addresses to determine the segment on which a datagram needs to be transmitted, and reduce traffic. • Switches are more functional in today’s networks than bridges because they operate at much higher speeds than bridges and can sup ...
Computer Network
... – Transmission Media • the transmission media consists of the physical connections, that facilitate the transmission of signals, between nodes on a network ...
... – Transmission Media • the transmission media consists of the physical connections, that facilitate the transmission of signals, between nodes on a network ...
William Stallings Data and Computer Communications
... Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
... Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
IP address - DePaul University
... Web Sites • To publish a Web Site, a user must – Find a Web server, that is • Connected to the Internet at all times (not dial-up access) • Running web server software • Has disk space that can be used for storing files. ...
... Web Sites • To publish a Web Site, a user must – Find a Web server, that is • Connected to the Internet at all times (not dial-up access) • Running web server software • Has disk space that can be used for storing files. ...
Network Administrator - San Luis Obispo Superior Court
... implements, and maintains the Court’s data network which includes: local area and wide area network circuits, routers, servers and other equipment to meet departmental and courtwide requirements. Responsibilities of this position include the creation, administration and maintenance of standards and ...
... implements, and maintains the Court’s data network which includes: local area and wide area network circuits, routers, servers and other equipment to meet departmental and courtwide requirements. Responsibilities of this position include the creation, administration and maintenance of standards and ...
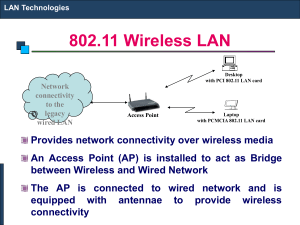
802.11 Wireless LAN
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
Sender Telephone, Computer, Video Conferencing Channel
... Network hub - a device that connects multiple computers into a network. Switch - a device that connects multiple computers into a network in which multiple communications links can be in operation ...
... Network hub - a device that connects multiple computers into a network. Switch - a device that connects multiple computers into a network in which multiple communications links can be in operation ...
Basic Networking Hardware
... A local area network that transmits over the air typically in an unlicensed frequency such as the 2.4GHz band. A wireless LAN does not require lining up devices for line of sight transmission. Wireless access points (base stations) are connected to an Ethernet hub or server and transmit a radio freq ...
... A local area network that transmits over the air typically in an unlicensed frequency such as the 2.4GHz band. A wireless LAN does not require lining up devices for line of sight transmission. Wireless access points (base stations) are connected to an Ethernet hub or server and transmit a radio freq ...
Study Guide - Csulb.edu
... Peer: Two separate computers or devices on a network that may both request and provide services to each other. ...
... Peer: Two separate computers or devices on a network that may both request and provide services to each other. ...
15 - MCCC Faculty Page
... someone registering a domain name may be liable to the owner of a trademark or to others that may be affected by the “bad faith” of the domain name registrant ...
... someone registering a domain name may be liable to the owner of a trademark or to others that may be affected by the “bad faith” of the domain name registrant ...
ppt
... Protocols Designed Based on Trust • That you don’t spoof your addresses – MAC spoofing, IP address spoofing, spam, … ...
... Protocols Designed Based on Trust • That you don’t spoof your addresses – MAC spoofing, IP address spoofing, spam, … ...
Assignment BTech 6_1
... of B, will C’s adapter process these frames? If so, will C’s adapter pass the IP datagrams in these ...
... of B, will C’s adapter process these frames? If so, will C’s adapter pass the IP datagrams in these ...
Communications and networking Early technology:
... • a LAN connects computers ("hosts") in a small geographical area • Ethernet is the most widely used LAN technology – developed by Bob Metcalfe & David Boggs at Xerox PARC, 1973 – each host has a unique 48-bit identification number – data sent from one host to another in "packets" of 100-1500 b ...
... • a LAN connects computers ("hosts") in a small geographical area • Ethernet is the most widely used LAN technology – developed by Bob Metcalfe & David Boggs at Xerox PARC, 1973 – each host has a unique 48-bit identification number – data sent from one host to another in "packets" of 100-1500 b ...
Introduction to HTML - Department of Computing and Software
... Wide Area Network (WAN): two or more local area networks connected with each other result in a wide area network. This also gives rise to the term inter-networking. Intranet: an Intranet is the name given to the use of Internet Technologies (e-mail, www) on private corporate networks whether they ar ...
... Wide Area Network (WAN): two or more local area networks connected with each other result in a wide area network. This also gives rise to the term inter-networking. Intranet: an Intranet is the name given to the use of Internet Technologies (e-mail, www) on private corporate networks whether they ar ...
Chapter 7 Packet-Switching Networks Chapter 7 Packet
... An end-to-end function is best implemented at a higher level than at a lower level z z ...
... An end-to-end function is best implemented at a higher level than at a lower level z z ...
Module 6 - ITE technical support
... Each network device is identified using a physical address. Ethernet networks use a MAC Address (physical device address) • The MAC address is a unique hexadecimal identifier burned into the ROM (physically assigned address) of every network interface. • When you change the network card, the host wi ...
... Each network device is identified using a physical address. Ethernet networks use a MAC Address (physical device address) • The MAC address is a unique hexadecimal identifier burned into the ROM (physically assigned address) of every network interface. • When you change the network card, the host wi ...
Wired and Wireless Network_L2_Teacher_Powerpoint
... • Identify the components required to create a LAN • Describe the role of each component in a LAN • Understand what is meant by the performance of a network and why this is important • Explain the factors that can affect the performance of a network ...
... • Identify the components required to create a LAN • Describe the role of each component in a LAN • Understand what is meant by the performance of a network and why this is important • Explain the factors that can affect the performance of a network ...
Pretest Answers
... local area network (LAN) card in the PC card slot, install card drivers, and use a network cable to attach to the network. e. Install network software written for the brand of notebook. 16. In which one of the following types of computers would you use a PC Card? a. Laptop b. Server c. Personal comp ...
... local area network (LAN) card in the PC card slot, install card drivers, and use a network cable to attach to the network. e. Install network software written for the brand of notebook. 16. In which one of the following types of computers would you use a PC Card? a. Laptop b. Server c. Personal comp ...
Westermo Group
... The DMZ acts a buffer between the trusted and un-trusted zones The DMZ prevents direct communication between the trusted and un-trusted zones. All communications from the un-trusted zone are terminated on an intermediate server or historian The DMZ can offer protection against cyber attacks such as ...
... The DMZ acts a buffer between the trusted and un-trusted zones The DMZ prevents direct communication between the trusted and un-trusted zones. All communications from the un-trusted zone are terminated on an intermediate server or historian The DMZ can offer protection against cyber attacks such as ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.