PPT
... ISO OSI Seven Layer Model Layer 7 Layer 6 Layer 5 Layer 4 Layer 3 Layer 2 Layer 1 ...
... ISO OSI Seven Layer Model Layer 7 Layer 6 Layer 5 Layer 4 Layer 3 Layer 2 Layer 1 ...
Powerpoint - Eve - Kean University
... The Token Ring network was originally developed by IBM. It is still IBM's primary local-area network (LA technology. Token-passing networks move a small command frame, called a token around the (circular r network. Possession of the token grants the possessor the right to transmit data. To transmit ...
... The Token Ring network was originally developed by IBM. It is still IBM's primary local-area network (LA technology. Token-passing networks move a small command frame, called a token around the (circular r network. Possession of the token grants the possessor the right to transmit data. To transmit ...
Slide 1
... The World Wide Web is a computer network consisting of a collection of internet sites that offer text, graphics, sound and animation resources through the hypertext transfer protocol. ...
... The World Wide Web is a computer network consisting of a collection of internet sites that offer text, graphics, sound and animation resources through the hypertext transfer protocol. ...
IP addresses
... Determines the format in which to represent the data. Possible choices are EBCDIC or ASCII format. ...
... Determines the format in which to represent the data. Possible choices are EBCDIC or ASCII format. ...
T - Intel
... Any intermediate node in a multi-hop wireless network can operate as a router wide-applicability for a packet forwarding architecture ...
... Any intermediate node in a multi-hop wireless network can operate as a router wide-applicability for a packet forwarding architecture ...
PPT - Winlab
... Any intermediate node in a multi-hop wireless network can operate as a router wide-applicability for a packet forwarding architecture ...
... Any intermediate node in a multi-hop wireless network can operate as a router wide-applicability for a packet forwarding architecture ...
知识管理的IT实现 IBM知识管理解决方案
... used to connect different types of cable,or physical topologies. They must,however,be used between networks with the same protocol. Bridges are store-and-forward devices. A bridge accepts an entire frame and passes it up to the data link layer where the checksum is verified. Then the frame is sent d ...
... used to connect different types of cable,or physical topologies. They must,however,be used between networks with the same protocol. Bridges are store-and-forward devices. A bridge accepts an entire frame and passes it up to the data link layer where the checksum is verified. Then the frame is sent d ...
network cards
... – only allows valid users to log on – only allows access to resources for users that have logged on – stores appropriate “user rights” for access to its files and directories ...
... – only allows valid users to log on – only allows access to resources for users that have logged on – stores appropriate “user rights” for access to its files and directories ...
Additional Voltages Available 2-year Extended Warranty Main Input
... is a web enabled monitoring device for a unit with Internet or LAN connection. The internal IP internet address can be pre-installed in firmware to fit customer network settings. The NetAgent can monitor the UPS on the network through a standard web browser. A Network Management System software with ...
... is a web enabled monitoring device for a unit with Internet or LAN connection. The internal IP internet address can be pre-installed in firmware to fit customer network settings. The NetAgent can monitor the UPS on the network through a standard web browser. A Network Management System software with ...
NET331_Ch8+Ch20
... IPv4 is also a connectionless protocol for a packet switching network that uses the datagram approach. This means that each datagram is handled independently, and each datagram can follow a different route to the destination. This implies that datagrams sent by the same source to the same destinatio ...
... IPv4 is also a connectionless protocol for a packet switching network that uses the datagram approach. This means that each datagram is handled independently, and each datagram can follow a different route to the destination. This implies that datagrams sent by the same source to the same destinatio ...
Connected Devices Interfacing (CDI)
... Network Information and Control (NetIC) Generic Enabler will provide to FI-WARE chapters as well as Usage Area applications and services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of t ...
... Network Information and Control (NetIC) Generic Enabler will provide to FI-WARE chapters as well as Usage Area applications and services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of t ...
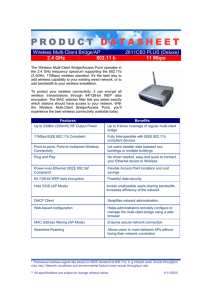
Wireless Multi-Client Bridge/AP 2611CB3 PLUS (Deluxe) 2.4 GHz
... Power-over-Ethernet (IEEE 802.3af Compliant) ...
