Optical Burst Switching Obs.doc
... – Relates to the capability of making connections. – A blocking network is one in which blocking is possible. – A nonblocking network permits all stations to be connected (in pairs) as long as the stations are not in use. ...
... – Relates to the capability of making connections. – A blocking network is one in which blocking is possible. – A nonblocking network permits all stations to be connected (in pairs) as long as the stations are not in use. ...
Network - UniMAP Portal
... • Internet evolved from ARPANET – first operational packet network – applied to tactical radio & satellite nets also – had a need for interoperability – lead to standardized TCP/IP protocols ...
... • Internet evolved from ARPANET – first operational packet network – applied to tactical radio & satellite nets also – had a need for interoperability – lead to standardized TCP/IP protocols ...
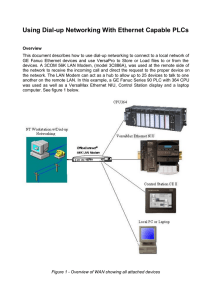
Using Dial-up Networking With Ethernet Capable PLCs
... up to answer an incoming call. You must go into the configuration for the modem and set it to answer after so many rings. In this case, the modem was set to answer after the first ring. Setting this to a higher number of rings will give you time to answer an incoming voice call, if so desired, befor ...
... up to answer an incoming call. You must go into the configuration for the modem and set it to answer after so many rings. In this case, the modem was set to answer after the first ring. Setting this to a higher number of rings will give you time to answer an incoming voice call, if so desired, befor ...
TCP_IP_Continued
... TCP Port Number Conventions • TCP Port Numbers are in the range 0 – 65535 • Ports 0 – 1023 are reserved for system services (email, web, etc.) • Ports 1024 – 49151 are registered to particular applications • Ports 49152 – 65535 can be used for custom or temporary purposes • Email servers typically ...
... TCP Port Number Conventions • TCP Port Numbers are in the range 0 – 65535 • Ports 0 – 1023 are reserved for system services (email, web, etc.) • Ports 1024 – 49151 are registered to particular applications • Ports 49152 – 65535 can be used for custom or temporary purposes • Email servers typically ...
Packet Tracer – Investigating Convergence (Instructor Version)
... Are the IP addresses in the configuration advertised by RIP the same as those that are connected? Yes ...
... Are the IP addresses in the configuration advertised by RIP the same as those that are connected? Yes ...
Networking and communication
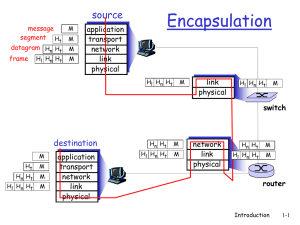
... transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, which gets sent to the link layer The link layer appe ...
... transport layer The OS adds a TCP header that identify the source and destination ports, forming a TCP segment, and sends that to the network layer In the network layer, an IP header identifying the source and destination systems are added, which gets sent to the link layer The link layer appe ...
LOCATING THE WISECRACKERS USING SPOOFER
... Trace back with Cumulative Path (I Trace-CP). It is often useful to learn the path that packets take through the Internet. This is especially important for dealing with certain denial-of- ...
... Trace back with Cumulative Path (I Trace-CP). It is often useful to learn the path that packets take through the Internet. This is especially important for dealing with certain denial-of- ...
CS 432 Computer Networks - Rose
... the duration of the communication session breaking large packets into smaller segments in order to pass them onto another network decreasing transmission rate quickly (halving it) when congestion is observed distributed database of mapping between host names and IP numbers a mechanism to prevent eit ...
... the duration of the communication session breaking large packets into smaller segments in order to pass them onto another network decreasing transmission rate quickly (halving it) when congestion is observed distributed database of mapping between host names and IP numbers a mechanism to prevent eit ...
Turkish lottery agents move to 3G wireless mobile
... RICON 3G routers are connected to the GTech lottery terminals with via a 9 pin serial port interface. The antenna used in RICON 3G wireless mobile router was able to be placed externally for optimal maximum signal strength. The routers dual SIM’s are securely protected within the router making the d ...