... Power-over-Ethernet (IEEE 802.3af Compliant) ...
2. Internet Communication Diagram
... Proxy server – This is a server that all computers on the local network have to go through before accessing information on the Internet. By using a proxy server you can filter what users connected to the network can access – it is also help speed up browsing by caching site data I want to access the ...
... Proxy server – This is a server that all computers on the local network have to go through before accessing information on the Internet. By using a proxy server you can filter what users connected to the network can access – it is also help speed up browsing by caching site data I want to access the ...
ppt - Carnegie Mellon School of Computer Science
... – Link must support 1280 bytes; – 1500 bytes if link supports variable sizes ...
... – Link must support 1280 bytes; – 1500 bytes if link supports variable sizes ...
Programming the IBM Power3 SP
... – enable grid and network researchers to test and evaluate new protocols with actual traffic demands of applications rather than modulated demands • Multiclass service inference – enable network clients to assess a system's multi-class mechanisms and parameters using only passive, external observati ...
... – enable grid and network researchers to test and evaluate new protocols with actual traffic demands of applications rather than modulated demands • Multiclass service inference – enable network clients to assess a system's multi-class mechanisms and parameters using only passive, external observati ...
Tesla - Nick Giannaris
... Direct: Two devices communicate directly. Full addressing is required. Group: Application assigns a group membership to one or more devices Broadcast: Used to send a packet to all devices simultaneously ...
... Direct: Two devices communicate directly. Full addressing is required. Group: Application assigns a group membership to one or more devices Broadcast: Used to send a packet to all devices simultaneously ...
lecture 1 - CUNY Home
... Gigabit Ethernet deployment: institutions, home LANs happening now Lecture 1 ...
... Gigabit Ethernet deployment: institutions, home LANs happening now Lecture 1 ...
Networking and Security Handout
... network adapters to the nodes that will make up the network. If the nodes are unable to communicate because of distance, then you can add a wireless access point to the network to help relay data between nodes. Wireless networks are susceptible to interference from other wireless devices such as pho ...
... network adapters to the nodes that will make up the network. If the nodes are unable to communicate because of distance, then you can add a wireless access point to the network to help relay data between nodes. Wireless networks are susceptible to interference from other wireless devices such as pho ...
“Fig 1.5” – An internet
... at source, data divided into packets packets individually sent from source to destination data reassembled at destination ...
... at source, data divided into packets packets individually sent from source to destination data reassembled at destination ...
Chapter6.5
... protocols for connection-oriented networks • Key assumption: do not detract from robustness of connectionless network – Lack of router state in connectionless allows for end-toend connectivity even during crash and reboot cycles – RSVP uses soft state: does not need to be explicitly deleted when no ...
... protocols for connection-oriented networks • Key assumption: do not detract from robustness of connectionless network – Lack of router state in connectionless allows for end-toend connectivity even during crash and reboot cycles – RSVP uses soft state: does not need to be explicitly deleted when no ...
The Network Layer
... Architectural model of IP where each IP is identified by a single machine Internet from connection-less to connection-oriented NAT violates the most fundamental rule of protocol layering Processes on the Internet are not required to use TCP or UDP Some application insert IP address in their body – ( ...
... Architectural model of IP where each IP is identified by a single machine Internet from connection-less to connection-oriented NAT violates the most fundamental rule of protocol layering Processes on the Internet are not required to use TCP or UDP Some application insert IP address in their body – ( ...
eHealth Network Monitoring
... resources are at risk of failure Manage servers supporting network services, such as firewalls, DNS, and DHCP servers, on Windows and UNIX platforms Perform continuous, active tests of application availability and functionality ...
... resources are at risk of failure Manage servers supporting network services, such as firewalls, DNS, and DHCP servers, on Windows and UNIX platforms Perform continuous, active tests of application availability and functionality ...
SOFTWARE DEFINED NETWORKING
... The increasing adoption of SDN and NFV technologies have driven the need to test their efficiency. The Celemetrix SDN practice enables enterprises, service providers and government agencies to validate their SDN and NFV implementation and deploy with confidence. Our experience consultants can help a ...
... The increasing adoption of SDN and NFV technologies have driven the need to test their efficiency. The Celemetrix SDN practice enables enterprises, service providers and government agencies to validate their SDN and NFV implementation and deploy with confidence. Our experience consultants can help a ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.