... RICON 3G routers are connected to the GTech lottery terminals with via a 9 pin serial port interface. The antenna used in RICON 3G wireless mobile router was able to be placed externally for optimal maximum signal strength. The routers dual SIM’s are securely protected within the router making the d ...
Chapter 1 An Introduction to Networking
... connected by routers. • Routers forwards packets from one to another following a route from the sender to the receiver. Store-and-Forward • Hosts are typically connected (or close to) the routers ...
... connected by routers. • Routers forwards packets from one to another following a route from the sender to the receiver. Store-and-Forward • Hosts are typically connected (or close to) the routers ...
ppt
... • Examine switch port configurations and other switch information. • Users can only change devices/ports for which they are authorized. ...
... • Examine switch port configurations and other switch information. • Users can only change devices/ports for which they are authorized. ...
Basic Networking
... file-sharing controls via the computer’s operating system. 2. Resource sharing is controlled by a central computer or authority. 3. Clients on a client/server network share their resources directly with each other. 4. Networks are usually only arranged in a ring, bus, or star formation and hybrid co ...
... file-sharing controls via the computer’s operating system. 2. Resource sharing is controlled by a central computer or authority. 3. Clients on a client/server network share their resources directly with each other. 4. Networks are usually only arranged in a ring, bus, or star formation and hybrid co ...
Introduction to TCP/IP networking
... – Interface presented to the application doesn’t require data in individual packets – Data is guaranteed to arrive, and in the correct order without duplications • Or the connection will be dropped ...
... – Interface presented to the application doesn’t require data in individual packets – Data is guaranteed to arrive, and in the correct order without duplications • Or the connection will be dropped ...
Powerpoint
... router fails to forward, or corrupts packets router runs out of memory, calculates wrong with large subnets, becomes probable ...
... router fails to forward, or corrupts packets router runs out of memory, calculates wrong with large subnets, becomes probable ...
COS 461: Computer Networks Spring 2009 (MW 1:30‐2:50 in CS 105) Mike Freedman Teaching Assistants: WyaI Lloyd and Jeff Terrace
... Programming in an individual creaWve process much like composiWon. You must reach your own understanding of the problem and discover a path to its soluWon. During this Wme, discussions with friends are encouraged. However, when the Wme comes to write code that solves the problem, such discussio ...
... Programming in an individual creaWve process much like composiWon. You must reach your own understanding of the problem and discover a path to its soluWon. During this Wme, discussions with friends are encouraged. However, when the Wme comes to write code that solves the problem, such discussio ...
Operating System Current Version Policy
... Operating System Current Version Policy Purpose To ensure secure and supportable operating system software on all Auburn University computers Policy All Auburn University computers will run only current edition operating system software that is fully supported by their vendors or the open source com ...
... Operating System Current Version Policy Purpose To ensure secure and supportable operating system software on all Auburn University computers Policy All Auburn University computers will run only current edition operating system software that is fully supported by their vendors or the open source com ...
28-roundup
... • (2) Data link: flow control, framing, error detection. • (3) Network: switching and routing. • (4) Transport: reliable end to end delivery. ...
... • (2) Data link: flow control, framing, error detection. • (3) Network: switching and routing. • (4) Transport: reliable end to end delivery. ...
Intro To Networking Part B Chapter 3
... –Improve security by housing equipment outside of the normal ...
... –Improve security by housing equipment outside of the normal ...
ROB: Route Optimization Assisted by BGP
... – the upper routers, in the nested mobile network, are • aware of the network prefix information of lower routers and • designed to send them to their ORC (proxy) routers. – modifies the route advertisement (RA) message » fixed routers should be also modified ...
... – the upper routers, in the nested mobile network, are • aware of the network prefix information of lower routers and • designed to send them to their ORC (proxy) routers. – modifies the route advertisement (RA) message » fixed routers should be also modified ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.